When should an engineer implement a collapsed-core architecture?
Which type of IPv4 address must be assigned to a server to protect it from external access and allow only internal users access while restricting internet access?
Which signal frequency appears 60 times per minute?
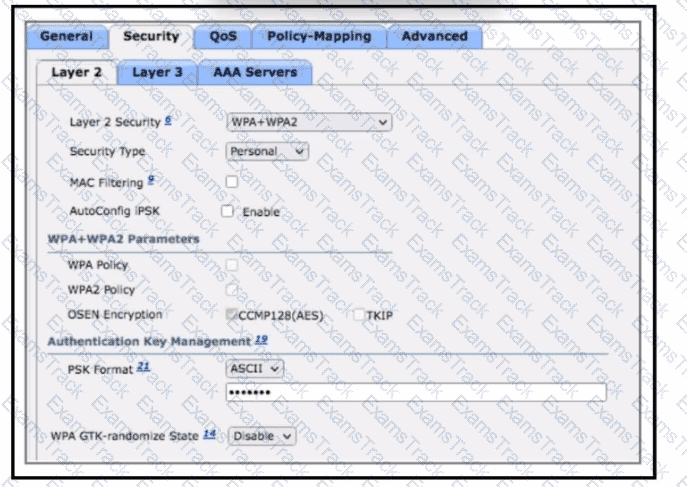
Refer to the exhibit. Company A wants to use a RADIUS server to service all user and device authentication attempts with a more secure and granular authentication approach. Not all client devices support dot1x authentication. Which two configuration changes must be made to accomplish the task? (Choose two.)
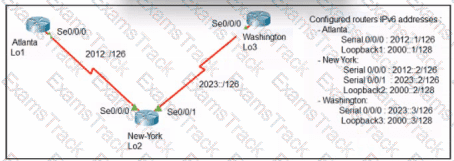
Refer to the exhibit. An engineer configured the New York router with static routes that point to the Atlanta and Washington sites. Which command must be configured on the Atlanta and Washington routers so that both sites are able to reach the Lo2 interface on the New York router?
Refer to the exhibit.
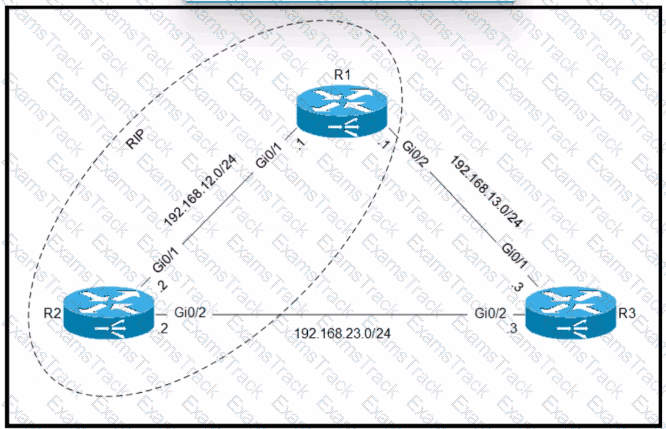
Routers R1 and R2 are configured with RIP as the dynamic routing protocol. A network engineer must configure R1 with a floating static route to serve as a backup route to network 192.168.23. Which command must the engineer configure on R1?
What must be considered before deploying virtual machines?
A router has two static routes to the same destination network under the same OSPF process. How does the router forward packets to the destination if the next-hop devices are different?
Refer to the exhibit.
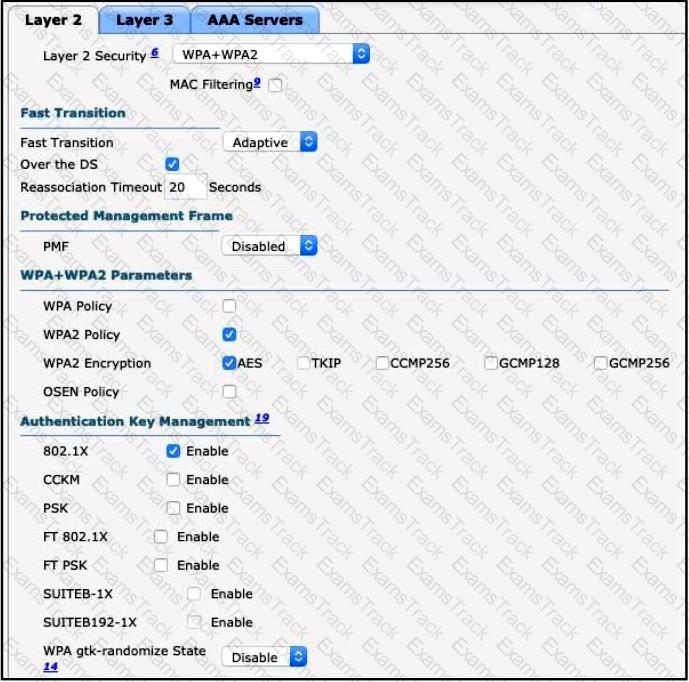
Clients on the WLAN are required to use 802.11r. What action must be taken to meet the requirement?
|
PDF + Testing Engine
|
|---|
|
$52.5 |
|
Testing Engine
|
|---|
|
$40.5 |
|
PDF (Q&A)
|
|---|
|
$34.5 |
Cisco Free Exams |
|---|

|