Which action implements physical access control as part of the security program of an organization?
Which Layer 2 switch function encapsulates packets for different VLANs so that the packets traverse the same port and maintain traffic separation between the VLANs?
Refer to the exhibit.
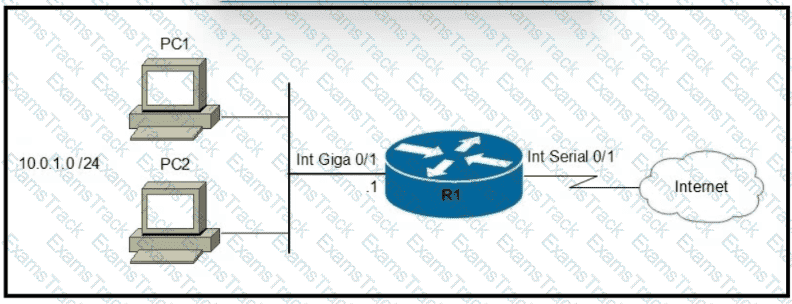
Which two commands must be configured on router R1 to enable the router to accept secure remote-access connections? (Choose two)
Refer to the exhibit.
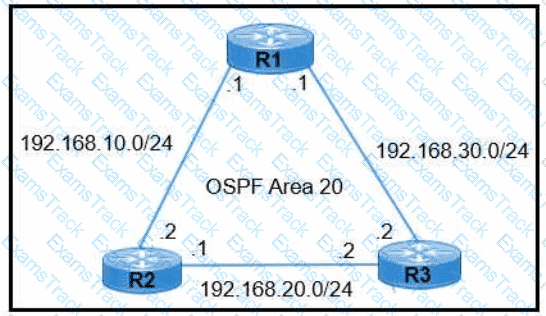
R1 learns all routes via OSPF Which command configures a backup static route on R1 to reach the 192 168.20.0/24 network via R3?
Refer to the exhibit.
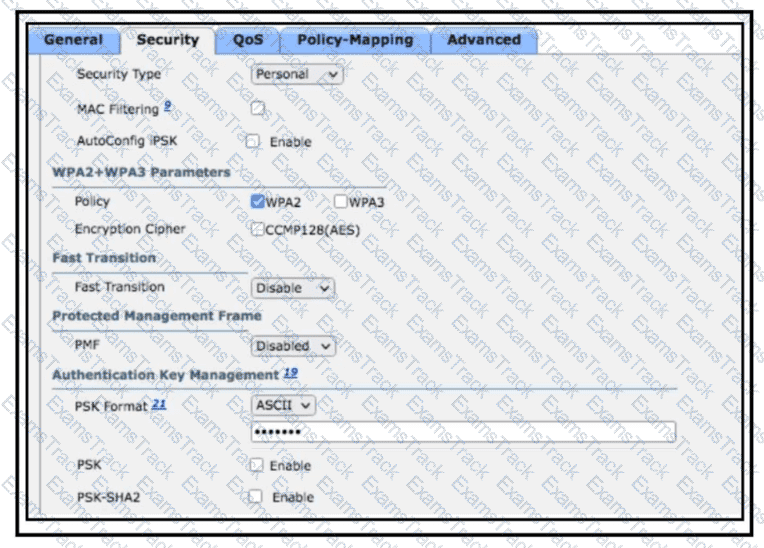
Users will be using a preconfigured secret key and SSID and must have a secured key hashing algorithm configured. The AAA server must not be used for the user authentication method. Which action completes the task?
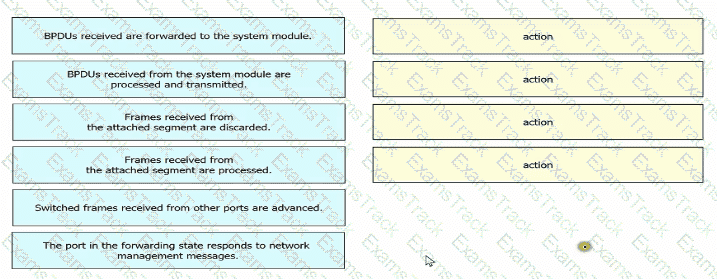
Drag and drop the Rapid PVST+ forwarding slate actions from the loft to the right. Not all actions are used.
Which action is taken by the data plane within a network device?
Refer to the exhibit.
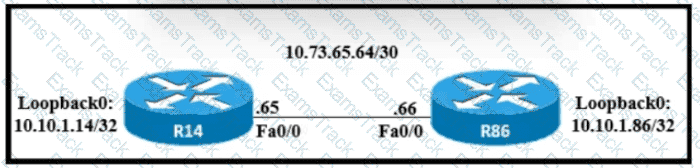
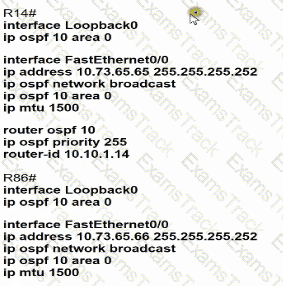
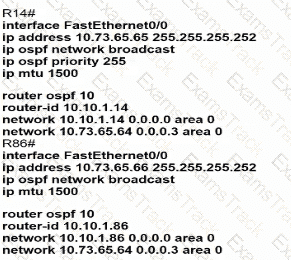
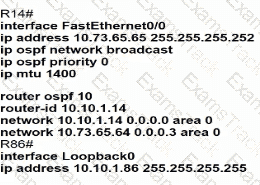
A static route must be configured on R14 to forward traffic for the 172 21 34 0/25 network that resides on R86 Which command must be used to fulfill the request?
What is a requirement for nonoverlapping Wi-Fi channels?
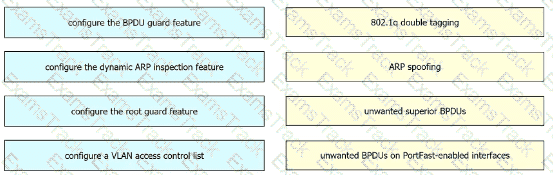
Drag and drop the threat-mitigation techniques from the left onto the types of threat or attack they mitigate on the right.
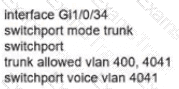
Refer to the exhibit.
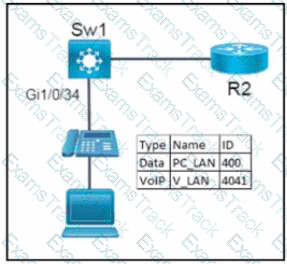
Network services must be enabled on interface Gil/0734. Which configuration meets the needs for this implementation?
A)
B)
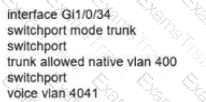
C)
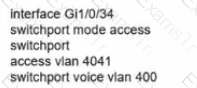
D)
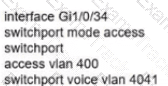
Refer to the exhibit.
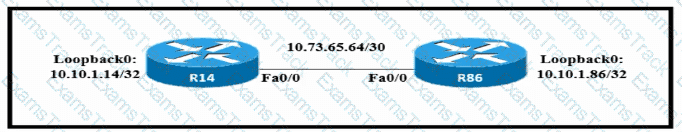
Which configuration allows routers R14 and R86 to form an OSPFv2 adjacency while acting as a central point for exchanging OSPF information between routers?
A)
B)
C)
D)
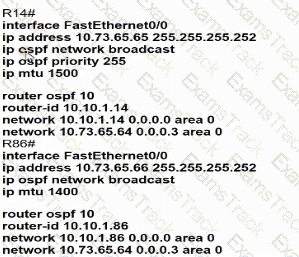
Refer to the exhibit.
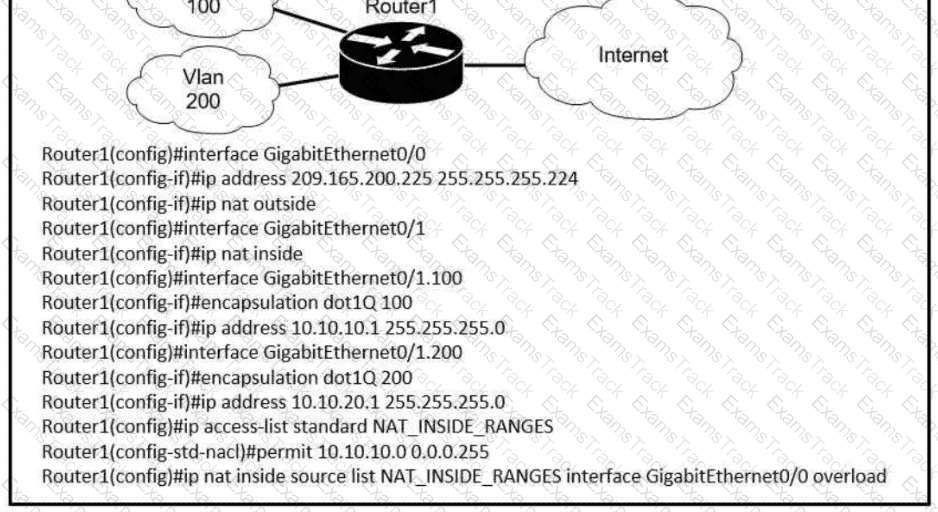
Users on existing VLAN 100 can reach sites on the Internet. Which action must the administrator take to establish connectivity to the Internet for users in VLAN 200?
Refer to the exhibit.
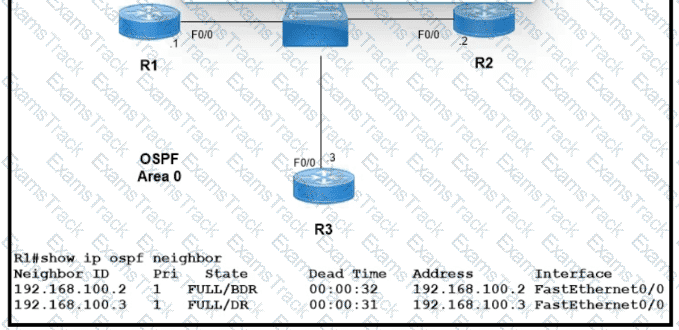
Which two configurations must the engineer apply on this network so that R1 becomes the DR? (Choose two.)
A)

B)

C)
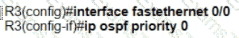
D)

E)

Which interface mode must be configured to connect the lightweight APs in a centralized architecture?
A network engineer must configure two new subnets using the address block 10 70 128 0/19 to meet these requirements:
• The first subnet must support 24 hosts
• The second subnet must support 472 hosts
• Both subnets must use the longest subnet mask possible from the address block
Which two configurations must be used to configure the new subnets and meet a requirement to use the first available address in each subnet for the router interfaces? (Choose two )
Refer to the exhibit.
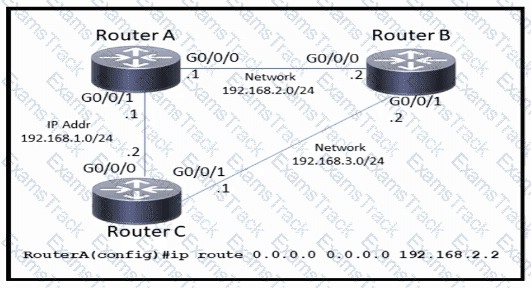
Which command must be issued to enable a floating static default route on router A?
Refer to the exhibit.
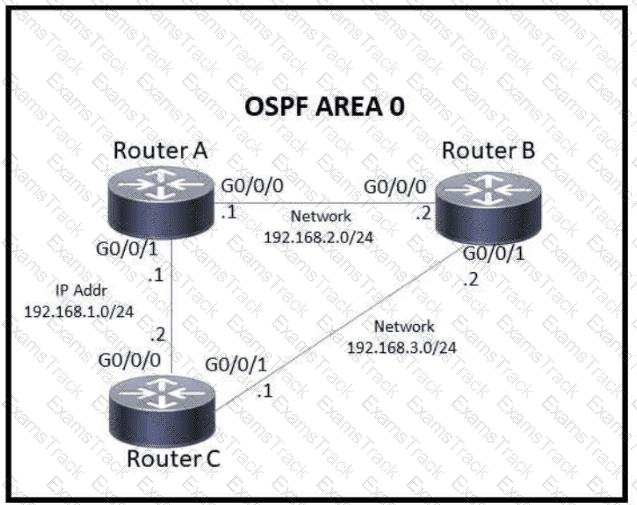
Which action must be taken to ensure that router A is elected as the DR for OSPF area 0?
Refer to the exhibit.
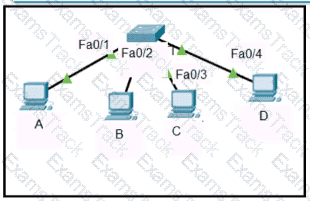
Host A sent a data frame destined for host D
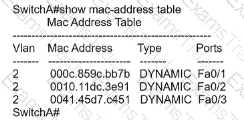
What does the switch do when it receives the frame from host A?
Refer to the exhibit.
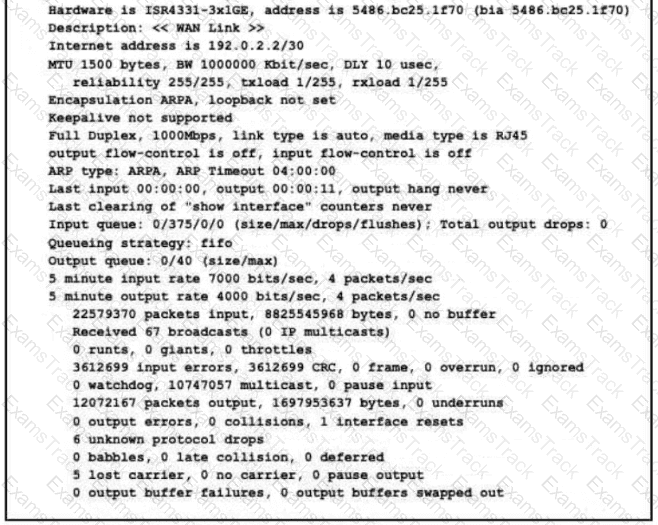
What is a reason for poor performance on the network interface?
What is one reason to implement LAG on a Cisco WLC?
Refer to the exhibit.

A network engineer must update the configuration on Switch2 so that it sends LLDP packets every minute and the information sent via LLDP is refreshed every 3 minutes Which configuration must the engineer apply?
A)

B)
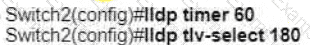
C)
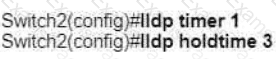
D)
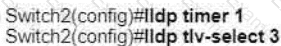
A Cisco engineer must configure a single switch interface to meet these requirements
• accept untagged frames and place them in VLAN 20
• accept tagged frames in VLAN 30 when CDP detects a Cisco IP phone
Which command set must the engineer apply?
A)

B)

C)

D)

Refer to the exhibit.
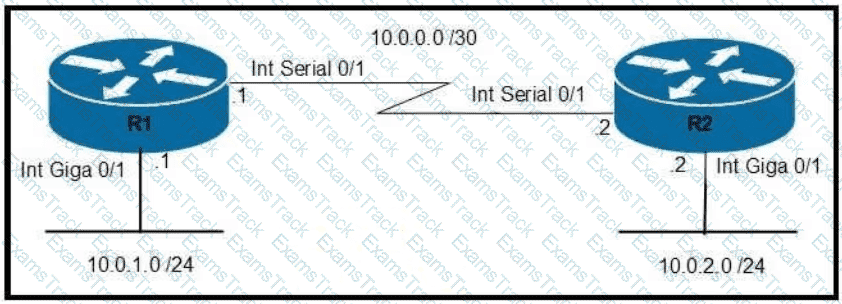
Which command configures OSPF on the point-to-point link between routers R1 and R2?
Which wireless security protocol relies on Perfect Forward Secrecy?
A network engineer must implement an IPv6 configuration on the vlan 2000 interface to create a routable locally-unique unicast address that is blocked from being advertised to the internet. Which configuration must the engineer apply?
What is a function of TFTP in network operations?
Refer to the exhibit.
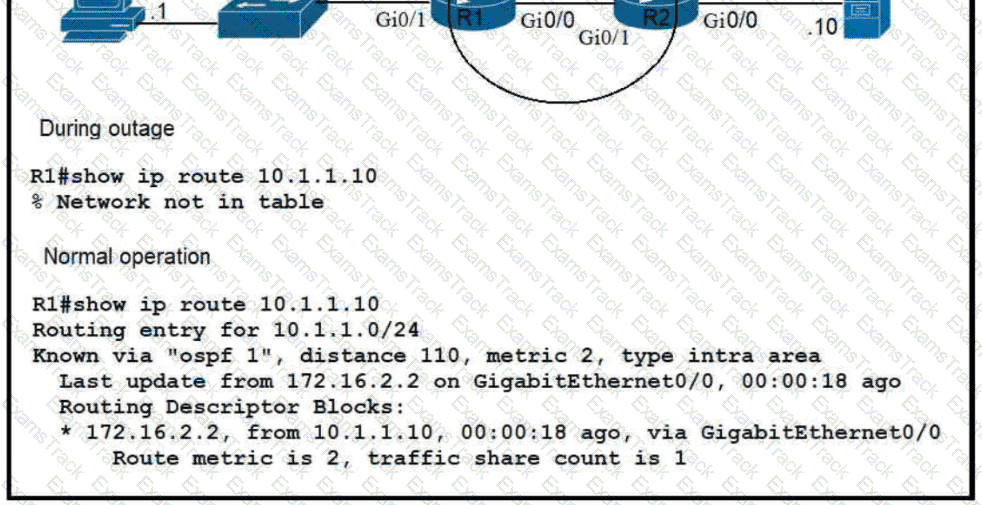
Which route must be configured on R1 so that OSPF routing is used when OSPF is up. but the server is still reachable when OSPF goes down?
Refer to the exhibit.
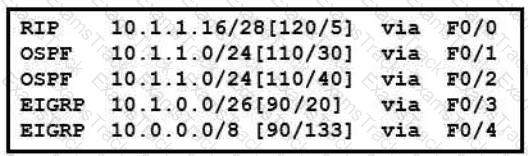
Packets received by the router from BGP enter via a serial interface at 209 165 201 1 Each route is present within the routing table Which interface is used to forward traffic with a destination IP of 10.1.1.19?
A network engineer is configuring a switch so that it is remotely reachable via SSH. The engineer has already configured the host name on the router. Which additional command must the engineer configure before entering the command to generate the RSA key?
What causes a port to be placed in the err-disabled state?
What is an expected outcome when network management automation is deployed?
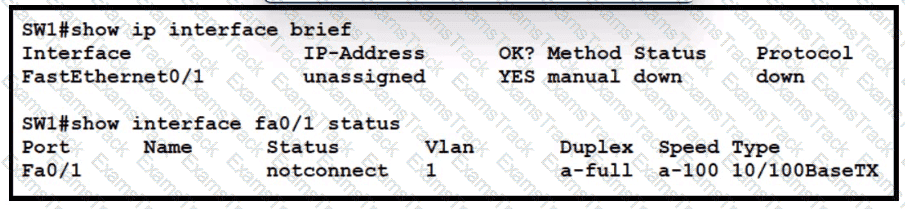
Refer to the exhibit. What is the cause of the issue?
Refer to the exhibit.
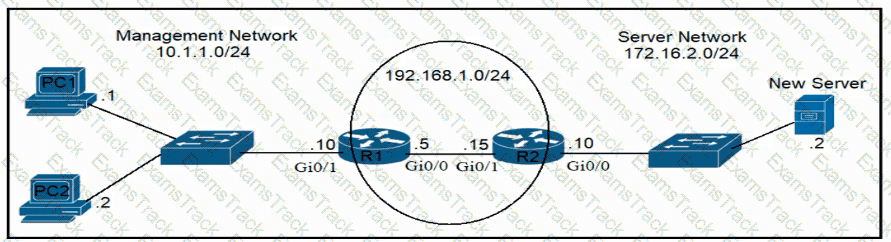
An engineer is updating the R1 configuration to connect a new server to the management network. The PCs on the management network must be blocked from pinging the default gateway of the new server. Which command must be configured on R1 to complete the task?
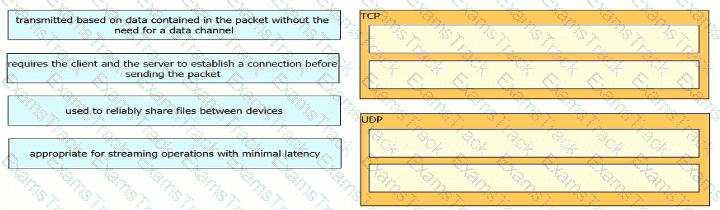
Drag and drop the TCP or UDP details from the left onto their corresponding protocols on the right.
Refer to the exhibit.
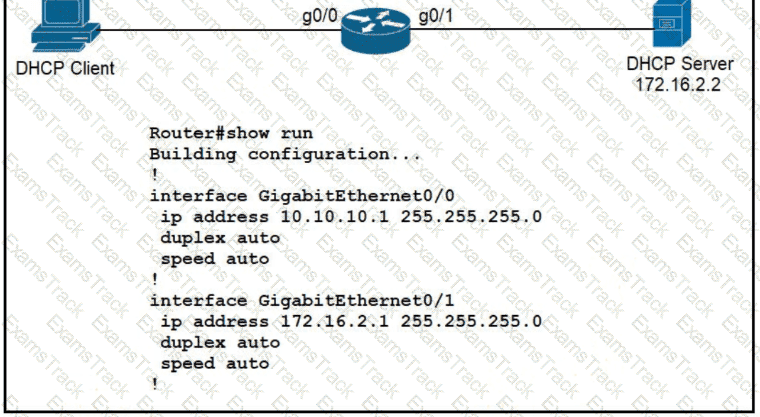
An engineer is configuring a new router on the network and applied this configuration. Which additional configuration allows the PC to obtain its IP address from a DHCP server?
A router received three destination prefixes:10.0.0/18, and 10.0.0/24. When the show ip route command is executed, which output does it return?
A)
B)
C)
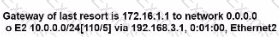
D)

Drag and drop the facts about wireless architectures from the left onto the types of access point on the right. Not all options are used.
Which WLC management connection type is vulnerable to man-in-the-middle attacks?
What is a function of a Next-Generation IPS?
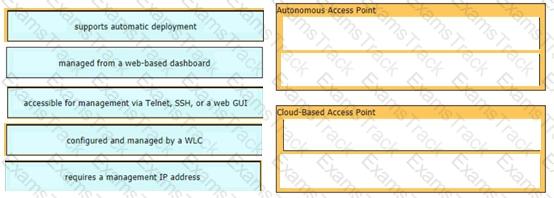
Drag and drop the characteristics of networking from the left onto the networking types on the right.
Refer to the exhibit.
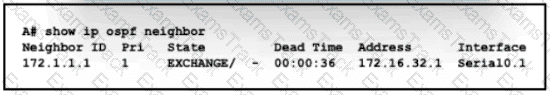
An engineer assumes a configuration task from a peer Router A must establish an OSPF neighbor relationship with neighbor 172 1 1 1 The output displays the status of the adjacency after 2 hours. What is the next step in the configuration process for the routers to establish an adjacency?
Refer to the exhibit.
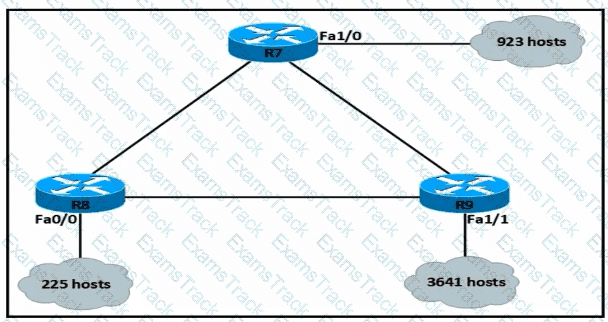
An IP subnet must be configured on each router that provides enough addresses for the number of assigned hosts and anticipates no more than 10% growth for now hosts. Which configuration script must be used?
A)
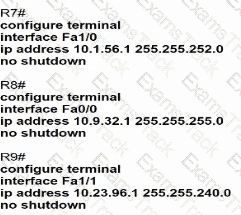
B)
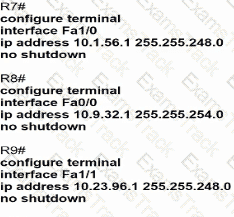
C)
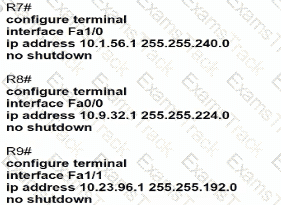
D)
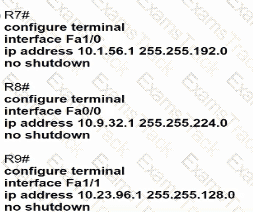
Refer to the exhibit.
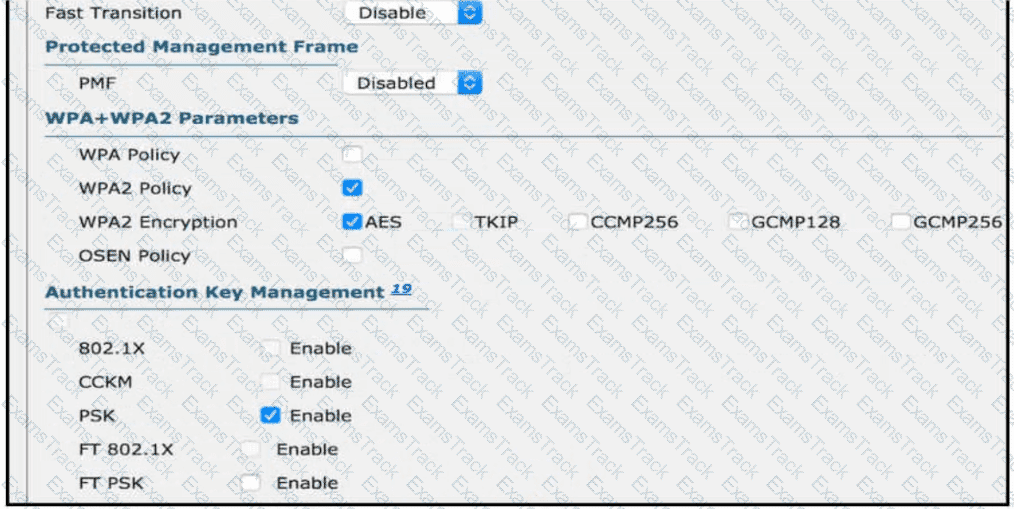
Users need to connect to the wireless network with IEEE 802. 11r-compatible devices. The connection must be maintained as users travel between floors or to other areas in the building What must be the configuration of the connection?
Which protocol uses the SSL?
Refer to the exhibit.

Packets received by the router from BGP enter via a serial interface at 209.165.201.10. Each route is present within the routing table. Which interface is used to forward traffic with a destination IP of 10.10.10.24?
Refer to the exhibit.
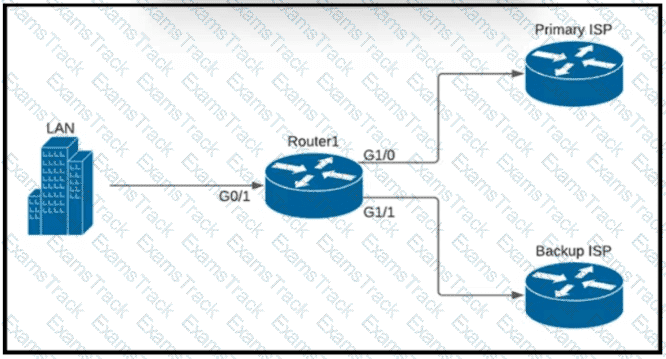
A company is configuring a failover plan and must implement the default routes in such a way that a floating static route will assume traffic forwarding when the primary link goes down. Which primary route configuration must be used?
Refer to the exhibit.
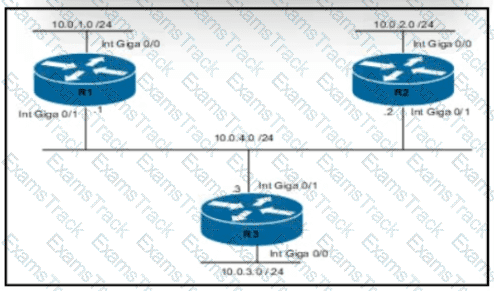
Routers R1 and R3 have the default configuration The router R2 priority is set to 99 Which commands on R3 configure it as the DR in the 10.0 4.0/24 network?
Refer to the exhibit.
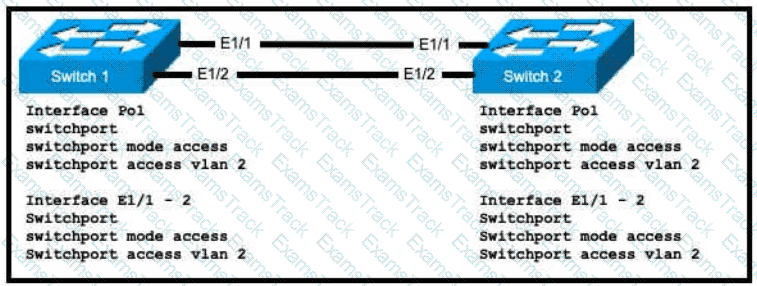
An engineer is configuring an EtherChannel using LACP between Switches 1 and 2 Which configuration must be applied so that only Switch 1 sends LACP initiation packets?
How does Rapid PVST+ create a fast loop-free network topology?
|
PDF + Testing Engine
|
|---|
|
$52.5 |
|
Testing Engine
|
|---|
|
$40.5 |
|
PDF (Q&A)
|
|---|
|
$34.5 |
Cisco Free Exams |
|---|

|