Which WAN topology has the highest degree of reliability?
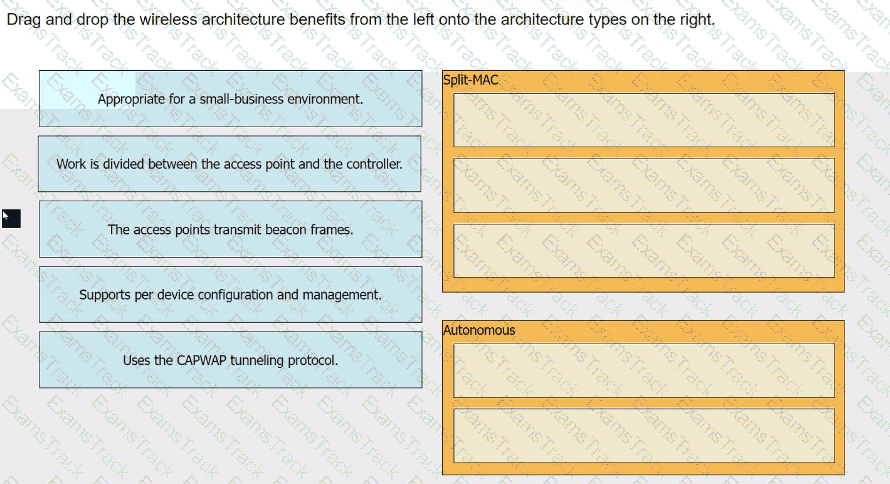
Drag and drop the wireless architecture benefits from the left onto the architecture types on the right.
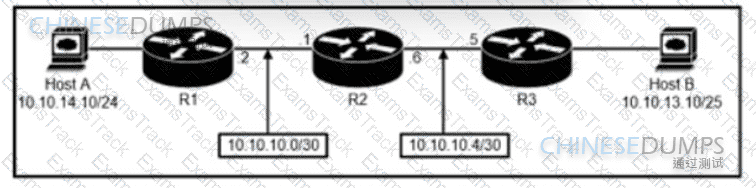
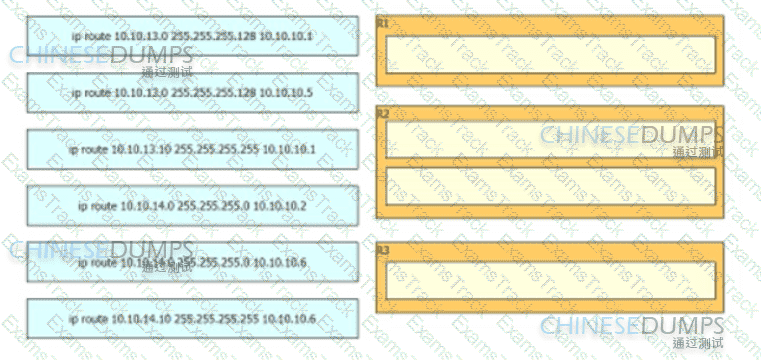
Refer to the exhibit. An engineer must configure a static network route between two networks so that host A communicates with host B. Drag and drop the commands from the left onto the routers where they must be configured on the right. Not all commands are used.
Refer to the exhibit.
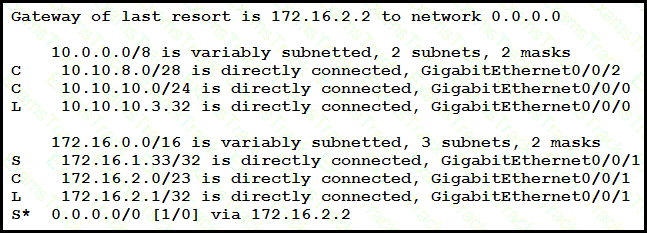
A packet sourced from 10.10.10.1 is destined for 10.10.8.14. What is the subnet mask of the destination route?
What is a characteristic of RSA?
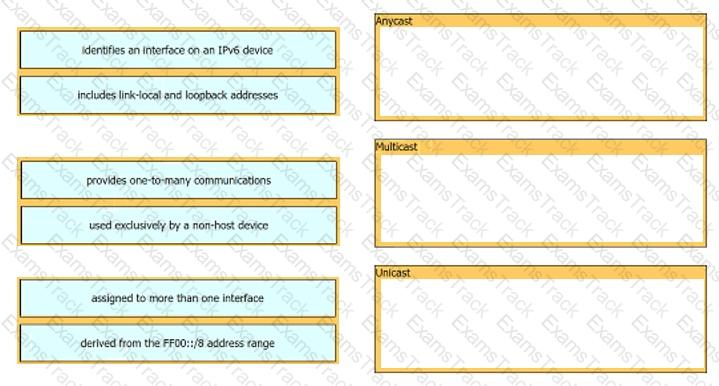
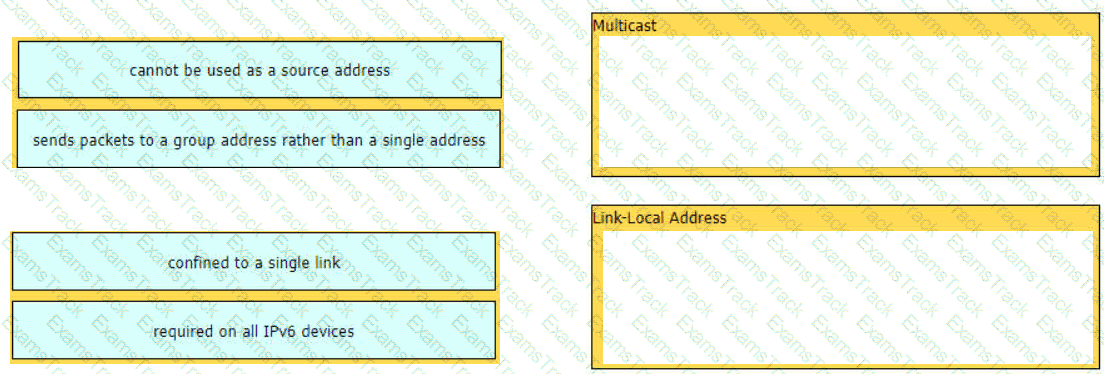
Drag and drop the IPv6 address details from the left onto the corresponding types on the right.
Which two capabilities of Cisco DNA Center make it more extensible as compared to traditional campus device management? (Choose two.)
Refer the exhibit.
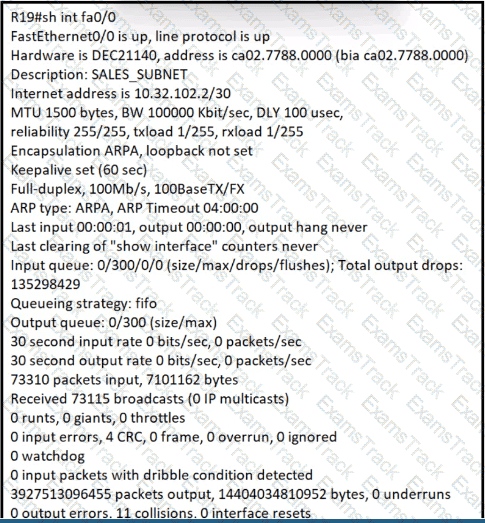
What is the cause of poor performance on router R19?
How does encryption project the wireless network?
What is a functionality of the control plane in the network?
Refer to the exhibit.
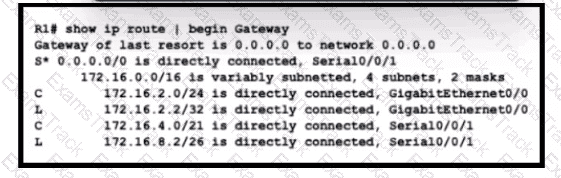
What is the subnet mask for route 172.16.4.0?
Refer to the exhibit.

How many JSON objects are represented?
What is the difference between SNMP traps and SNMP polling?
A)

B)

C)

D)
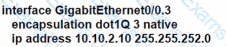
Drag and drop the DNS commands from the left onto their effects on the right.
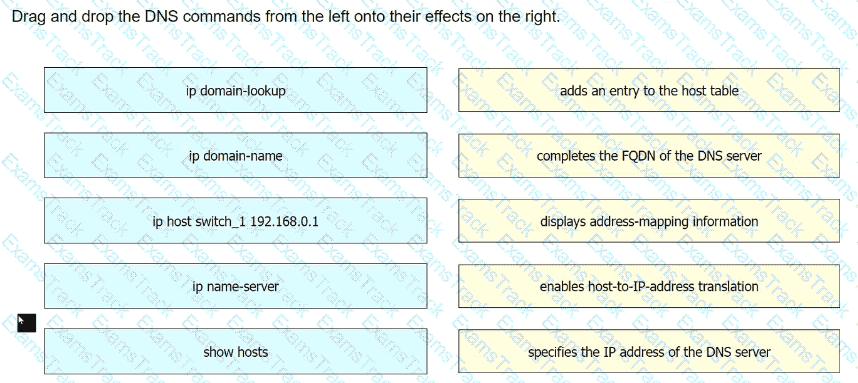
Drag and drop the statements about networking from the left onto the corresponding networking types on the right. Not all statements are used.
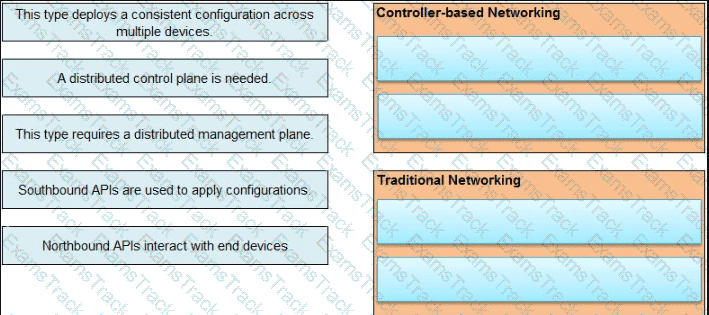
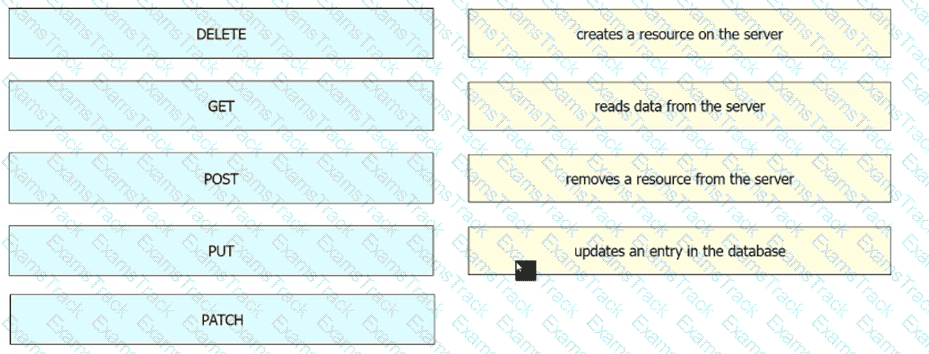
Drag and drop the HTTP methods used with REST-Based APIs from the left onto the descriptions on the right.
Which Rapid PVST+ feature should be configured on a switch port to immediately send traffic to a connected server as soon as it is active?
A network engineer is upgrading a small data center to host several new applications, including server backups that are expected to account for up to 90% of the bandwidth during peak times. The data center connects to the MPLS network provider via a primary circuit and a secondary circuit. How does the engineer inexpensively update the data center to avoid saturation of the primary circuit by traffic associated with the backups?
What is an enhancement implemented in WPA3?
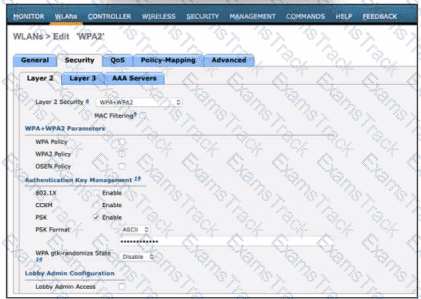
Refer to the exhibit. A network engineer is configuring a WLAN to use a WPA2 PSK and allow only specific clients to join. Which two actions must be taken to complete the process? (Choose two.)
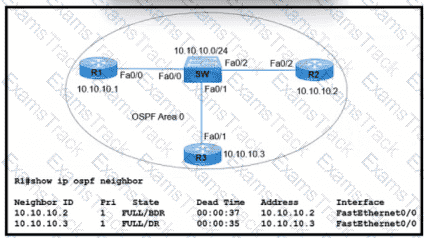
Refer to the exhibit. R1 has taken the DROTHER role in the OSPF DR/BDR election process. Which configuration must an engineer implement so that R1 is elected as the DR?
Drag and drop the REST API call method for HTTP from the left onto the action they perform on the right.
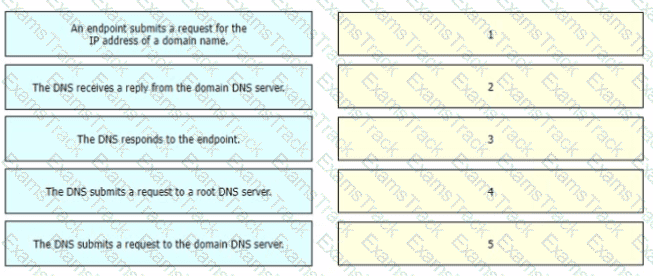
Drag and drop the steps in a standard DNS lookup operation from the left into the order on the right.
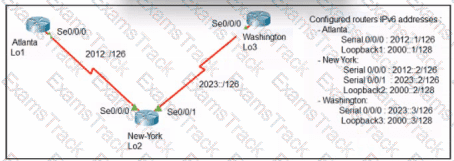
Refer to the exhibit. An engineer configured the New York router with static routes that point to the Atlanta and Washington sites. Which command must be configured on the Atlanta and Washington routers so that both sites are able to reach the Lo2 interface on the New York router?
To improve corporate security, an organization is planning to implement badge authentication to limit access to the data center. Which element of a security program is being deployed?
What is the put method within HTTP?
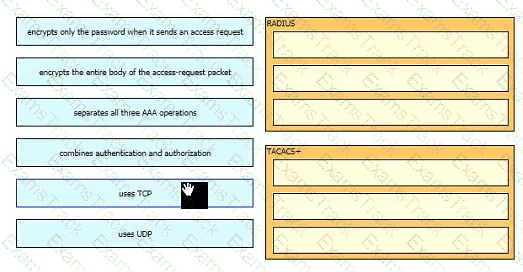
Drag and drop the functions of AAA supporting protocols from the left onto the protocols on the right.
What describes the functionality of southbound APIs?
Drag and drop the characteristic from the left onto the IPv6 address type on the right.
What is the role of nonoverlapping channels in a wireless environment?
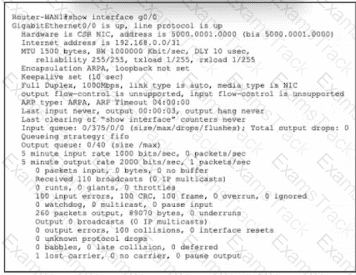
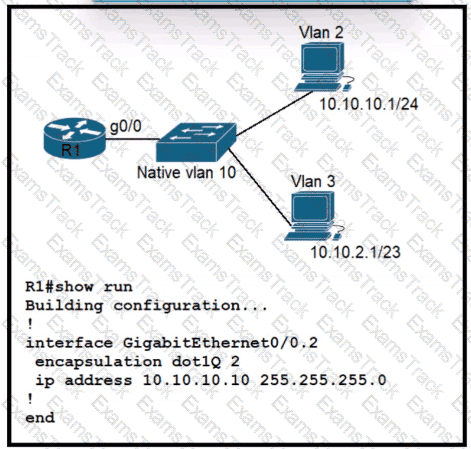
Refer to the exhibit. Router-WAN1 has a new connection via Gi0/0 to the ISP. Users running the web applications indicate that connectivity is unstable to the internet. What is causing the interface issue?
Refer to the exhibit.
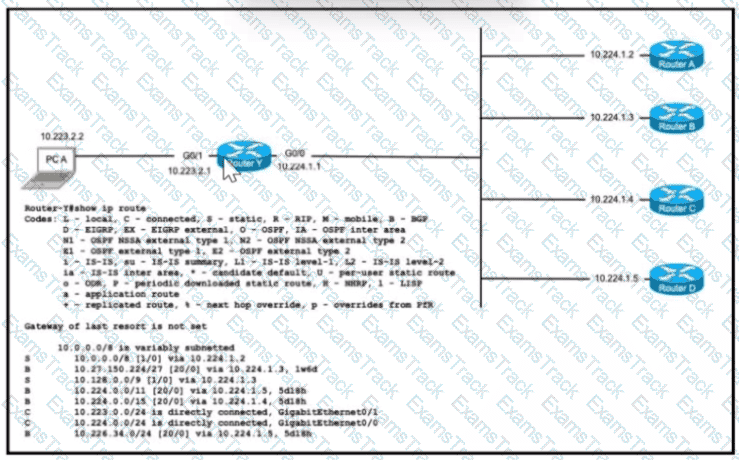
PC A is communicating with another device at IP address 10.227.225.255. Through which router does router Y route the traffic?
Which cipher is supported for wireless encryption only with the WPA2 standard?
Which type of DNS record is used to specify the mail server responsible for accepting email messages on behalf of a recipient's domain?
An engineer must configure a core router with a floating static default route to the backup router at 10.200.0.2. Which command meets the requirements?
Refer to the exhibit.
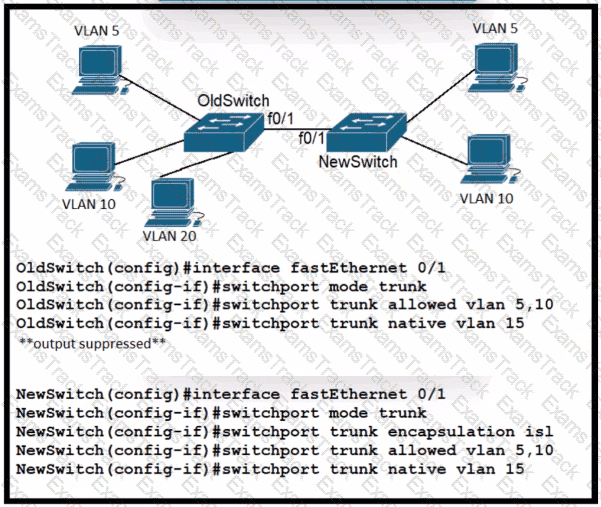
A new VLAN and switch are added to the network. A remote engineer configures OldSwitch and must ensure that the configuration meets these requirements:
• accommodates current configured VLANs
• expands the range to include VLAN 20
• allows for IEEE standard support for virtual LANs
Which configuration on the NewSwitch side of the link meets these requirements?
A)

B)

C)
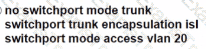
D)

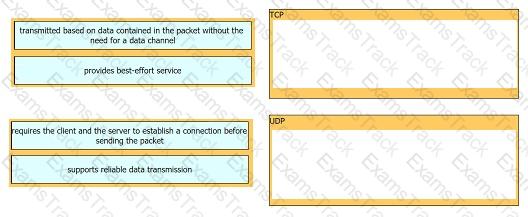
Drag and drop the TCP or UDP details from the left onto their corresponding protocols on the right.
What is a function of MAC address learning?
What are two functions of DHCP servers? (Choose two.)
A router received three destination prefixes:10.0.0/18, and 10.0.0/24. When the show ip route command is executed, which output does it return?
A)
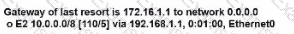
B)
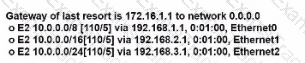
C)
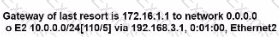
D)

Refer to the exhibit.
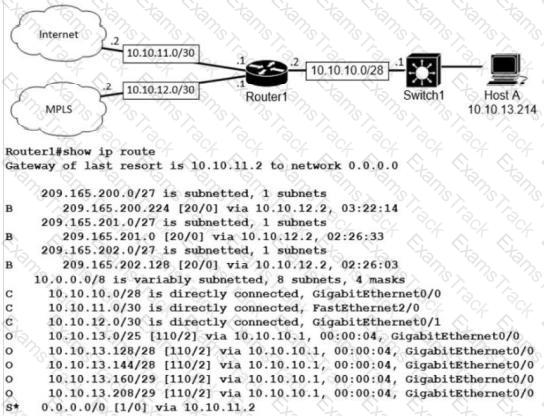
What is the prefix length for the route that router1 will use to reach host A?
Which group of channels in the 802.1ib/g/n/ac/ax 2.4 GHz frequency Bands are nonoverlapping channels?
A switch is forwarding a frame out of all interfaces except the interface that received the frame. What is the technical term for this process?
Which component controls and distributes physical resources for each virtual machine?
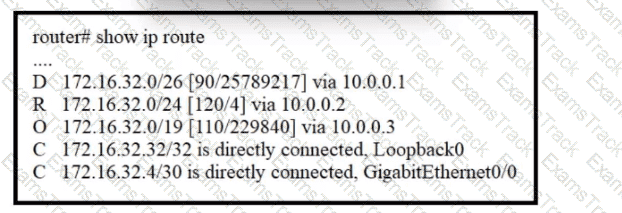
Refer to the exhibit. A packet sourced from 172.16.32.254 is destined for 172.16.32.8. What is the subnet mask of the preferred destination route?
What is a reason to implement LAG on a Cisco WLC?
Which cable type must be used when connecting a router and switch together using these criteria?
• Pins 1 and 2 are receivers and pins 3 and 6 are transmitters
• Auto detection MDi-X is unavailable
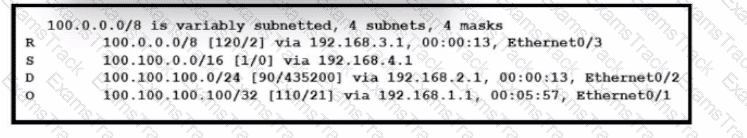
Refer to the exhibit. How will the device handle a packet destined to IP address 100.100.100.100?
Refer to the exhibit.
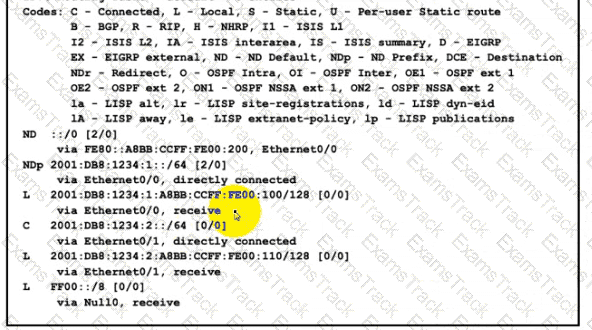
The administrator must configure a floating sialic default route that points to 2001:db8:1234:2::1 and replaces the current default route only if it fails. Which command must the engineer configure on the CPE?
|
PDF + Testing Engine
|
|---|
|
$52.5 |
|
Testing Engine
|
|---|
|
$40.5 |
|
PDF (Q&A)
|
|---|
|
$34.5 |
Cisco Free Exams |
|---|

|