Which two statements distinguish authentication from accounting? (Choose two.)
Refer to the exhibit.
An engineer assigns IP addressing to the current VLAN with three PCs. The configuration must also account for the expansion of 30 additional VLANS using the same Class C subnet for subnetting and host count. Which command set fulfills the request while reserving address space for the expected growth?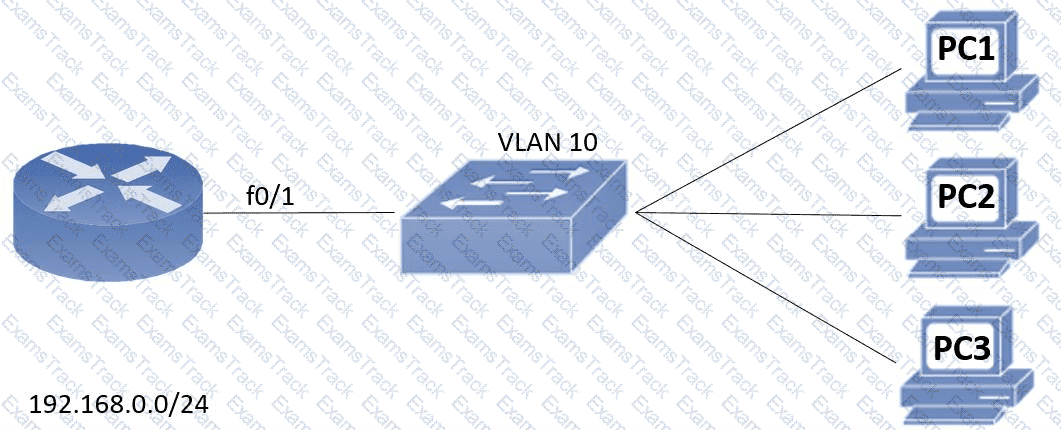
Why would a network administrator choose to implement RFC 1918 address space?
Refer to the exhibit.
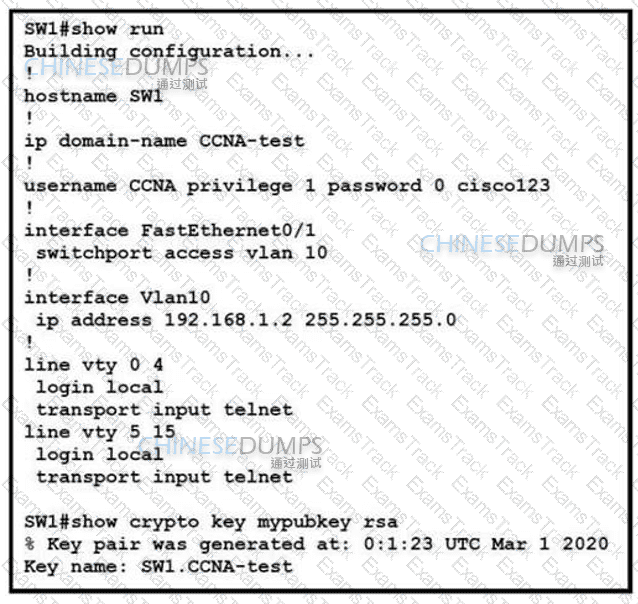
An engineer is updating the management access configuration of switch SW1 to allow secured, encrypted remote configuration. Which two commands or command sequences must the engineer apply to the switch? (Choose two.)
An engineer configures interface Gi1/0 on the company PE router to connect to an ISP Neighbor discovery is disabled
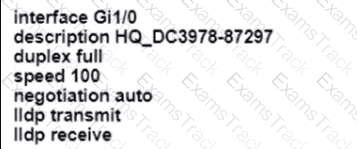
Which action is necessary to complete the configuration if the ISP uses third-party network devices?
Refer to the exhibit.
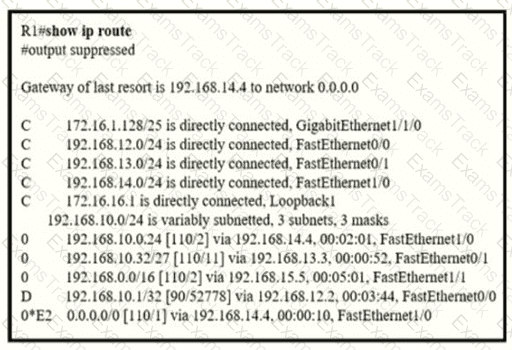
If R1 receives a packet destined to 172.161.1, to which IP address does it send the packet?
An engineer needs to configure LLDP to send the port description time length value (TLV). What command sequence must be implemented?
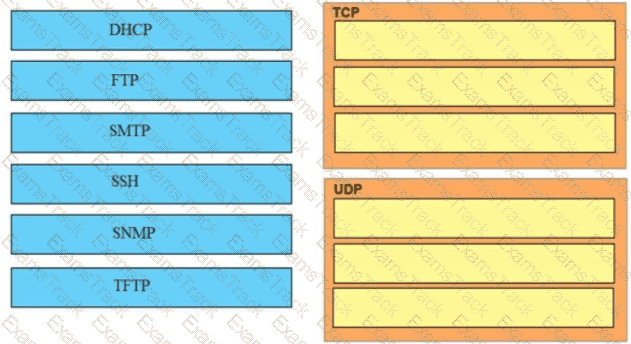
Drag and drop the application protocols from the left onto the transport protocols that it uses on the right
A wireless administrator has configured a WLAN; however, the clients need access to a less congested 5-GHz network for their voice quality. What action must be taken to meet the requirement?
What is a similarly between 1000BASE-LX and 1000BASE-T standards?
A Cisco IP phone receive untagged data traffic from an attached PC. Which action is taken by the phone?
Refer to me exhibit.
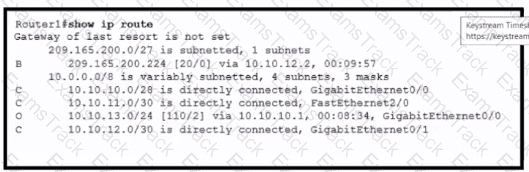
Which action is taken by the router when a packet is sourced from 10.10.10.2 and destined for 10.10.10.16?
Which technology must be implemented to configure network device monitoring with the highest security?
What is a capability of FTP in network management operations?
Refer to the exhibit.

An engineer is bringing up a new circuit to the MPLS provider on the Gi0/1 interface of Router1 The new circuit uses eBGP and teams the route to VLAN25 from the BGP path What s the expected behavior for the traffic flow for route 10.10.13.0/25?
What are two benefits of FHRPs? (Choose two.)
Which networking function occurs on the data plane?
Which IPv6 address type provides communication between subnets and is unable to route on the Internet?
Why choose Cisco DNA Center for automated lifecycle management?
How does frame switching function on a switch?
|
PDF + Testing Engine
|
|---|
|
$61.25 |
|
Testing Engine
|
|---|
|
$47.25 |
|
PDF (Q&A)
|
|---|
|
$40.25 |
Cisco Free Exams |
|---|

|