What is the expected outcome when an EUI-64 address is generated?
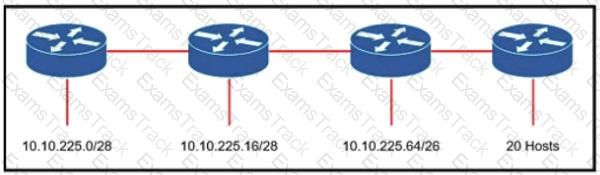
Refer to the exhibit. An engineer must add a subnet for a new office that will add 20 users to the network. Which IPv4 network and subnet mask combination does the engineer assign to minimize wasting addresses?
Refer to the exhibit.
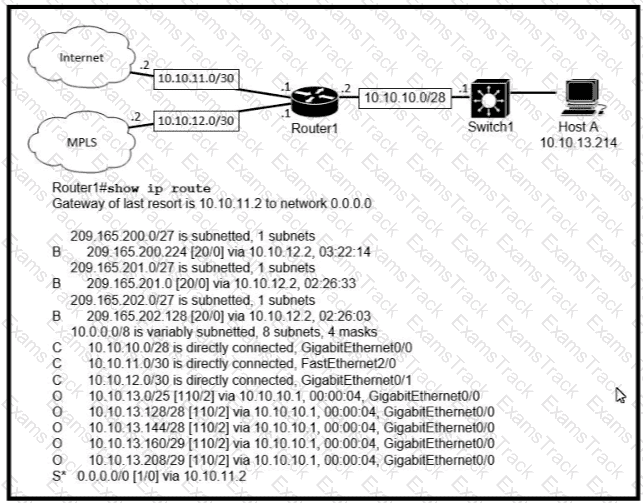
Which prefix does Router 1 use for traffic to Host A?
Refer to the exhibit.

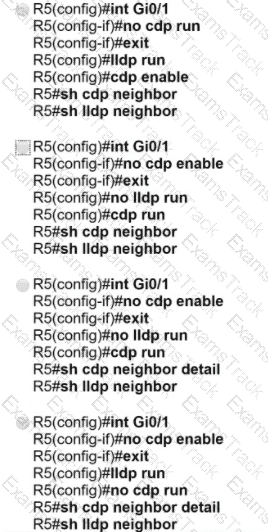
For security reasons, automatic neighbor discovery must be disabled on the R5 Gi0/1 interface. These tasks must be completed:
• Disable all neighbor discovery methods on R5 interface GiO/1.
• Permit neighbor discovery on R5 interface GiO/2.
• Verify there are no dynamically learned neighbors on R5 interface Gi0/1.
• Display the IP address of R6*s interface Gi0/2.
Which configuration must be used?
Which two QoS tools provides congestion management? ( Choose two )
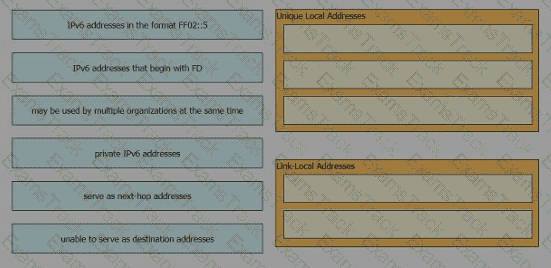
What is a characteristic of private IPv4 addressing?
A wireless administrator has configured a WLAN; however, the clients need access to a less congested 5-GHz network for their voice quality. What action must be taken to meet the requirement?
Refer to the exhibit.

What is the effect of this configuration?
Refer to the exhibit.
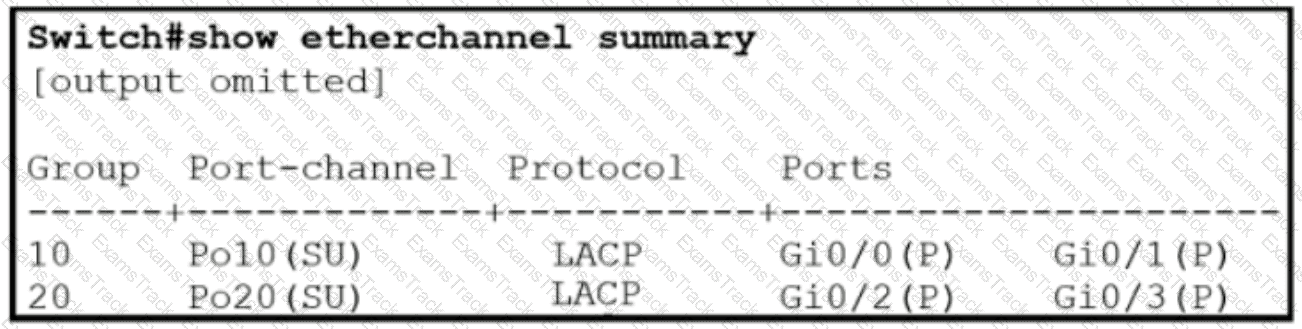
Which two commands were used to create port channel 10? (Choose two )

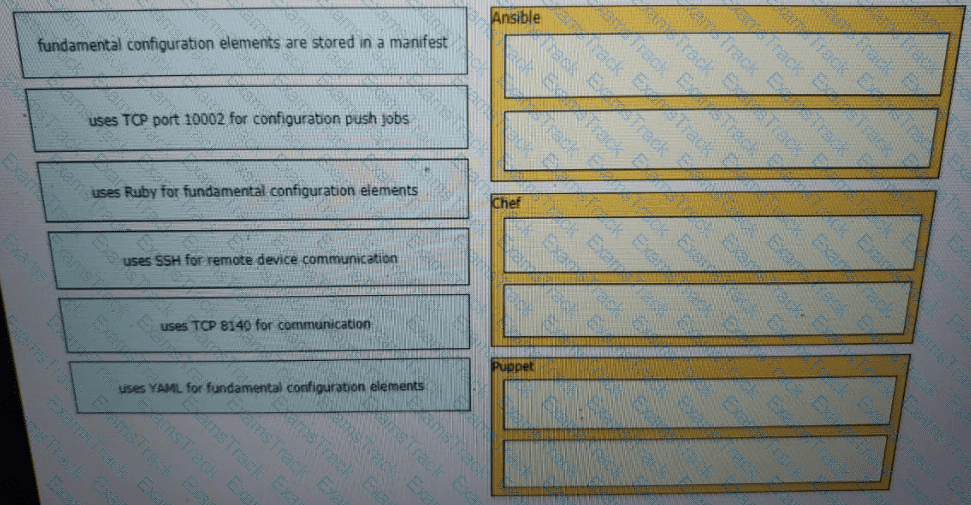
Drag and drop the descriptions from the left onto the configuration-management technologies on the right.
How does the dynamically-learned MAC address feature function?
Refer to the exhibit.
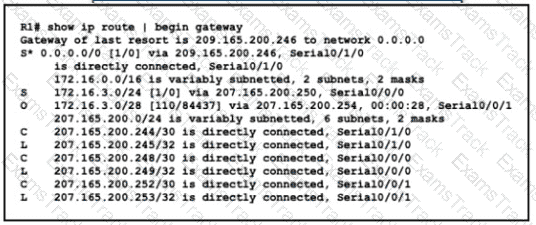
A packet is being sent across router R1 to host 172.163.3.14. To which destination does the router send the packet?
Which two actions influence the EIGRP route selection process? (Choose two)
What are two characteristics of a public cloud Implementation? (Choose two.)
Refer to the exhibit.
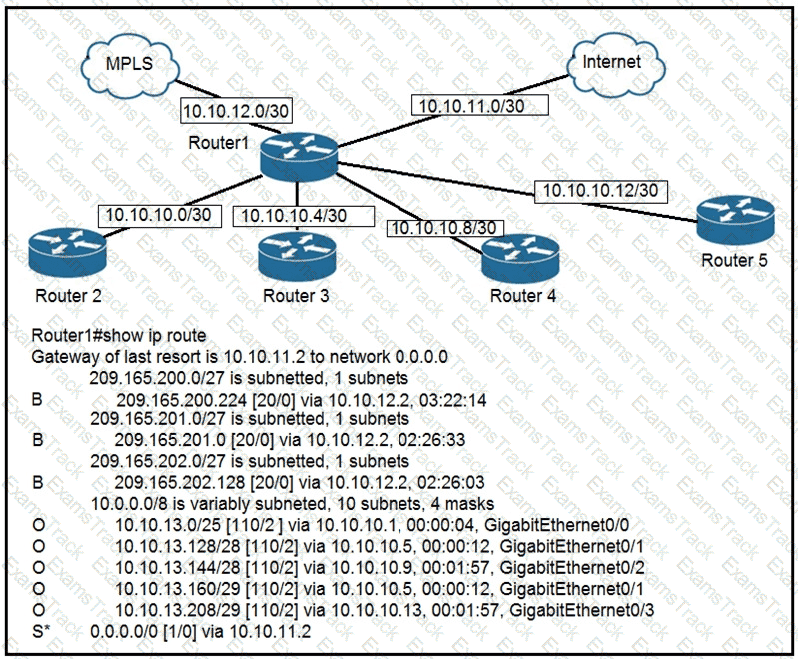
To which device does Router1 send packets that are destined to host 10.10.13.165?
Which IPv6 address type provides communication between subnets and is unable to route on the Internet?
Which network plane is centralized and manages routing decisions?
What are two recommendations for protecting network ports from being exploited when located in an office space outside of an IT closer? (Choose two.)
An engineer must configure a WLAN using the strongest encryption type for WPA2- PSK. Which cipher fulfills the configuration requirement?
When a WLAN with WPA2 PSK is configured in the Wireless LAN Controller GUI which format is supported?
What benefit does controller-based networking provide versus traditional networking?
An engineer must configure traffic for a VLAN that is untagged by the switch as it crosses a trunk link. Which command should be used?
Refer to the exhibit.
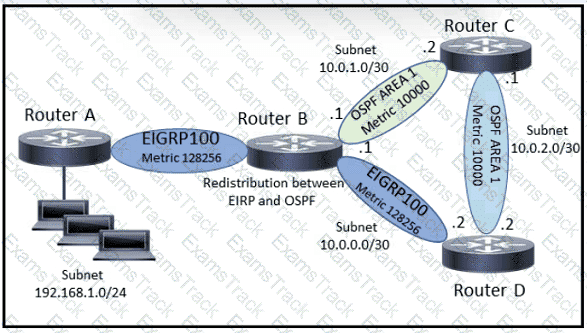
A network engineer executes the show ip route command on router D. What is the next hop to network 192.168 1 0/24 and why?
Which unified access point mode continues to serve wireless clients after losing connectivity to the Cisco Wireless LAN Controller?
What are two benefits of network automation? (Choose two.)
A network engineer must migrate a router loopback interface to the IPv6 address space. If the current IPv4 address of the interface is 10.54.73.1/32, and the engineer configures IPv6 address 0.0.0.0.0:ffff:a36:4901, which prefix length must be used?
Drag and drop the IPv6 address description from the left onto the IPv6 address types on the right. Not all options are used.
A new DHCP server has been deployed in a corporate environment with lease time set to eight hours. Which CMD command on a Windows-based device allows the engineer to verify the DHCP lease expiration?
Which action does the router take as rt forwards a packet through the network?
The service password-encryption command is entered on a router. What is the effect of this configuration?
Which JSON data type is an unordered set of attribute- value pairs?
Which WPA3 enhancement protects against hackers viewing traffic on the Wi-Fi network?
Which function does an SNMP agent perform?
A Cisco IP phone receive untagged data traffic from an attached PC. Which action is taken by the phone?
Refer to the exhibit.
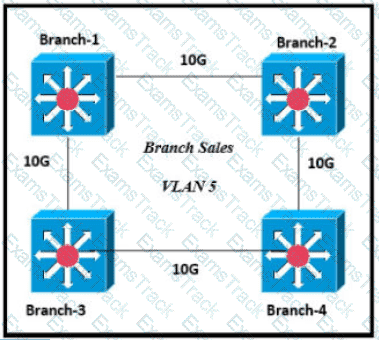
Only four switches are participating in the VLAN spanning-tree process.
Branch-1 priority 614440
Branch-2: priority 39082416
Branch-3: priority 0
Branch-4: root primary
Which switch becomes the permanent root bridge for VLAN 5?
Refer to the exhibit.
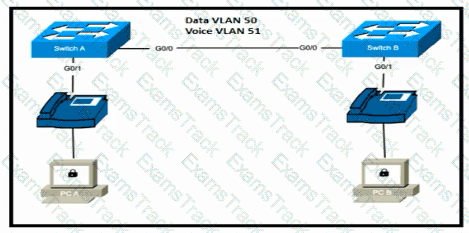
Switch A is newly configured. All VLANs are present in the VLAN database. The IP phone and PC A on Gi0/1 must be configured for the appropriate VLANs to establish connectivity between the PCs. Which command set fulfills the requirement?
A)

B)

C)

D)

What is the primary purpose of a First Hop Redundancy Protocol?
Which protocol requires authentication to transfer a backup configuration file from a router to a remote server?
Refer to the exhibit.
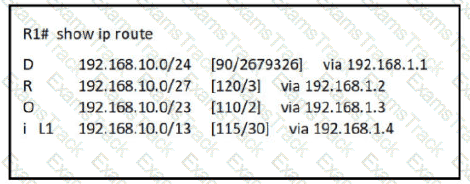
How does router R1 handle traffic to 192.168.10.16?
How does CAPWAP communicate between an access point in local mode and a WLC?
What is the benefit of configuring PortFast on an interface?
What are two reasons that cause late collisions to increment on an Ethernet interface? (Choose two)
Refer to the exhibit.
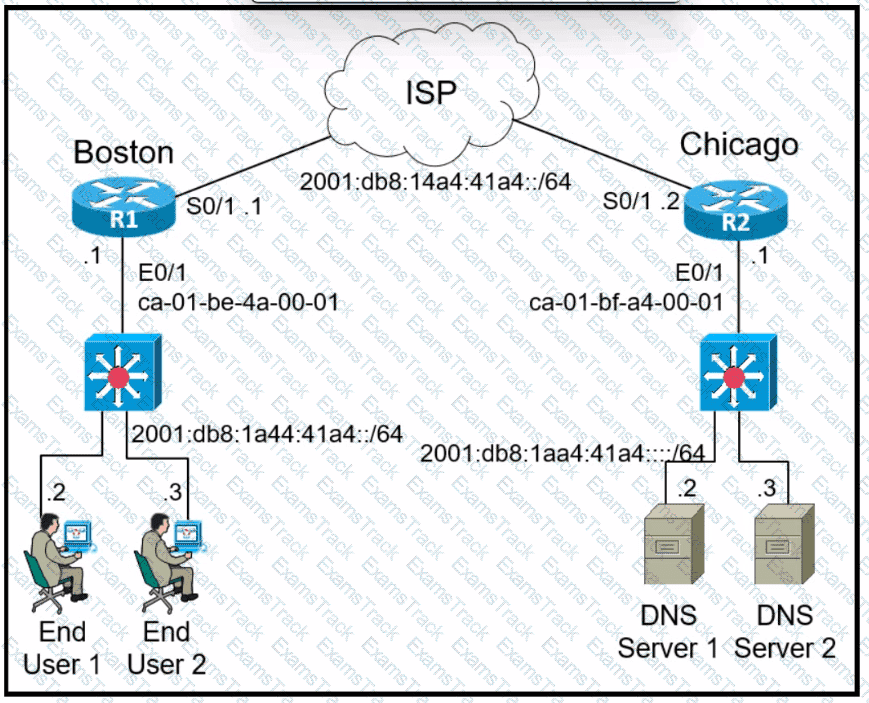
Refer to the exhibit. The IPv6 address for the LAN segment on router R1 must be configured using the EUI-64 format. When configured which ipv6 address is produced by the router?
Refer to the exhibit.
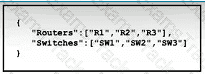
What is represented by "R1" and "SW1" within the JSON output?
What is the role of the root port in a switched network?
Which two network actions occur within the data plane? (Choose two.)
Refer to the exhibit.
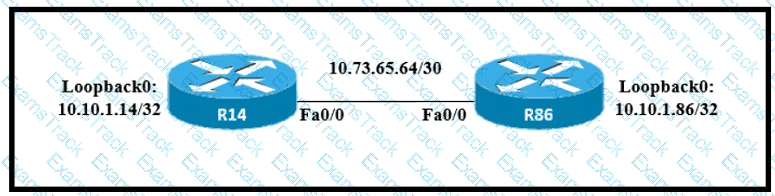
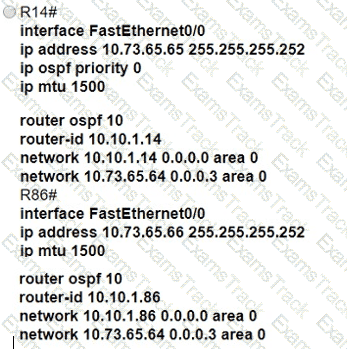
All interfaces are configured with duplex auto and ip ospf network broadcast. Which configuration allows routers R14 and R86 to form an OSPFv2 adjacency and act as a central point for exchanging OSPF information between routers?
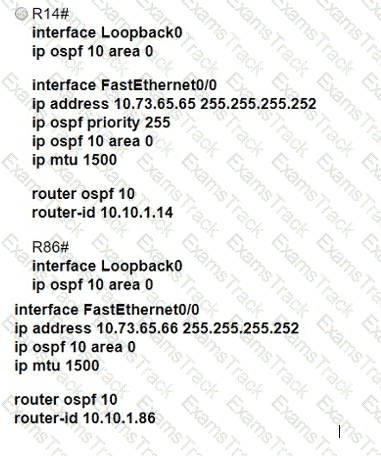
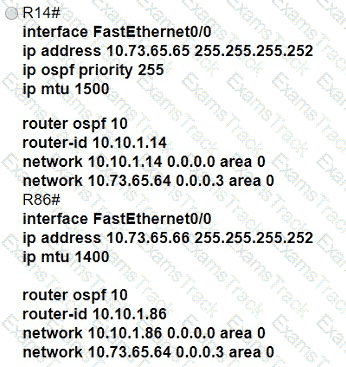
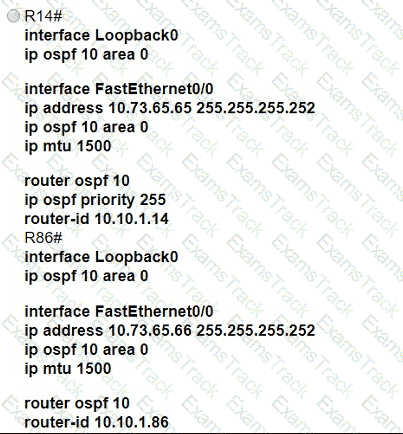
Refer to the exhibit.
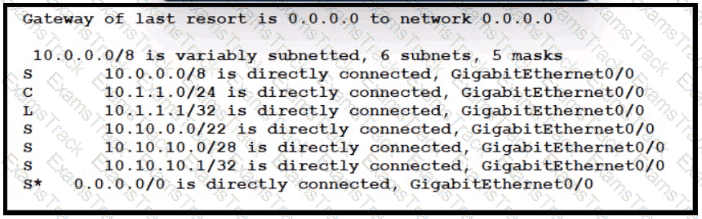
Which IP route command created the best path for a packet destined for 10.10.10.3?
What is the MAC address used with VRRP as a virtual address?
Refer to the exhibit.

Which action must be taken so that neighbofing devices rapidly discover switch Cat9300?
|
PDF + Testing Engine
|
|---|
|
$52.5 |
|
Testing Engine
|
|---|
|
$40.5 |
|
PDF (Q&A)
|
|---|
|
$34.5 |
Cisco Free Exams |
|---|

|