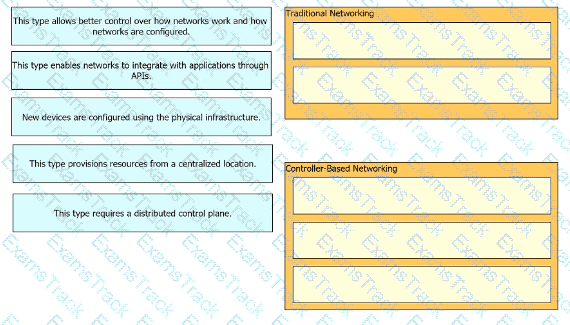
Drag and drop the statements about networking from the left onto the corresponding networking types on the right.
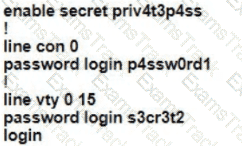
A Cisco engineer is configuring a factory-default router with these three passwords:
• The user EXEC password for console access is p4ssw0rd1
• The user EXEC password for Telnet access is s3cr3t2
• The password for privileged EXEC mode is pnv4t3p4ss Which command sequence must the engineer configured
A)
B)
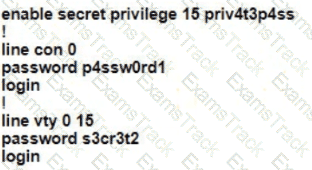
C)
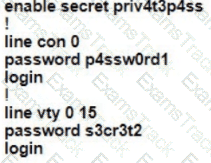
D)

Which characteristic differentiates the concept of authentication from authorization and accounting?
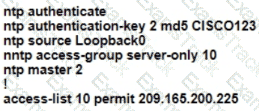
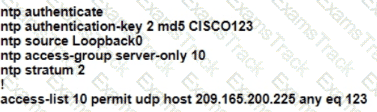
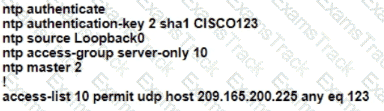
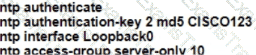
R1 as an NTP server must have:
• NTP authentication enabled
• NTP packets sourced from Interface loopback 0
• NTP stratum 2
• NTP packets only permitted to client IP 209.165 200 225
How should R1 be configured?
A)
B)
C)
D)
Refer to the exhibit.
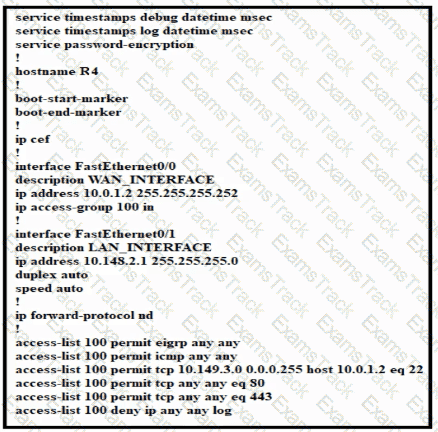
Which configuration enables DHCP addressing for hosts connected to interface FastEthernetO/1 on router R4?
Which field within the access-request packet is encrypted by RADIUS?
Refer to the exhibit.
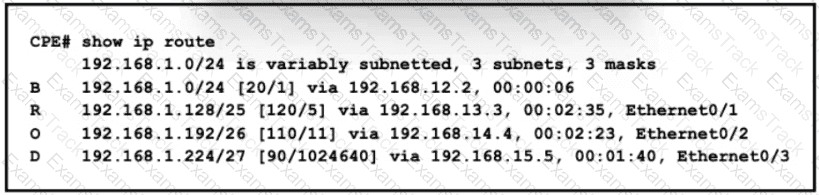
All traffic enters the CPE router from interface Serial0/3 with an IP address of 192 168 50 1 Web traffic from the WAN is destined for a LAN network where servers are load-balanced An IP packet with a destination address of the HTTP virtual IP of 192 1681 250 must be forwarded Which routing table entry does the router use?
Refer to the exhibit.
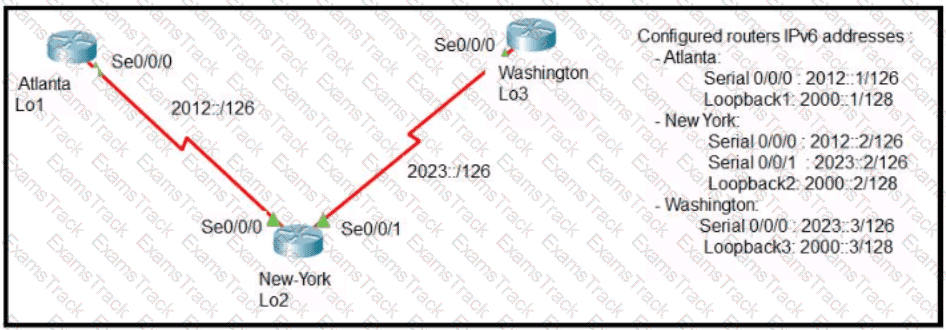
The New York router is configured with static routes pointing to the Atlanta and Washington sites. Which two tasks must be performed so that the Serial0/0/0 interfaces on the Atlanta and Washington routers can reach one another?
(Choose two.)
What are two benefits of FHRPs? (Choose two.)
Refer to the exhibit.
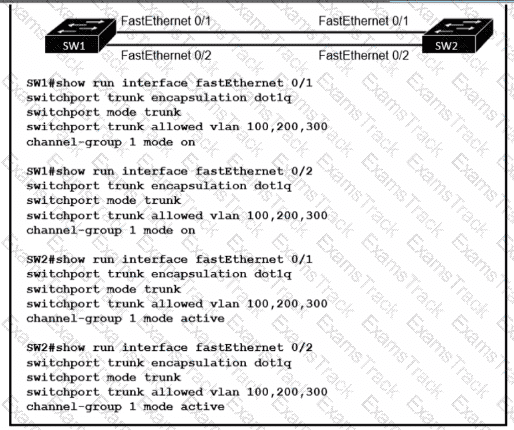
An engineer built a new L2 LACP EtherChannel between SW1 and SW2 and executed these show commands to verify the work. Which additional task allows the two switches to establish an LACP port channel?
A network engineer must create a diagram of a multivendor network. Which command must be configured on the Cisco devices so that the topology of the network can be mapped?
Refer to the exhibit.
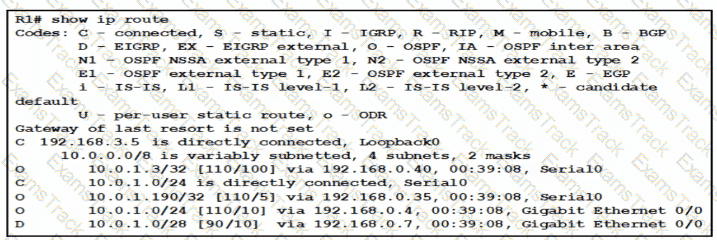
Traffic sourced from the loopback0 Interface is trying to connect via ssh to the host at 10.0.1.15. What Is the next hop to the destination address?
OSPF must be configured between routers R1 and R2. Which OSPF configuration must be applied to router R1 to avoid a DR/BDR election?
An implementer is preparing hardware for virtualization to create virtual machines on a host. What is needed to provide communication between hardware and virtual machines?
What are two characteristics of an SSID? (Choose Two)
What is the same for both copper and fiber interfaces when using SFP modules?
An engineer must configure R1 for a new user account. The account must meet these requirements:
* It must be configured in the local database.
* The username is engineer.
* It must use the strongest password configurable. Which command must the engineer configure on the router?
Refer to the exhibit.
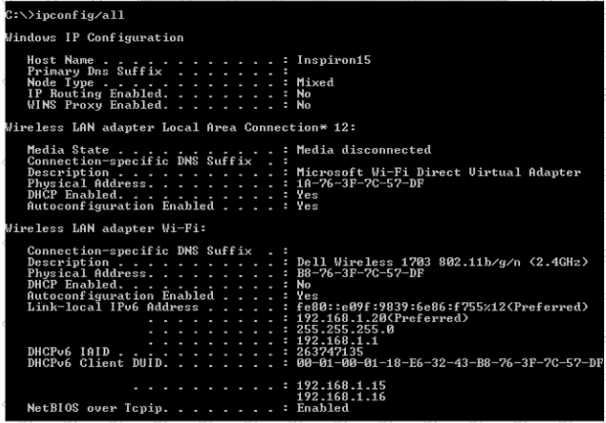
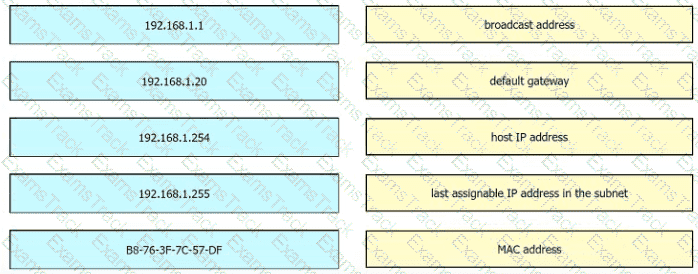
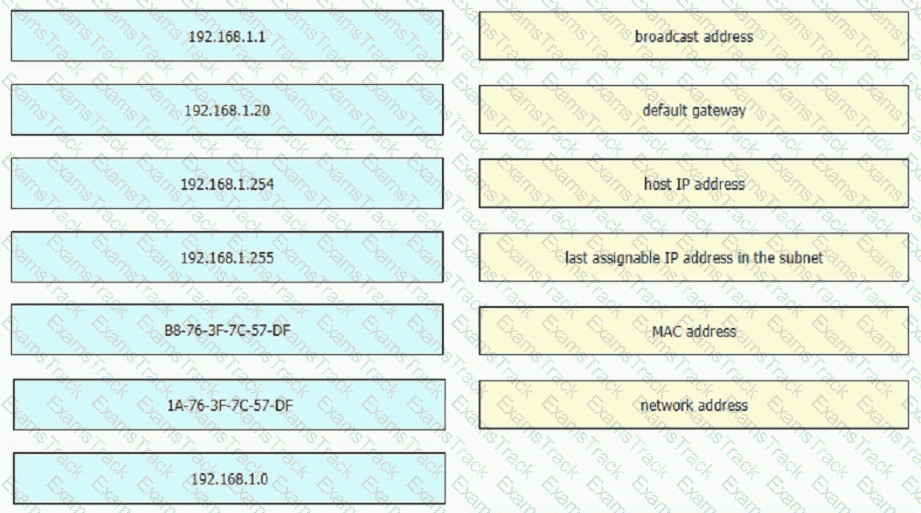
An engineer is tasked with verifying network configuration parameters on a client workstation to report back to the team lead. Drag and drop the node identifiers from the left onto the network parameters on the right.
Refer to the exhibit.
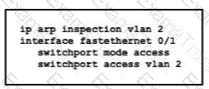
What is the effect of this configuration?
When a client and server are not on the same physical network, which device is used to forward requests and replies between client and server for DHCP?
A network administrator needs to aggregate 4 ports into a single logical link which must negotiate layer 2 connectivity to ports on another switch. What must be configured when using active mode on both sides of the connection?
An engineer must establish a trunk link between two switches. The neighboring switch is set to trunk or desirable mode. What action should be taken?
Which two tasks must be performed to configure NTP to a trusted server in client mode on a single network device? (Choose two)
Which port type supports the spanning-tree portfast command without additional configuration?
Refer to the exhibit.
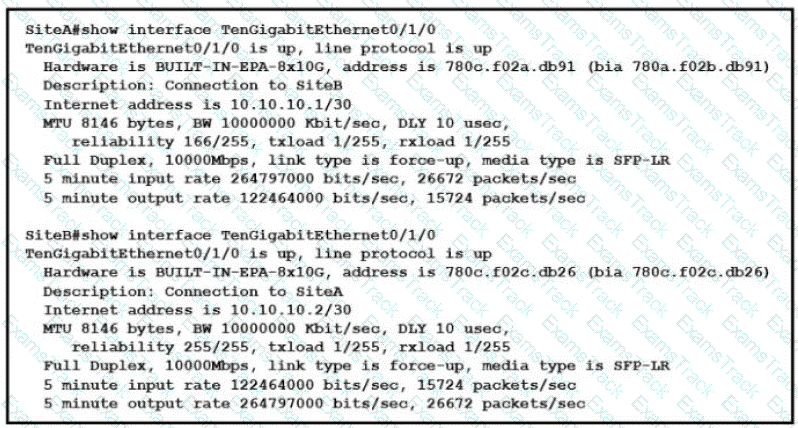
Shortly after SiteA was connected to SiteB over a new single-mode fiber path users at SiteA report intermittent connectivity issues with applications hosted at SiteB What is the cause of the intermittent connectivity issue?
What is the primary function of a Layer 3 device?
What is a capability of FTP in network management operations?
A user configured OSPF in a single area between two routers A serial interface connecting R1 and R2 is running encapsulation PPP By default which OSPF network type is seen on this interface when the user types show ip ospf interface on R1 or R2?
A network engineer must configure the router R1 GigabitEthernet1/1 interface to connect to the router R2 GigabitEthernet1/1 interface. For the configuration to be applied the engineer must compress the address 2001:0db8:0000:0000:0500:000a:400F:583B. Which command must be issued on the interface?
What role does a hypervisor provide for each virtual machine in server virtualization?
What is a characteristic of a Layer 2 switch?
Which interface condition is occurring in this output?

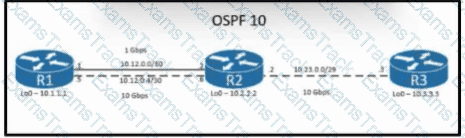
Refer to the exhibit. The loopback IP of R3 has been learned via the two interfaces on R1. R1 is configured with a reference bandwidth of 10 Gbps. Based on the metric calculations, which next hop IP would be used for outgoing routing?
Why would a network administrator choose to implement RFC 1918 address space?
Why are API keys used to enforce rate limiting?
A device detects two stations transmitting frames at the same time. This condition occurs after the first 64 bytes of the frame is received interface counter increments?
Which type of API allows SDN controllers to dynamically make changes to the network?
Refer to the exhibit.
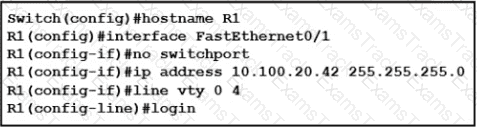
An engineer booted a new switch and applied this configuration via the console port. Which additional configuration must be applied to allow administrators to authenticate directly to enable privilege mode via Telnet using a local username and password?
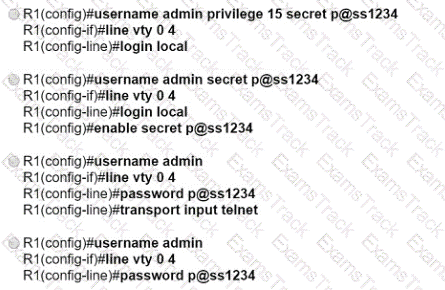
Refer to the exhibit.
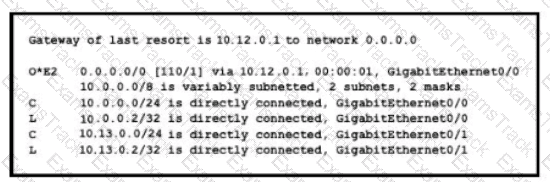
If configuring a static default route on the router with the ip route 0.0.0.0 0.0.0.0 10.13.0.1 120 command how does the router respond?
What are two benefits of network automation? (Choose two)
Refer to the exhibit.
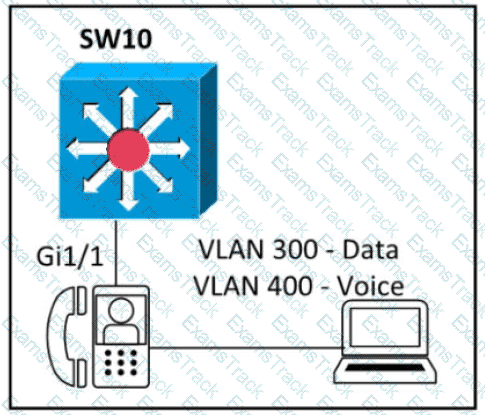
An engineer must configure GigabitEthernet1/1 to accommodate voice and data traffic Which configuration accomplishes this task?

Refer to the exhibit.
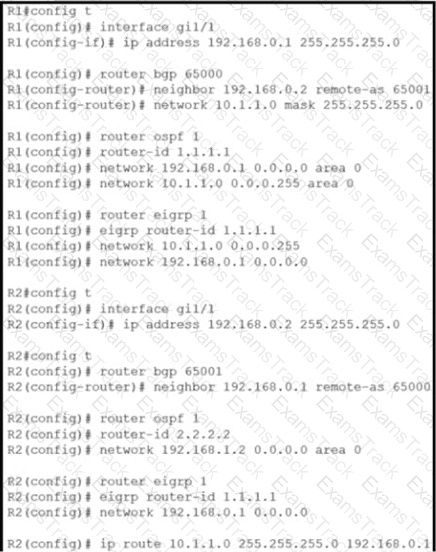
Router R2 is configured with multiple routes to reach network 10 1.1 0/24 from router R1. What protocol is chosen by router R2 to reach the destination network 10.1 1 0/24?
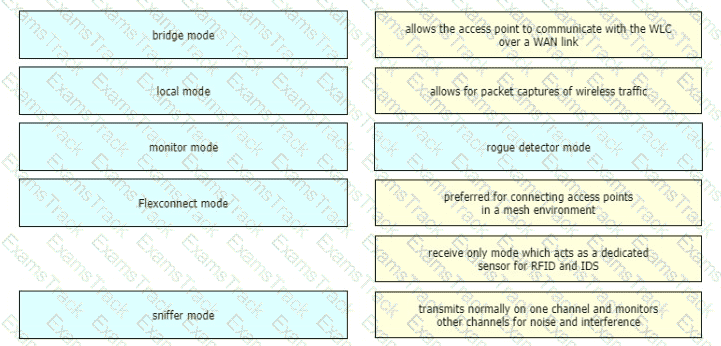
Drag and drop the lightweight access point operation modes from the left onto the descriptions on the right
Refer to the exhibit.
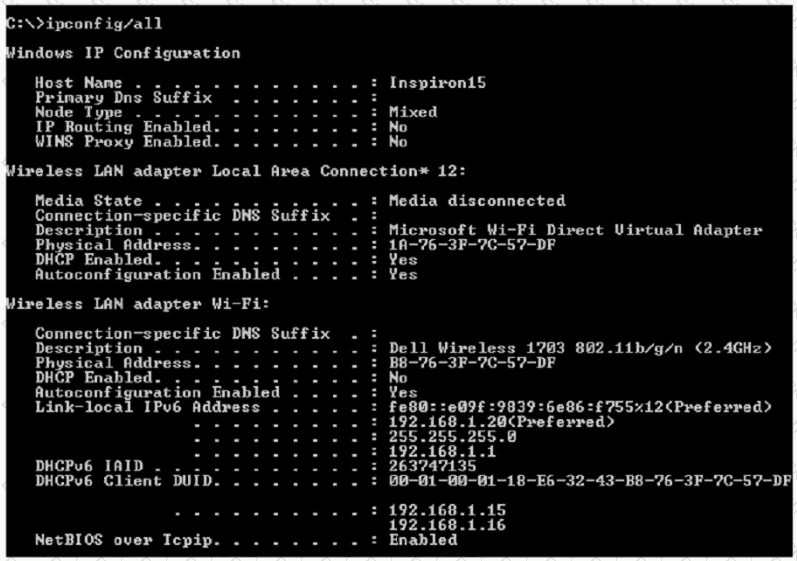
An engineer is required to verify that the network parameters are valid for the users wireless LAN connectivity on a /24 subnet. Drag and drop the values from the left onto the network parameters on the right. Not all values are used.
What are two differences between optical-fiber cabling and copper cabling? (Choose two)
Which two primary drivers support the need for network automation? (Choose two.)
Which type of organization should use a collapsed-core architecture?
Which result occurs when PortFast is enabled on an interface that is connected to another switch?
An engineer needs to configure LLDP to send the port description time length value (TLV). What command sequence must be implemented?
|
PDF + Testing Engine
|
|---|
|
$52.5 |
|
Testing Engine
|
|---|
|
$40.5 |
|
PDF (Q&A)
|
|---|
|
$34.5 |
Cisco Free Exams |
|---|

|