Which two outcomes are predictable behaviors for HSRP? (Choose two.)
When implementing a router as a DHCP server, which two features must be configured'? (Choose two)
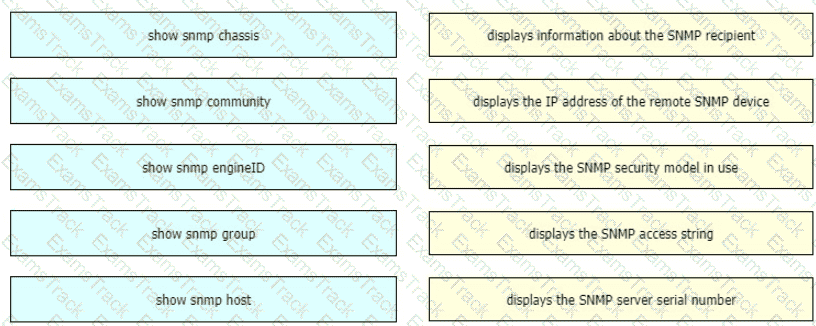
Drag and drop the SNMP manager and agent identifier commands from the left onto the functions on the right
Which technology is appropriate for communication between an SDN controller and applications running over the network?
Which configuration ensures that the switch is always the root for VLAN 750?
Refer to the exhibit.

What is the result if Gig1/11 receives an STP BPDU?
What criteria is used first during me root port selection process?
How do TCP and UDP differ in the way that they establish a connection between two endpoints?
Refer to the exhibit.
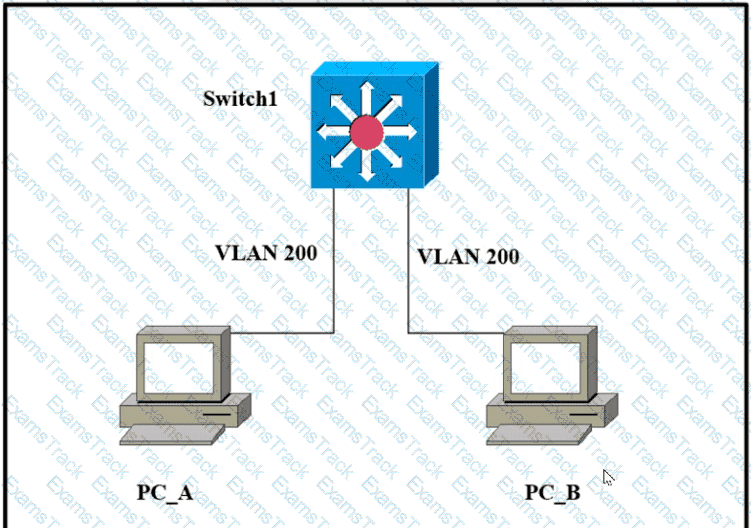
Which outcome is expected when PC_A sends data to PC_B?
What does a switch use to build its MAC address table?
Which feature on the Cisco Wireless LAN Controller when enabled restricts management access from specific networks?
Two switches are connected and using Cisco Dynamic Trunking Protocol SW1 is set to Dynamic Desirable
What is the result of this configuration?
What are two functions of an SDN controller? (Choose two)
What are two characteristics of the distribution layer in a three-tier network architecture? (Choose two.)
How is the native VLAN secured in a network?
A manager asks a network engineer to advise which cloud service models are used so employees do not have to waste their time installing, managing, and updating software which is only used occasionally Which cloud service model does the engineer recommend?
What is a characteristic of cloud-based network topology?
What software defined architecture plane assists network devices with making packet-forwarding decisions by providing Layer 2 reachability and Layer 3 routing information?
What facilitates a Telnet connection between devices by entering the device name?
Which type of attack can be mitigated by dynamic ARP inspection?
An organization has decided to start using cloud-provided services. Which cloud service allows the organization to install its own operating system on a virtual machine?
Which network allows devices to communicate without the need to access the Internet?
What is a DHCP client?
Aside from discarding, which two states does the switch port transition through while using RSTP (802.1w)? (Choose two)
Which CRUD operation modifies an existing table or view?
Several new coverage cells are required to improve the Wi-Fi network of an organization. Which two standard designs are recommended? (choose two.)
What is the purpose of using First Hop Redundancy Protocol in a specific subnet?
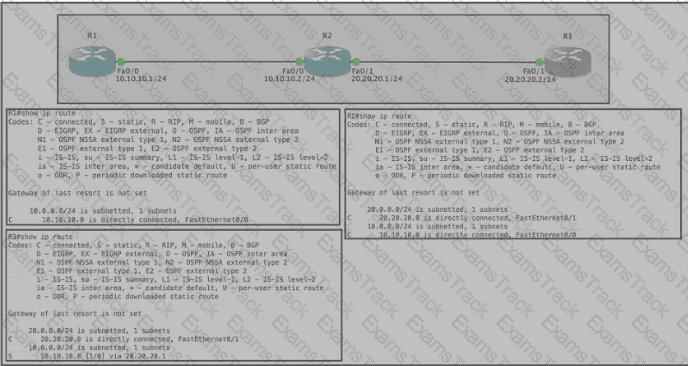
Refer to the exhibit Router R1 Fa0/0 is unable to ping router R3 Fa0'1. Which action must be taken in router R1 to help resolve the configuration issue?
Which command is used to specify the delay time in seconds for LLDP to initialize on any interface?
Refer to the exhibit.
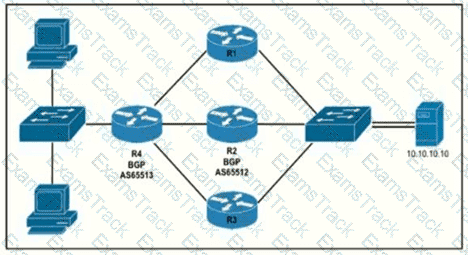
Router R4 is dynamically learning the path to the server. If R4 is connected to R1 via OSPF Area 20, to R2 v2ia R2 BGP, and to R3 via EIGRP 777, which path is installed in the routing table of R4?
When using Rapid PVST+, which command guarantees the switch is always the root bridge for VLAN 200?
Which switch technology establishes a network connection immediately when it is plugged in?
An email user has been lured into clicking a link in an email sent by their company's security organization. The webpage that opens reports that it was safe but the link could have contained malicious code. Which type of security program is in place?
Which technology is used to improve web traffic performance by proxy caching?
Which 802.11 management frame type is sent when a client roams between access points on the same SSID?
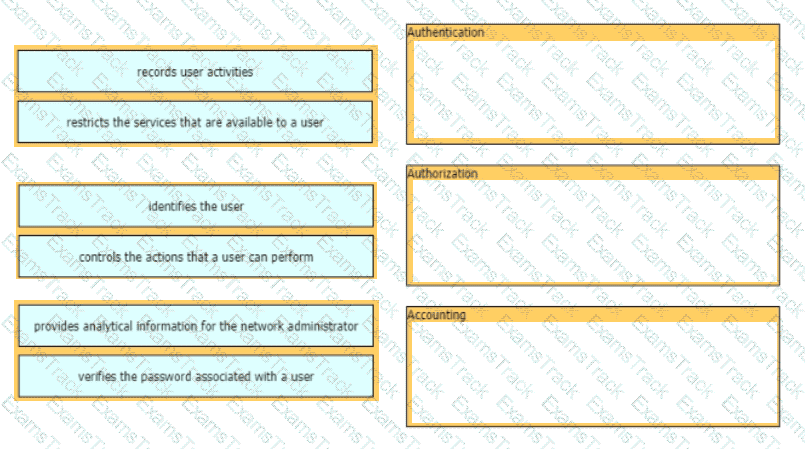
Drag and drop the AAA functions from the left onto the correct AAA services on the right
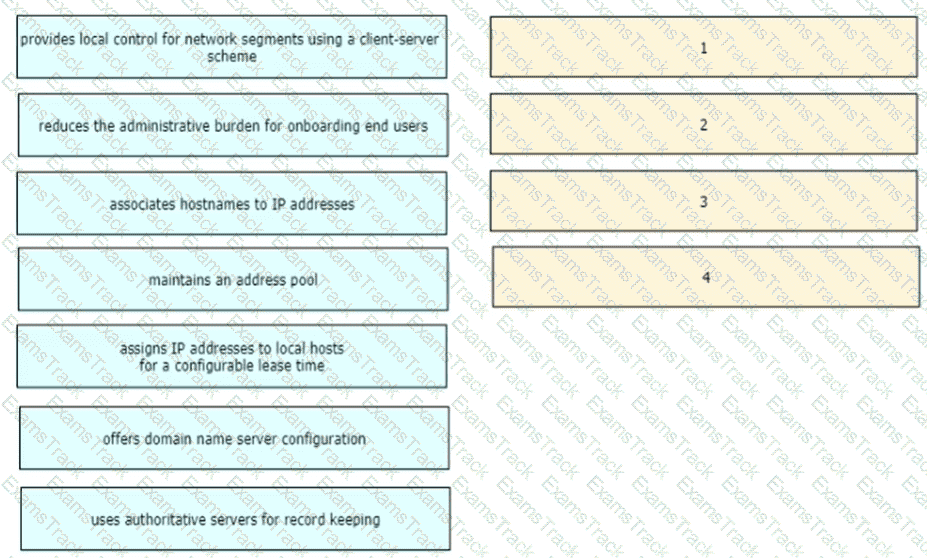
Drag and drop the functions of DHCP from the left onto any of the positions on the right Not all functions are used
What are two roles of Domain Name Services (DNS)? (Choose Two)
Which protocol is used for secure remote CLI access?
Refer to the exhibit.
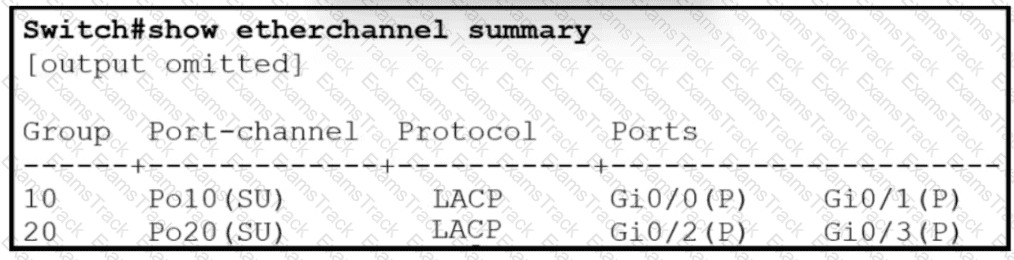
Which two commands when used together create port channel 10? (Choose two.)
Refer to the exhibit.
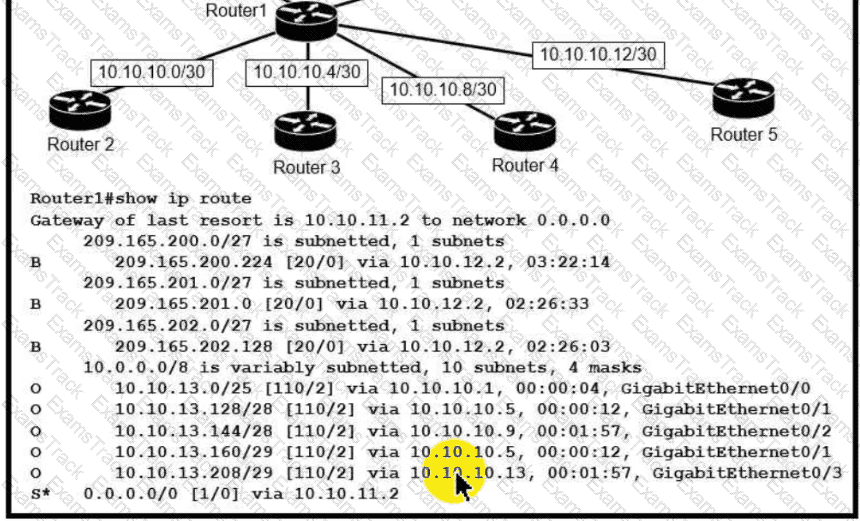
Which next-hop IP address does Routed use for packets destined to host 10 10.13.158?
Refer to the exhibit.
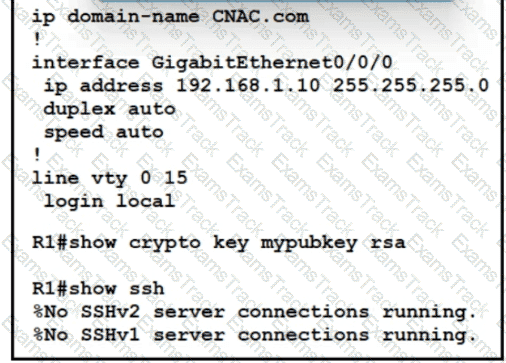
Which two commands must be added to update the configuration of router R1 so that it accepts only encrypted connections? (Choose two )
When configuring IPv6 on an interface, which two IPv6 multicast groups are joined? (Choose two)
What is the difference between IPv6 unicast and anycast addressing?
Refer to the exhibit.
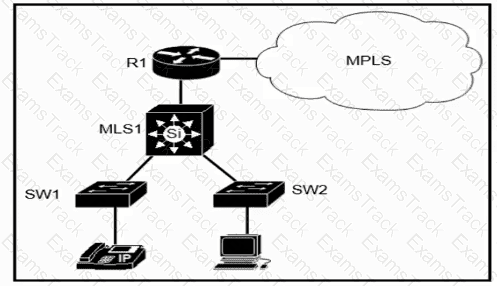
Which plan must be Implemented to ensure optimal QoS marking practices on this network?
Refer to the exhibit.
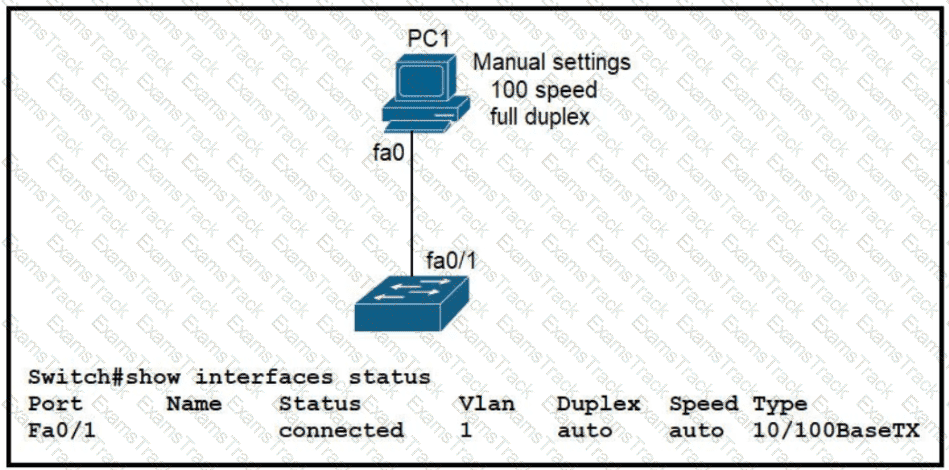
The link between PC1 and the switch is up. but it is performing poorly. Which interface condition is causing the performance problem?
Refer to the exhibit.
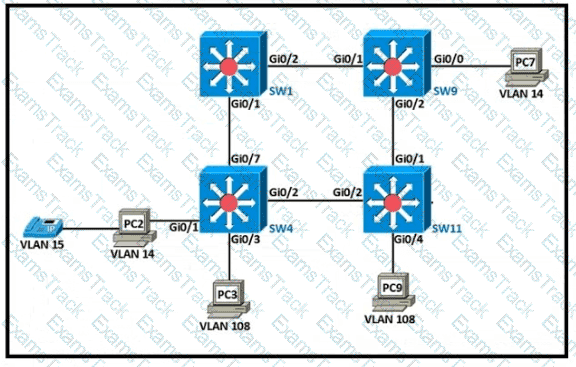
The following must be considered:
• SW1 is fully configured for all traffic
• The SW4 and SW9 links to SW1 have been configured
• The SW4 interface Gi0/1 and Gi0/0 on SW9 have been configured
• The remaining switches have had all VLANs adde d to their VLAN database
Which configuration establishes a successful ping from PC2 to PC7 without interruption to traffic flow between other PCs?
A)
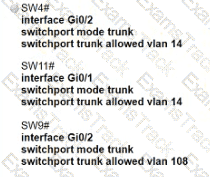
B)
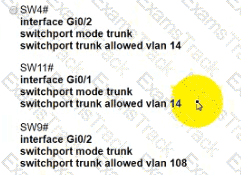
C)

D)

What is a requirement when configuring or removing LAG on a WLC?
Refer to the exhibit.
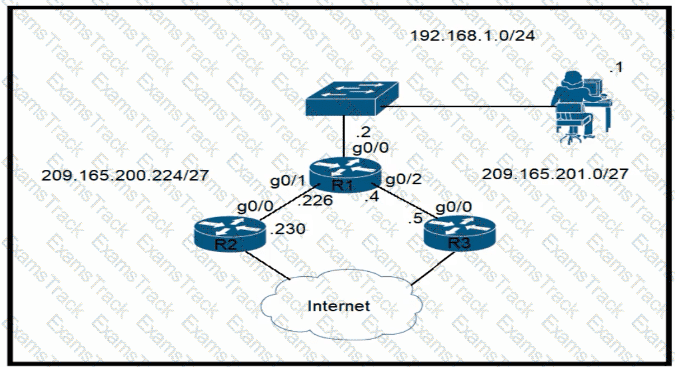
Router R1 currently is configured to use R3 as the primary route to the Internet, and the route uses the default administrative distance settings. A network engineer must configure R1 so that it uses R2 as a backup, but only if R3 goes down. Which command must the engineer configure on R1 so that it correctly uses R2 as a backup route, without changing the administrative distance configuration on the link to R3?
Refer to the exhibit.
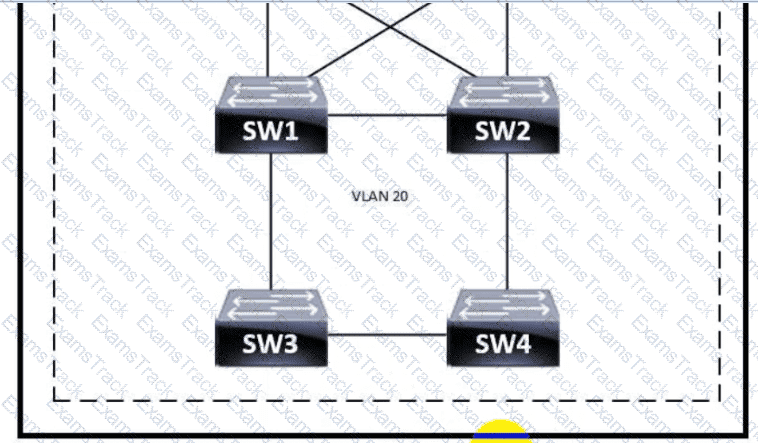
Which switch becomes the root of a spanning tree for VLAN 20 if all li links are of equal speed?

|
PDF + Testing Engine
|
|---|
|
$52.5 |
|
Testing Engine
|
|---|
|
$40.5 |
|
PDF (Q&A)
|
|---|
|
$34.5 |
Cisco Free Exams |
|---|

|