Which interface is used to send traffic to the destination network?
10.90.207.87/26 [110/1912] via F0/7
10.90.207.87/26 [110/28968] via F0/6
10.90.207.87/26 [120/14] via F0/4
10.90.207.87/26 [120/11] via F0/5
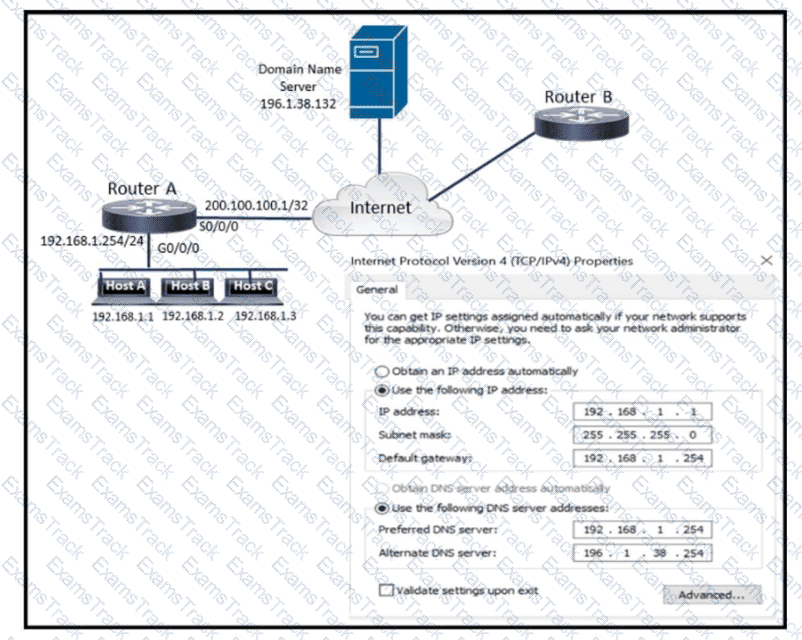
Refer to the exhibit. What is preventing host A from reaching the internet?
How does automation affect network management processes?
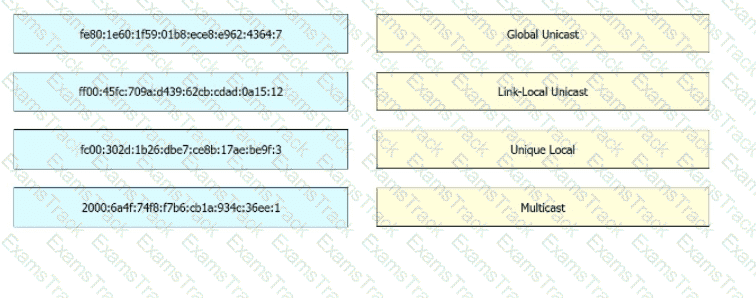
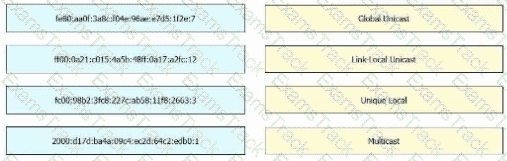
Drag and drop the IPv6 address from the left onto the type on the right.
Which combination of methods satisfies the minimum security requirements when a new multifactor authentication solution is deployed?
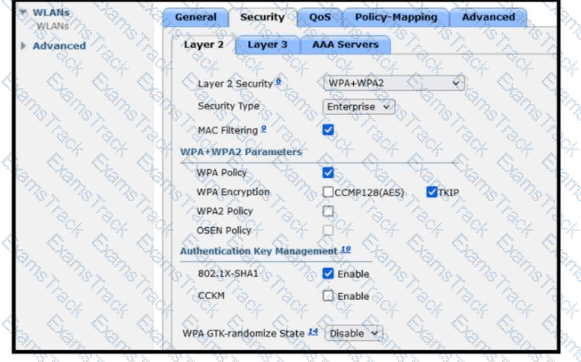
Refer to the exhibit. A guest WLAN must be created that prompts the client for a username and password on the local web page of the WLC. Which two actions must be performed on the Layer 2 tab before enabling the Authentication option on the Layer 3 tab? (Choose two.)
Drag and drop the IPv6 address from the left onto the type on the right.
What is a characteristic of encryption in wireless networks?
On workstations running Microsoft Windows, which protocol provides the default gateway for the device?
What are network endpoints?
When a switch receives a frame for a known destination MAC address, how is the frame handed?
Which technology allows multiple operating systems lo run a single physical server?
Refer to the exhibit.
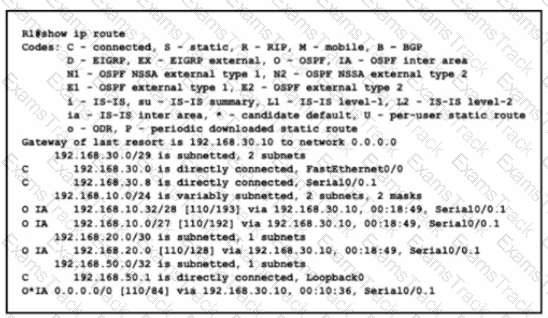
What is the metric for the route to the 192.168.10.33 host?
When deploying syslog, which severity level logs informational message?
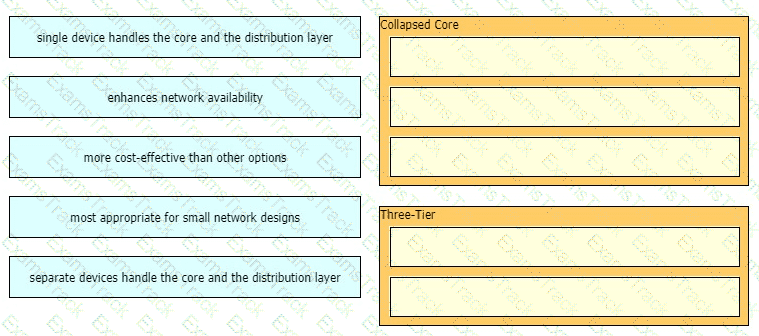
What are two descriptions of three-tier network topologies? (Choose two)
Refer to the exhibit.
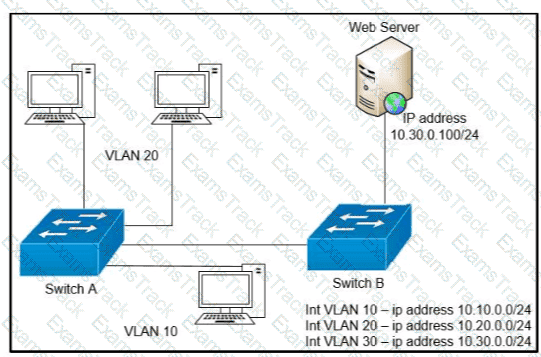
A network engineer must block access for all computers on VLAN 20 to the web server via HTTP All other computers must be able to access the web server Which configuration when applied to switch A accomplishes this task?

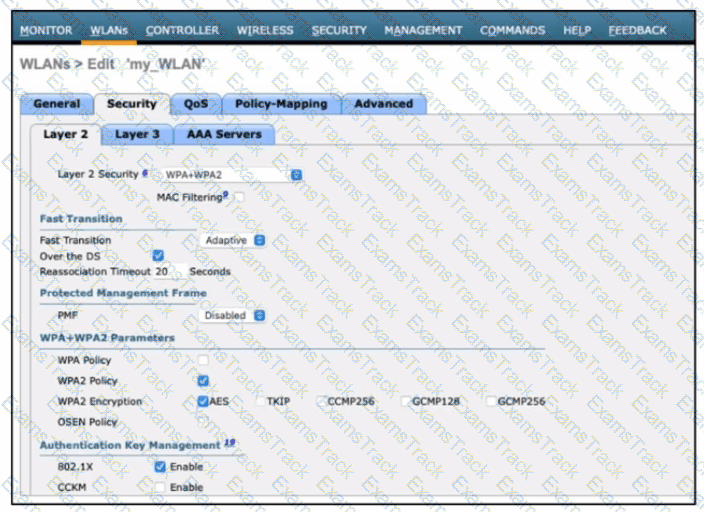
Refer to the exhibit. A network engineer is configuring a wireless LAN with Web Passthrough Layer 3 Web Policy. Which action must the engineer take to complete the configuration?
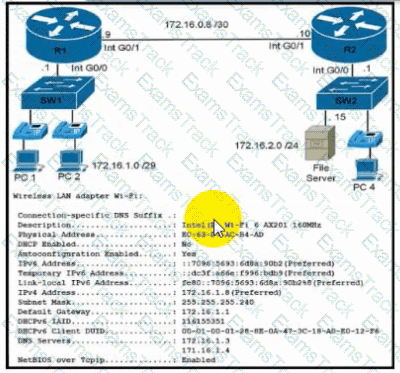
Refer to the exhibit. During initial configuration testing, the Windows workstation PC1 cannot connect with the 172.16.2.0/24 network.
Which set of actions corrects the configuration?
What is the total number of users permitted to simultaneously browse the controller management pages when using the AireOS GUI?
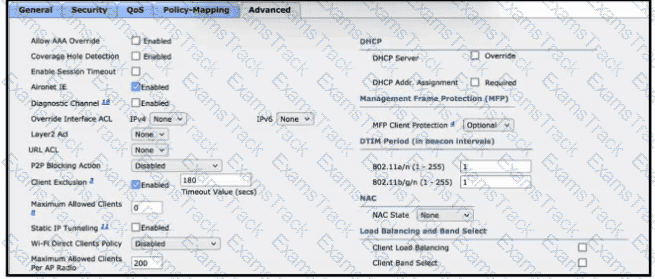
Refer to the exhibit. After a recent internal security audit, the network administrator decided to block all P2P-capable devices from the selected SSID. Which configuration setting must the administrator apply?
How are the switches in a spine-and-leaf topology interconnected?
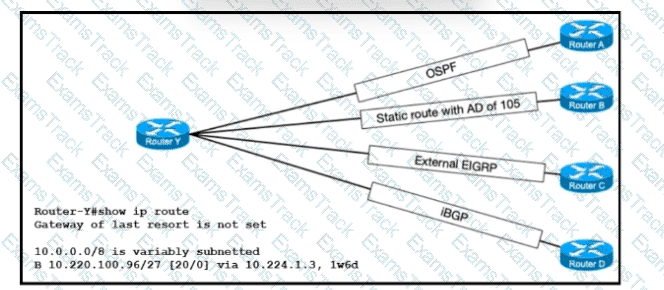
Refer to the exhibit. The route for 10.220.100.96/27 has been very unstable. The same route has four backups to routers A, B, C, and D via the respective methods. The routing protocol defaults for router Y have not been changed. When the current route for 10.220.100.96/27 becomes unavailable, which router will router Y use to route traffic to 10.220.100.96/27?
Which action does the router take as it forwards a packet through the network?
Which two capacities of Cisco DNA Center make it more extensible as compared to traditional campus device management? (Choose two)
Refer to the exhibit.
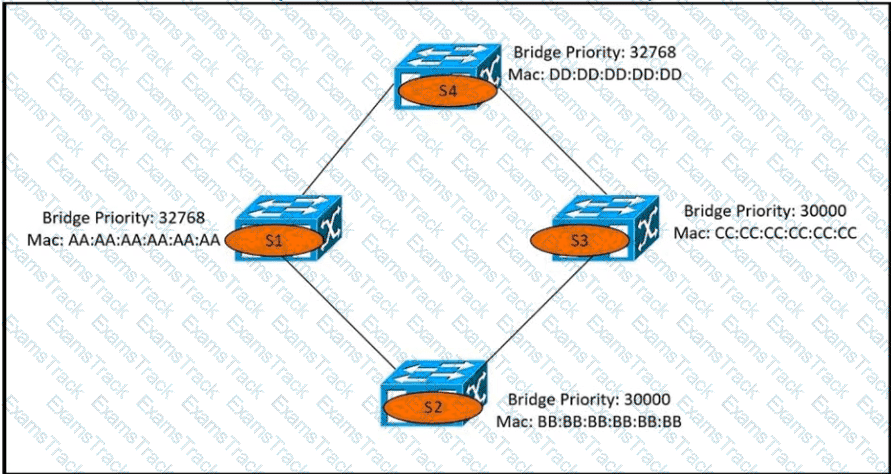
Which switch becomes the root bridge?
Which device performs stateful inspection of traffic?
Which two minimum parameters must be configured on an active interface to enable OSPFv2 to operate? (Choose two)
Which type of address is the public IP address of a NAT device?
An engineering team asks an implementer to configure syslog for warning conditions and error conditions. Which command does the implementer configure to achieve the desired result?
Which two functions are performed by the core layer in a three-tier architecture? (Choose two)
What is a DNS lookup operation?
Refer to Exhibit.
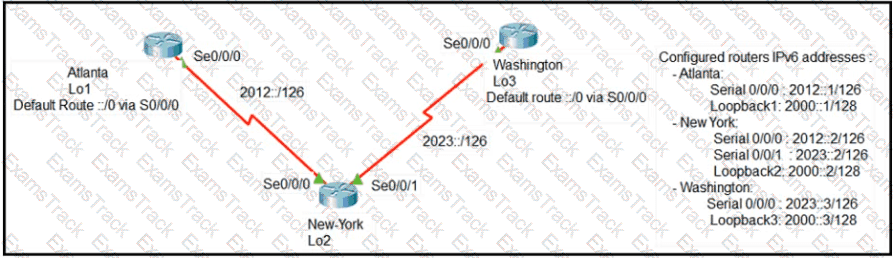
The loopback1 interface of the Atlanta router must reach the loopback3 interface of the Washington router. Which two static host routes must be configured on the NEW York router? (Choose two)
Drag and drop the SNMP components from the left onto the descriptions on the right.

Which command on a port enters the forwarding state immediately when a PC is connected to it?
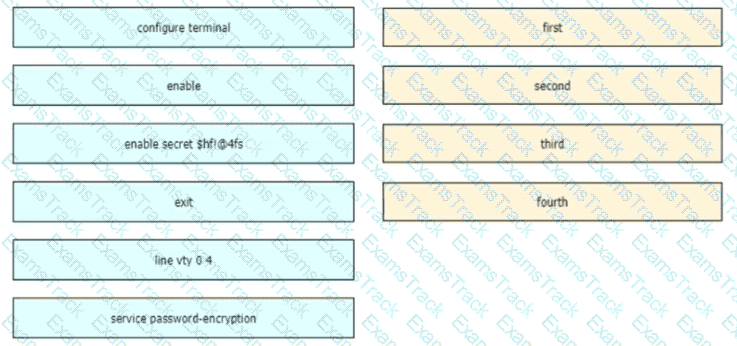
An engineer is configuring an encrypted password for the enable command on a router where the local user database has already been configured Drag and drop the configuration commands from the left into the correct sequence on the right Not all commands are used
Refer to the exhibit.
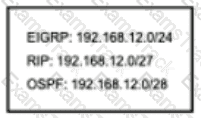
How does the router manage traffic to 192.168.12.16?
Which IPv6 address block sends packets to a group address rather than a single address?
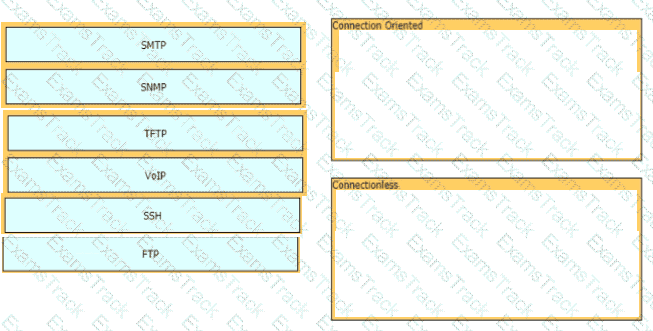
Drag and drop the network protocols from the left onto the correct transport services on the right.
What is the purpose of traffic shaping?
Refer to the exhibit.
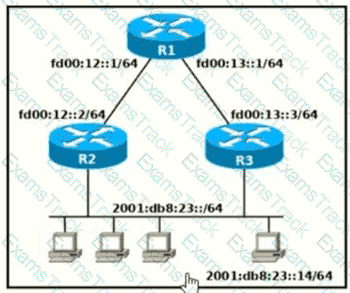
Which two commands, when configured on router R1, fulfill these requirements? (Choose two.)
Packets towards the entire network 2001:db8:2::/64 must be forwarded through router R2.
Packets toward host 2001:db8:23::14 preferably must be forwarded through R3.
What is an advantage of Cisco DNA Center versus traditional campus device management?
A network analyst is tasked with configured the date and time on a router using EXEC mode. The date must be set to 12:00am. Which command should be used?
Which two command sequences must you configure on switch to establish a Layer 3 EtherChannel with an open-standard protocol? (Choose two )
What is a DHCP client?
What are two functions of a server on a network? (Choose two)
When DHCP is configured on a router, which command must be entered so the default gateway is automatically distributed?
Refer to the exhibit.
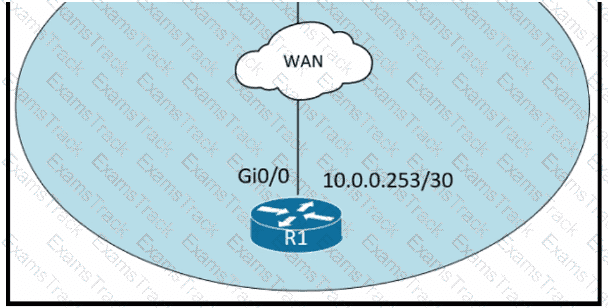
An administrator must turn off the Cisco Discovery Protocol on the port configured with address last usable address in the 10.0.0.0/30 subnet. Which command set meets the requirement?
Drag and drop the characteristics of network architectures from the left onto the type of architecture on the right.
Which mode allows access points to be managed by Cisco Wireless LAN Controllers?
Which option about JSON is true?
|
PDF + Testing Engine
|
|---|
|
$52.5 |
|
Testing Engine
|
|---|
|
$40.5 |
|
PDF (Q&A)
|
|---|
|
$34.5 |
Cisco Free Exams |
|---|

|