What is the difference between the ACK flag and the RST flag in the NetFlow log session?
A cyberattacker notices a security flaw in a software that a company is using They decide to tailor a specific worm to exploit this flaw and extract saved passwords from the software To which category of the Cyber Kill Cham model does this event belong?
A CMS plugin creates two files that are accessible from the Internet myplugin html and exploitable php A newly discovered exploit takes advantage of an injection vulnerability m exploitable php To exploit the vulnerability an HTTP POST must be sent with specific variables to exploitable php A security engineer notices traffic to the webserver that consists of only HTTP GET requests to myplugin html Which category does this activity fall under?
What does cyber attribution identify in an investigation?
What are two differences and benefits of packet filtering, stateful firewalling, and deep packet inspections? (Choose two.)
Which evasion technique is a function of ransomware?
What is the impact of false positive alerts on business compared to true positive?
An engineer needs to have visibility on TCP bandwidth usage, response time, and latency, combined with deep packet inspection to identify unknown software by its network traffic flow. Which two features of Cisco Application Visibility and Control should the engineer use to accomplish this goal? (Choose two.)
Refer to the exhibit.
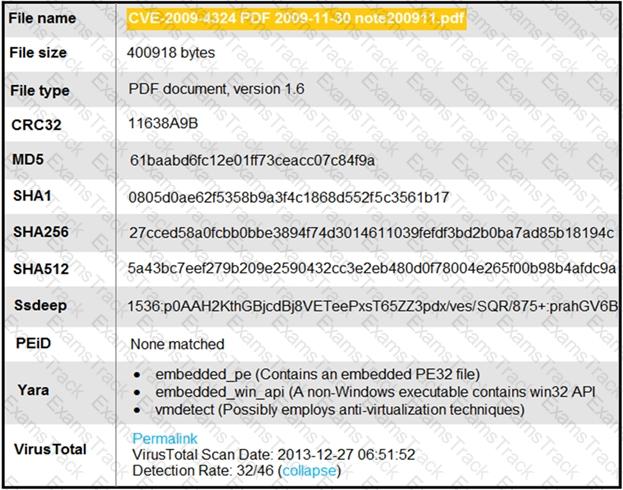
An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email. What is the state of this file?
Which technology prevents end-device to end-device IP traceability?
|
PDF + Testing Engine
|
|---|
|
$52.5 |
|
Testing Engine
|
|---|
|
$40.5 |
|
PDF (Q&A)
|
|---|
|
$34.5 |
Cisco Free Exams |
|---|

|