How can TOR impact data visibility inside an organization?
Refer to the exhibit.

A security analyst wraps up the shift and passed open ticket notes to the night shift SOC team analyst. The ticket name in question is "Investigating suspicious activity on a Windows Server’’. Which operating system components must the analyst prioritize to uncover the attacker's persistence mechanisms?
Which tool gives the ability to see session data in real time?
An analyst is using the SIEM platform and must extract a custom property from a Cisco device and capture the phrase, "File: Clean." Which regex must the analyst import?
Which process is used when IPS events are removed to improve data integrity?
Which two elements are used by the defense-in-depth strategy? (Choose two)
An engineer runs a suspicious file in a sandbox analysis tool to see the outcome. The analysis report shows that outbound callouts were made post infection.
Which two pieces of information from the analysis report are needed to investigate the callouts? (Choose two.)
What is the purpose of a host-based intrusion detection system (HIDS)?
Refer to the exhibit.
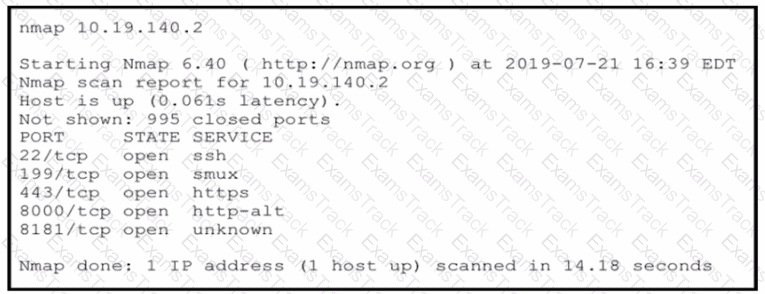
An attacker gained initial access to the company s network and ran an Nmap scan to advance with the lateral movement technique and to search the sensitive data Which two elements can an attacker identify from the scan? (Choose two.)
What is the communication channel established from a compromised machine back to the attacker?
|
PDF + Testing Engine
|
|---|
|
$52.5 |
|
Testing Engine
|
|---|
|
$40.5 |
|
PDF (Q&A)
|
|---|
|
$34.5 |
Cisco Free Exams |
|---|

|