Refer to the exhibit.
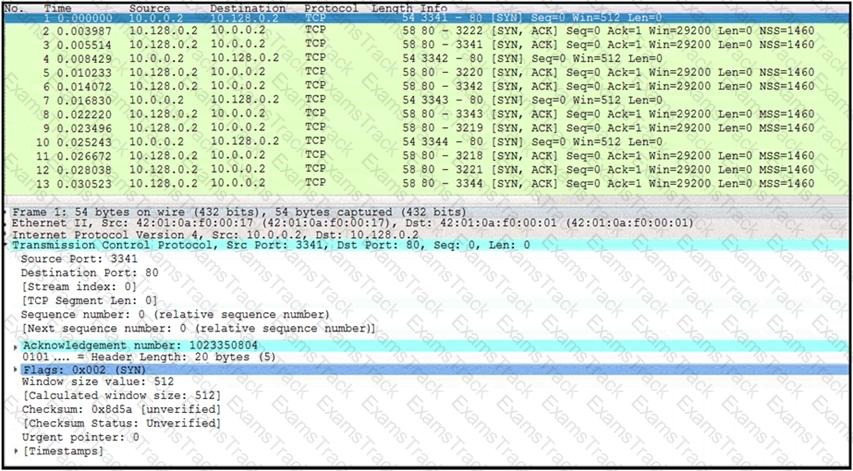
What is occurring in this network traffic?
What is the purpose of a ransomware attack?
What is a difference between tampered and untampered disk images?
Which option describes indicators of attack?

Refer to the exhibit. An employee received an email from an unknown sender with an attachment and reported it as a phishing attempt. An engineer uploaded the file to Cuckoo for further analysis. What should an engineer interpret from the provided Cuckoo report?
An engineer is analyzing a recent breach where confidential documents were altered and stolen by the receptionist. Further analysis shows that the threat actor connected an externa USB device to bypass security restrictions and steal data. The engineer could not find an external USB device Which piece of information must an engineer use for attribution in an investigation?
Refer to the exhibit.
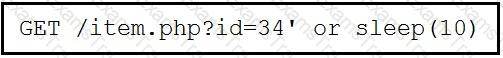
This request was sent to a web application server driven by a database. Which type of web server attack is represented?
Refer to the exhibit.
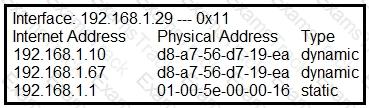
What is occurring in this network?
What is the impact of encapsulation on the network?
What is the difference between inline traffic interrogation (TAPS) and traffic mirroring (SPAN)?
|
PDF + Testing Engine
|
|---|
|
$52.5 |
|
Testing Engine
|
|---|
|
$40.5 |
|
PDF (Q&A)
|
|---|
|
$34.5 |
Cisco Free Exams |
|---|

|