Which action matches the weaponization step of the Cyber Kill Chain model?
Refer to the exhibit.
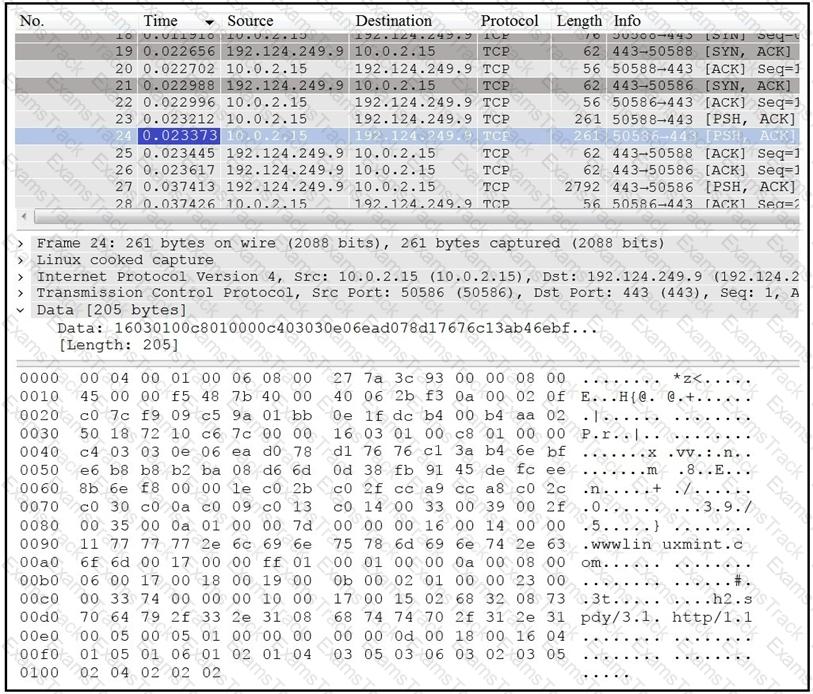
Which application protocol is in this PCAP file?
An investigator is examining a copy of an ISO file that is stored in CDFS format. What type of evidence is this file?
At which layer is deep packet inspection investigated on a firewall?
Which step in the incident response process researches an attacking host through logs in a SIEM?
How is symmetric encryption used for HTTPS connections?
A SOC analyst is investigating an incident that involves a Linux system that is identifying specific sessions. Which identifier tracks an active program?
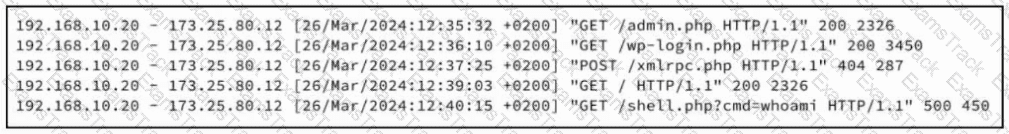
Refer to the exhibit. A security analyst examines Apache web server logs and notices the entries. Which security concern is occurring?
What is data encapsulation?
Refer to the exhibit.

Which application-level protocol is being targeted?
|
PDF + Testing Engine
|
|---|
|
$52.5 |
|
Testing Engine
|
|---|
|
$40.5 |
|
PDF (Q&A)
|
|---|
|
$34.5 |
Cisco Free Exams |
|---|

|