Which type of attack uses a botnet to reflect requests off of an NTP server to overwhelm a target?
When an event is investigated, which type of data provides the investigate capability to determine if data exfiltration has occurred?
Which signature impacts network traffic by causing legitimate traffic to be blocked?
Refer to the exhibit.
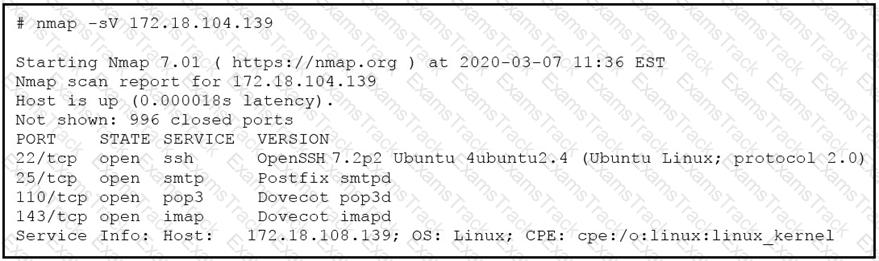
What does the output indicate about the server with the IP address 172.18.104.139?
A user received a targeted spear-phishing email and identified it as suspicious before opening the content. To which category of the Cyber Kill Chain model does to this type of event belong?
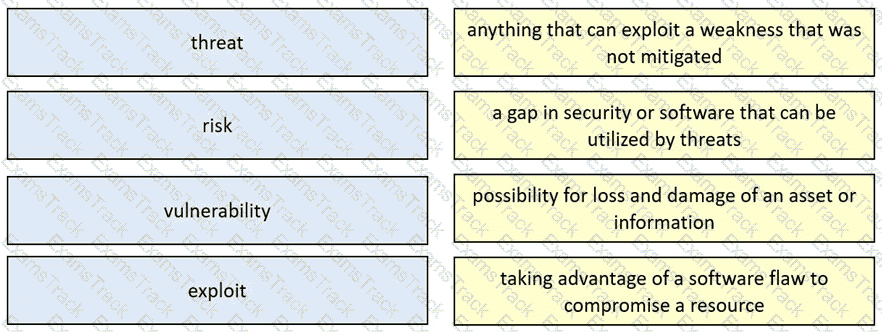
Drag and drop the security concept from the left onto the example of that concept on the right.
Refer to the exhibit.

Which type of attack is being executed?
Refer to the exhibit.

What is the outcome of the command?
Refer to the exhibit.
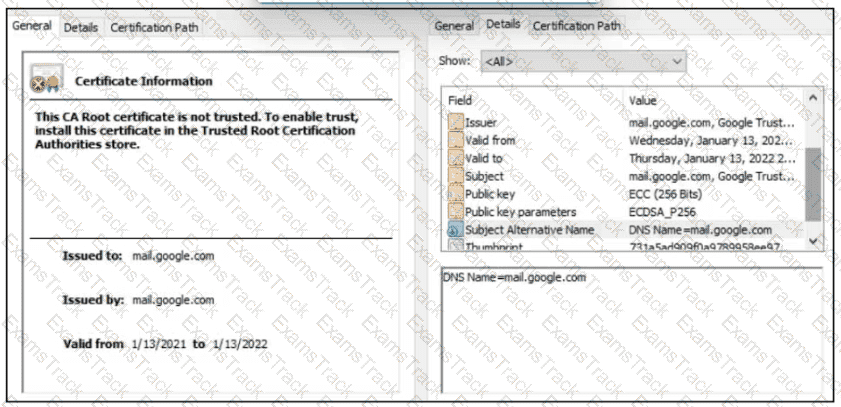
A company employee is connecting to mail google.com from an endpoint device. The website is loaded but with an error. What is occurring?
|
PDF + Testing Engine
|
|---|
|
$52.5 |
|
Testing Engine
|
|---|
|
$40.5 |
|
PDF (Q&A)
|
|---|
|
$34.5 |
Cisco Free Exams |
|---|

|