Which data capture includes payload and header information?
What is the difference between statistical detection and rule-based detection models?
What is the name of the technology that searches for and reports on known weaknesses and flaws present in an organization’s IT infrastructure?
Which items is an end-point application greylist used?
What is a difference between rule-based and role-based access control mechanisms?
What is used to maintain persistent control of an exploited device?
Which CVSS metric group identifies other components that are affected by a successful security attack?
What specific type of analysis is assigning values to the scenario to see expected outcomes?
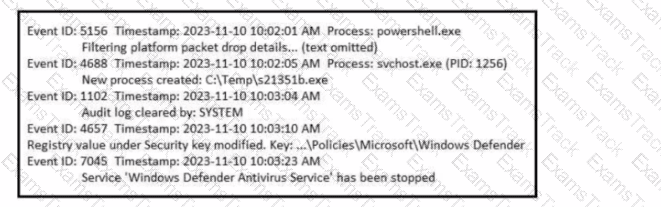
Refer to the exhibit. A SOC analyst is examining the Windows security logs of one of the endpoints. What is the possible reason for this event log?
|
PDF + Testing Engine
|
|---|
|
$52.5 |
|
Testing Engine
|
|---|
|
$40.5 |
|
PDF (Q&A)
|
|---|
|
$34.5 |
Cisco Free Exams |
|---|

|