An organization has recently adjusted its security stance in response to online threats made by a known hacktivist group.
What is the initial event called in the NIST SP800-61?
Which action should be taken if the system is overwhelmed with alerts when false positives and false negatives are compared?
Refer to the exhibit.
A company's user HTTP connection to a malicious site was blocked according to configured policy What is the source technology used for this measure'?
Which regular expression matches "color" and "colour"?
Drag and drop the security concept on the left onto the example of that concept on the right.
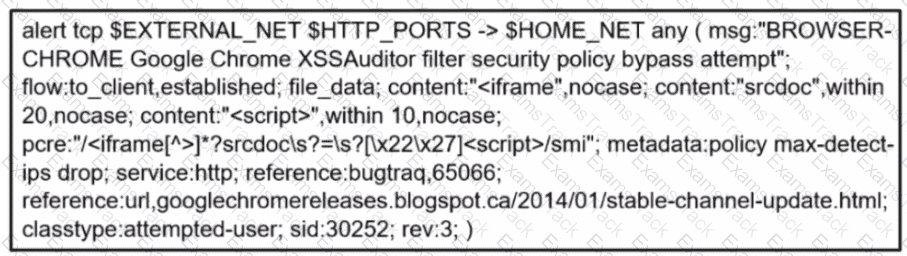
Refer to the exhibit.

Which component is identifiable in this exhibit?
An engineer received an alert affecting the degraded performance of a critical server Analysis showed a heavy CPU and memory load What is the next step the engineer should take to investigate this resource usage7
What is a difference between inline traffic interrogation and traffic mirroring?
One of the objectives of information security is to protect the CIA of information and systems. What does CIA mean in this context?
Refer to the exhibit.
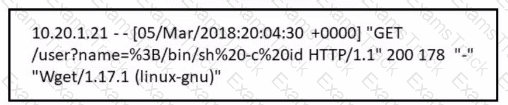
Which attack is being attempted against a web application?
|
PDF + Testing Engine
|
|---|
|
$52.5 |
|
Testing Engine
|
|---|
|
$40.5 |
|
PDF (Q&A)
|
|---|
|
$34.5 |
Cisco Free Exams |
|---|

|