Which security principle requires more than one person is required to perform a critical task?
An employee of a company receives an email with an attachment. They notice that this email is from a suspicious source, and they decide not to open the attached file. After further investigation, a security analyst concludes that this file is malware. To which category of the Cyber Kill Chain model does this event belong?
Which two elements of the incident response process are stated in NIST SP 800-61 r2? (Choose two.)
An engineer is addressing a connectivity issue between two servers where the remote server is unable to establish a successful session. Initial checks show that the remote server is not receiving an SYN-ACK while establishing a session by sending the first SYN. What is causing this issue?
How is attacking a vulnerability categorized?
Which list identifies the information that the client sends to the server in the negotiation phase of the TLS handshake?
What describes the difference when comparing attack surface and vulnerability in practice?
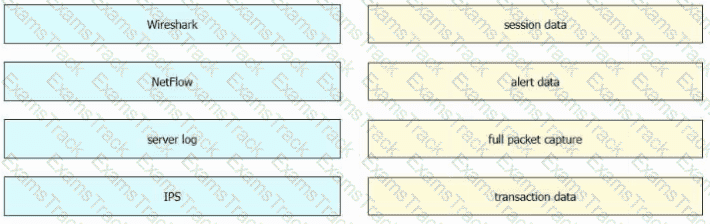
Drag and drop the data sources from the left onto the corresponding data types on the right.
What is a benefit of using asymmetric cryptography?
An organization recently experienced a major incident in which servers were attacked and data integrity was compromised. The attacker exploited a vulnerability in TLS 1.2 and performed a man-in-the-middle attack by downgrading the connection. Which action should a security specialist take to prevent similar attacks in the future?
|
PDF + Testing Engine
|
|---|
|
$52.5 |
|
Testing Engine
|
|---|
|
$40.5 |
|
PDF (Q&A)
|
|---|
|
$34.5 |
Cisco Free Exams |
|---|

|