An engineer discovered a breach, identified the threat’s entry point, and removed access. The engineer was able to identify the host, the IP address of the threat actor, and the application the threat actor targeted. What is the next step the engineer should take according to the NIST SP 800-61 Incident handling guide?
What does an attacker use to determine which network ports are listening on a potential target device?
What matches the regular expression c(rgr)+e?
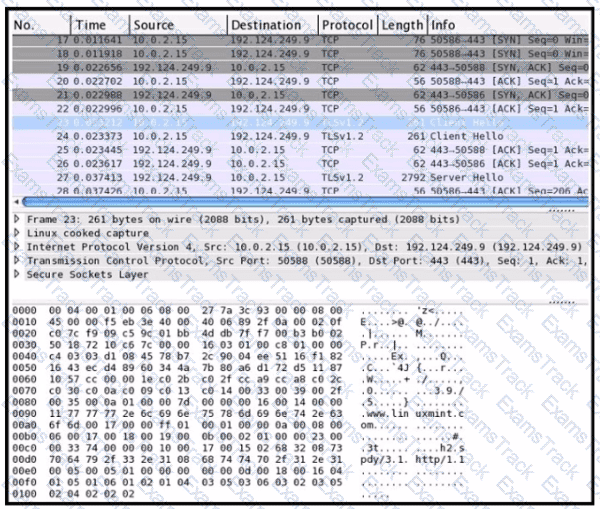
Refer to the exhibit Drag and drop the element names from the left onto the corresponding pieces of the PCAP file on the right.

Which attack is the network vulnerable to when a stream cipher like RC4 is used twice with the same key?
Refer to the exhibit.

Which type of evidence is this file?
What is the role of indicator of compromise in an investigation?
Which security technology guarantees the integrity and authenticity of all messages transferred to and from a web application?
An engineer must verify vulnerabilities found in the scanning process The engineer checks the impact of those findings to the organization and compares the results with known threats inside organization What is the benefit of knowing this information?
Refer to the exhibit.
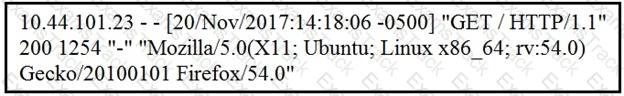
What does the message indicate?
|
PDF + Testing Engine
|
|---|
|
$52.5 |
|
Testing Engine
|
|---|
|
$40.5 |
|
PDF (Q&A)
|
|---|
|
$34.5 |
Cisco Free Exams |
|---|

|