What is a difference between a threat and a vulnerability?
What is the difference between the ACK flag and the RST flag?
What is the difference between mandatory access control (MAC) and discretionary access control (DAC)?
A company had a recent breach and lost confidential data to a competitor. An internal investigation found out that a new junior accounting specialist logged in to the accounting server with their user ID and stole confidential data. The junior accounting specialist denies the action and claims that the attempt was done by someone else. During court proceedings, the company presents logs and CCTV camera recordings that show the malicious insider in action. Which type of evidence has the company presented?
A security consultant must change the identity access management model fof their organization The new approach will put responsibility on the owner, who will decide whichusers will have access to which resources Which low-cost model must be used for this purpose?
What causes events on a Windows system to show Event Code 4625 in the log messages?
Refer to the exhibit.
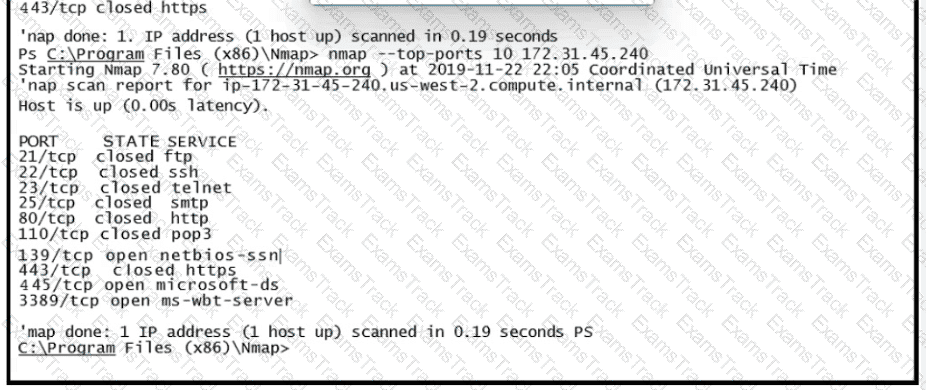
What does this output indicate?
An employee reports that someone has logged into their system and made unapproved changes, files are out of order, and several documents have been placed in the recycle bin. The security specialist reviewed the system logs, found nothing suspicious, and was not able to determine what occurred. The software is up to date; there are no alerts from antivirus and no failed login attempts. What is causing the lack of data visibility needed to detect the attack?
An analyst discovers that a legitimate security alert has been dismissed. Which signature caused this impact on network traffic?
Refer to the exhibit.
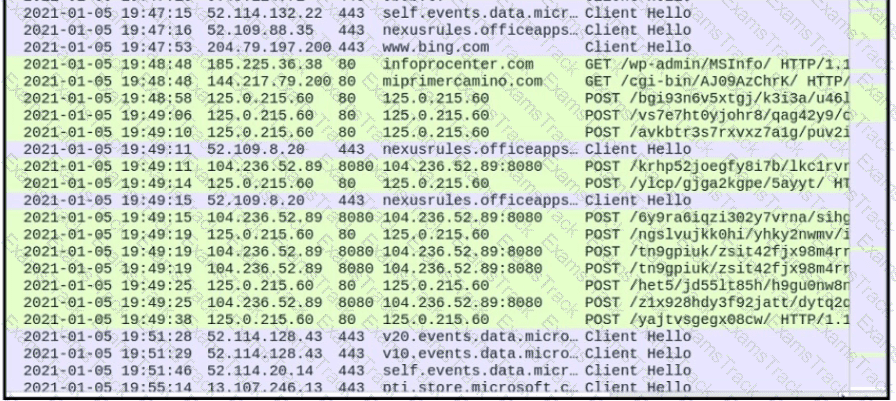
What is occurring?
|
PDF + Testing Engine
|
|---|
|
$52.5 |
|
Testing Engine
|
|---|
|
$40.5 |
|
PDF (Q&A)
|
|---|
|
$34.5 |
Cisco Free Exams |
|---|

|