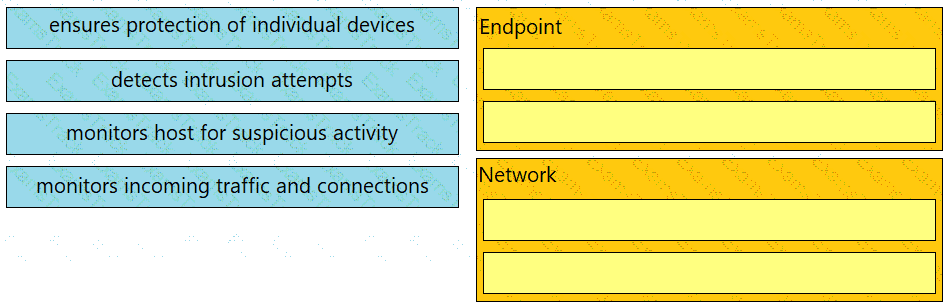
Drag and drop the uses on the left onto the type of security system on the right.
Which security technology allows only a set of pre-approved applications to run on a system?
A multinational organization uses a complex network infrastructure incorporating multiple cloud services, diverse endpoints, and distributed networks with several security devices. Which challenge will the security team face when ensuring robust data visibility for effective threat detection and response?
What are two differences between tampered disk images and untampered disk images'? (Choose two.)
Which regex matches only on all lowercase letters?
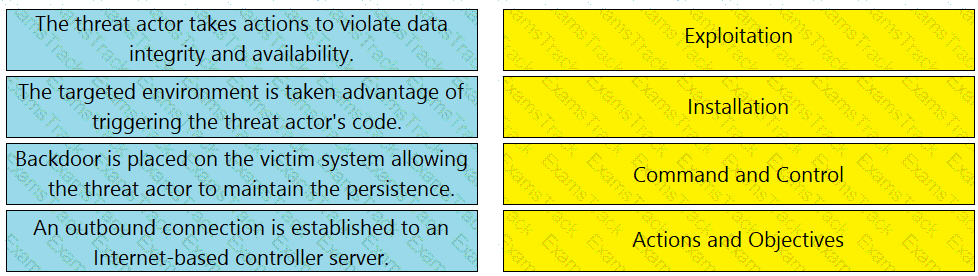
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.
Which type of access control depends on the job function of the user?
Refer to the exhibit.
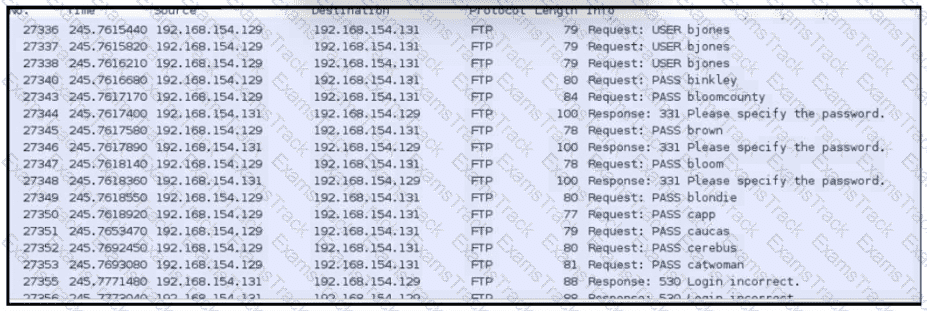
An analyst was given a PCAP file, which is associated with a recent intrusion event in the company FTP server Which display filters should the analyst use to filter the FTP traffic?
Refer to the exhibit.
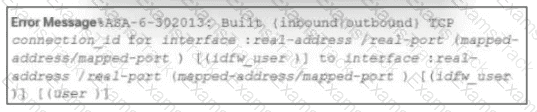
During the analysis of a suspicious scanning activity incident, an analyst discovered multiple local TCP connection events Which technology provided these logs?
An engineer receives a security alert that traffic with a known TOR exit node has occurred on the network. What is the impact of this traffic?
|
PDF + Testing Engine
|
|---|
|
$52.5 |
|
Testing Engine
|
|---|
|
$40.5 |
|
PDF (Q&A)
|
|---|
|
$34.5 |
Cisco Free Exams |
|---|

|