An engineer must extend Layer 2 Between two campus sites connected through an MPLS backbone that encapsulates Layer 2 and Layer 3 data Which action must the engineer perform on the routers to accomplish this task?
Refer to the exhibit.

Which type of DDoS attack will be mitigated by this configuration?
What is the primary role of a BR router in a 6rd environment?

Refer to the exhibit. A large enterprise streams training videos from a server connected to R4 to hosts connected to R5. PIM-SM is configured in the network using IGMPv2, with R2 serving as the RP. OSPF is configured in the network to support IGP routing, and the network uses BGP to access the internet through R3. The network engineering team must migrate the network to SSM.
Which action must the team take to begin the migration?
Refer to the exhibit.
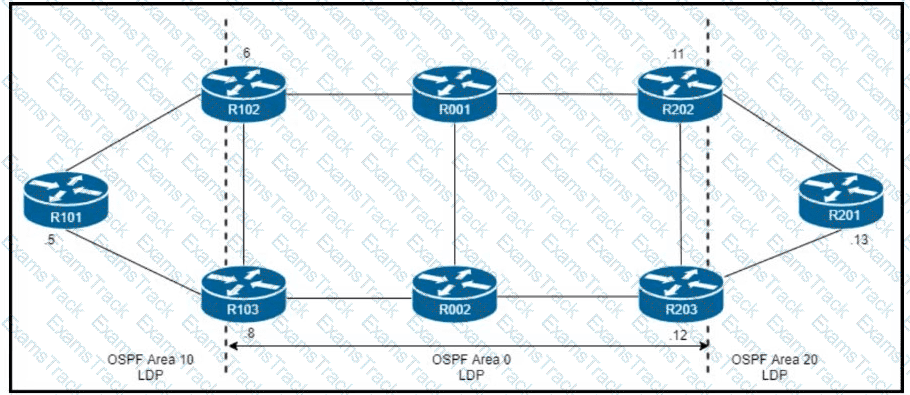
R101 is peering with R102 and R103, and R201 is peering with R202 and R203 using iBGP Labeled Unicast address families. The OSPF area 0 border routers are in a full iBGP Labeled Unicast mesh, and VPNv4 routes are exchanged directly between PE routers R101 and R201 through iBGP Which address family-level configuration must be applied on ABR R102 on ABR R102 to support a Unified MPLS routing architecture with partitioned IGP domains?
A)

B)
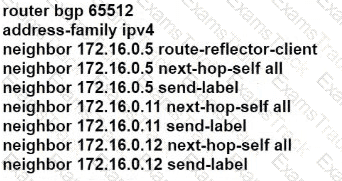
C)
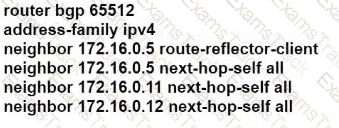
D)
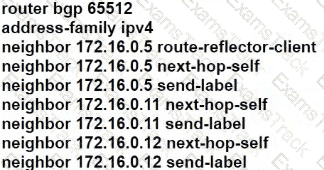
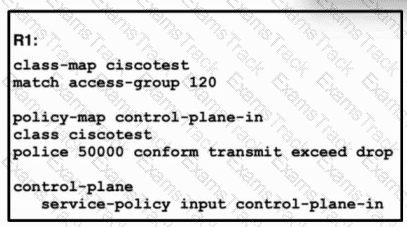
Refer to the exhibit. A network engineer installed router R1 as the new core router and must secure the control plane. The configuration has been applied, and now the engineer is creating ACL 120. Only hosts 192.168.1.1 and 192.168.2.2 should be allowed to access the router using Telnet. All other hosts should be rate-limited, with excess traffic dropped. Which configuration accomplishes this goal?
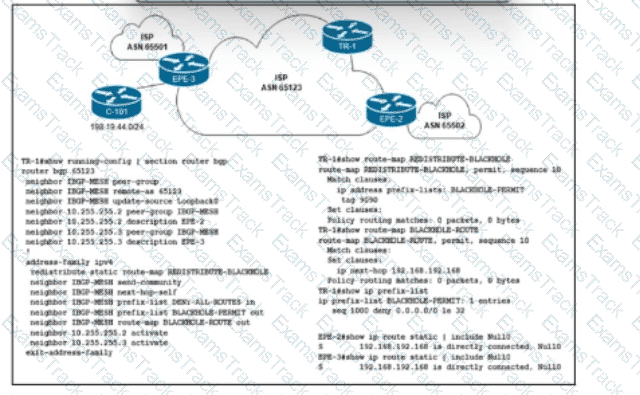
Refer to the exhibit. Customer C-101 in ASN 65123 requested that the ISP blackholes a host route 198.19.44.195, to which the customer is receiving a significant amount of malicious traffic. Which configuration must the network engineer implement on the trigger router TR-1 to fulfill the request without affecting other IP destinations in the customer's block?
Which type of attack is an application attack?
Which configuration modifies Local Packet Transport Services hardware policies?
A)
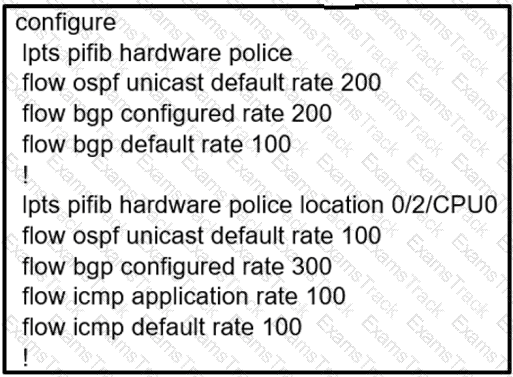
B)

C)
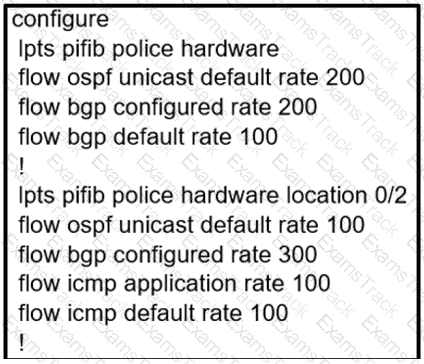
D)

Refer to the exhibit.
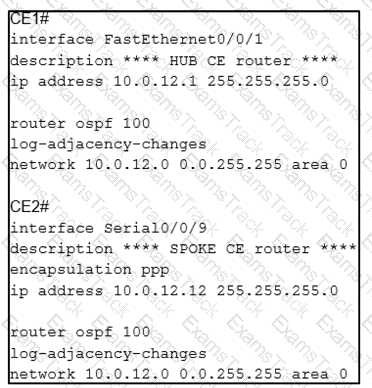
A network engineer is configuring customer edge routers to finalize a L2VPN over MPLS deployment Assume that the AToM L2VPN service that connects the two CEs is configured correctly on the service provider network Which action causes the solution to fail?
Refer to the exhibit:
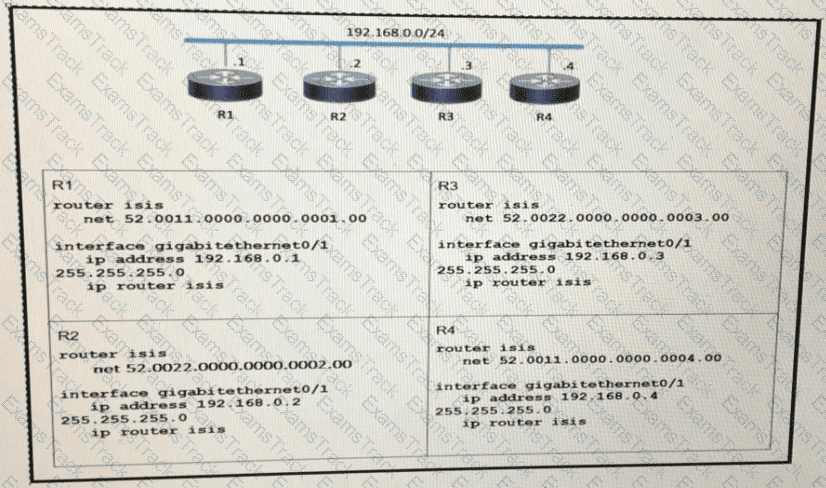
Which two statements about the ISIS topology are true? (Choose two.)
Refer to the exhibit.

AN engineer is configuring segment routing on an ISP to simplify traffic engineering and management across network domains. What should the engineer do to complete the implementation of segment routing?
Refer to the exhibit.

An engineer implemented OSPF neighbor relationship on an IOS device. Which configuration must be applied to get the OR/BOR election removed from interfaces running OSPF?
Which statement describes the advantage of a Multi-Layer control plane?
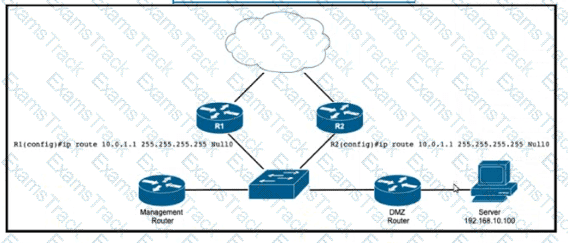

Refer to the exhibit. EIGRP a running across the core lo exchange Internal routes, and each router maintains 6GP adjacency with the other routers on the network. An operator has configured static routes on the edge routers R1 and R2 for IP address 10.0.1.1. which is used as a black hole route as shown. Which configuration should the operator Implement to me management rouler to create a route map that will redistribute lagged static routes into BGP and create a static route to blackhole traffic with tag 777 that Is destined to server at 192.168.10.100?

|
PDF + Testing Engine
|
|---|
|
$52.5 |
|
Testing Engine
|
|---|
|
$40.5 |
|
PDF (Q&A)
|
|---|
|
$34.5 |
Cisco Free Exams |
|---|

|