How does Cisco MPLS TE use OSPF extensions to allow for optimized transit between a headend router and a destination router?
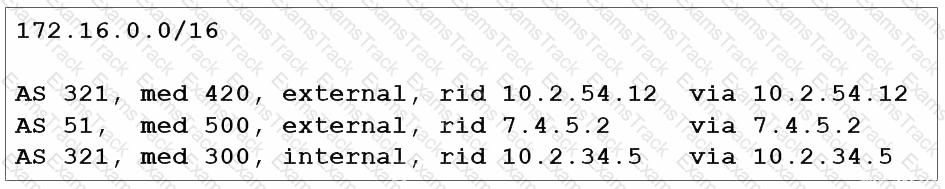
Refer to the exhibit. Tier 2 ISP A on AS 653 is connected to two Tier 1 ISPs on AS 321 and AS 51 respectively. The network architect at ISP A is planning traffic flow inside the network to provide predictable network services. Cisco Express Forwarding is disabled on the edge router. How should the architect implement BGP to direct all traffic via the Tier 1 ISP with next-hop 7.4.5.2?
Which statement about TLS is accurate when using RESTCONF to write configurations on network devices'?
Which two features will be used when defining SR-TE explicit path hops if the devices are using IP unnumbered interfaces? (Choose two.)
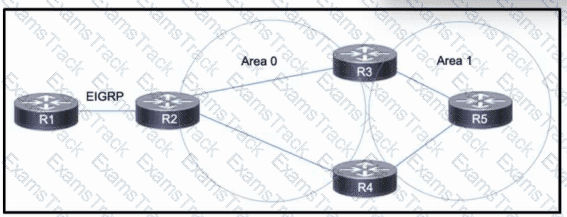
Refer to the exhibit. Company A is running OSPF within its network, comprised of routers R2, R3, R4, and R5 and consisting of two areas. Company A just acquired Company B, which uses EIGRP on its own R1. R1 has several routes in its routing table. The network engineering team at Company A needs access to the Company B network to manage network devices there, but each company will otherwise operate independently. R2 will serve as the ASBR between the two networks. Which action must the team take to reduce the number of EIGRP routes received on R2 and include only the necessary routes in the routing table?

Refer to the exhibit. A network operator working for a private telecommunication company with an employee id: 7138: 13:414 just added new users to the network, which resides in VLANs connected to routers R1 and R4. The engineer now must configure the network so that routers R1 and R4 share routes to the VLANs, but routers R2 and R3 are prevented from including the routes in their routing tables. Which configuration must the engineer apply to R4 to begin implementing the request?
Refer to the exhibit.
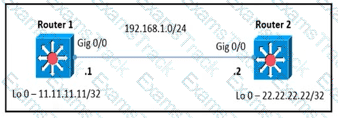
Router 1 and router 2 are running OSPF Area 0. The router logs on both routers show that the LDP link has flapped. Which configuration must the engineer apply to the two routers to implement session protection on the link?

A network architect décides to expand the scope of the multicast deployment within the company network the network is already using PlM-SM with a static RP that supports a high-bandwidth. video-based training application that s heavily used by the employees, but excessive bandwidth usage is a concern How must the engineer update the network to provide a more efficient multicast implementation'?
Network devices in the core layer use different IGPs, and the network is split into several areas. The engineer must use a NETCONF operation to load a full interface configuration on multiple Cisco devices to ensure that they meet company standards. The devices must work over SSH from the Linux jump server. Which action meets the configuration requirements?
What is the purpose of microsegments in the SRv6 architecture?
Which configuration enables BGP FlowSpec client function and installation of policies on all local interfaces?
A)

B)

C)

D)

Refer to the exhibit.
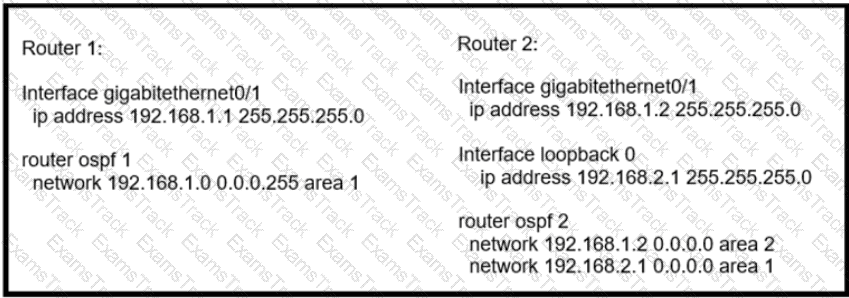
Router 1 is missing the route for the router 2 loopback 0. What should the engineer change to fix the problem?
An engineer is setting up overlapping VPNs to allow VRF ABC and XYZ to communicate with VRF CENTRAL but wants to make sure that VRF ABC and XYZ cannot communicate. Which configuration accomplishes these objectives?




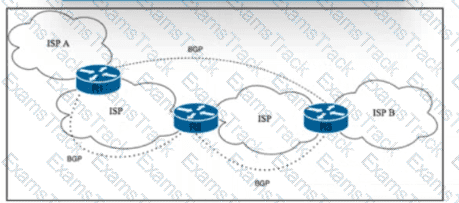
Refer to the exhibit. Tier 1 ISP A is connected to small Tier 3 ISP B. The EBGP routing protocol is used for route exchange. The networking team at ISP A noticed the flapping of BGP sessions with ISP B. The team decides to Improve stability on the network by suppressing the subnet for 30 minutes when a session begins to flap. Which action must the team perform to meet this goal?
Refer to the exhibit.

A network engineer is implementing a standard customer route-policy on ASBR1 with these requirements:
• It must accept only customer-assigned prefixes
• It must preserve customer advertised BGP communities
• It must set the local-preference to 110 for all prefixes
• It must attach the ORIGINATION-PE and LOCAL-CITY communities to all accepted prefixes.
Which route policy must the engineer implement on ASBR1 to satisfy the requirements?

|
PDF + Testing Engine
|
|---|
|
$52.5 |
|
Testing Engine
|
|---|
|
$40.5 |
|
PDF (Q&A)
|
|---|
|
$34.5 |
Cisco Free Exams |
|---|

|