An engineer is configuring a Cisco IPS to protect the network and wants to test a policy before deploying it. A copy of each incoming packet needs to be monitored while traffic flow remains constant. Which IPS mode should be implemented to meet these requirements?
A network engineer must configure the cabling between a Cisco Secure Firewall Threat Defense appliance and a network so the Secure Firewall Threat Defense appliance performs inline to analyze and tune generated intrusion events before going live. Which Secure Firewall Threat Defense interface mode must the engineer use?
A company is deploying intrusion protection on multiple Cisco FTD appliances managed by Cisco FMC. Which system-provided policy must be selected if speed and detection are priorities?
Which default action setting in a Cisco FTD Access Control Policy allows all traffic from an undefined application to pass without Snort Inspection?
What is a feature of Cisco AMP private cloud?
Which limitation applies to Cisco Firepower Management Center dashboards in a multidomain environment?
Which two routing options are valid with Cisco Firepower Threat Defense? (Choose two.)
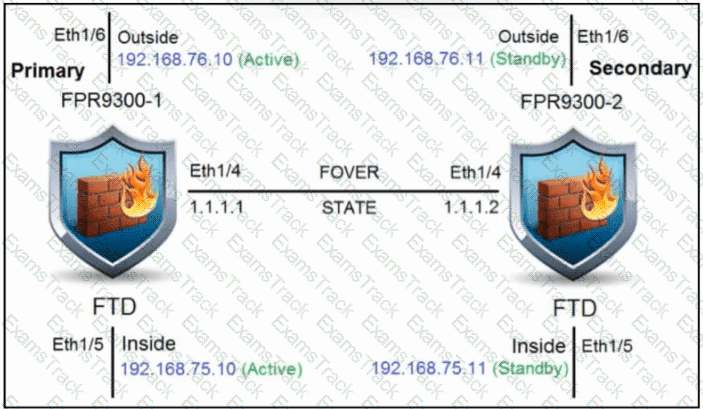
Refer to the exhibit. An engineer is configuring a high-availability solution that has the hardware devices and software versions:
two Cisco Secure Firewall 9300 Security Appliances with FXOS SW 2.0(1.23)
software Cisco Secure Firewall Threat Defense 6.0.1.1 (build 1023) on both appliances
one Cisco Secure Firewall Management Center with SW 6.0.1.1 (build 1023)
Which condition must be met to complete the high-availability configuration?
An engineer is configuring a Cisco Secure Firewall Threat Defence device managed by Cisco Secure Firewall Management Centre. The device must have SSH enabled and the accessible from the inside interface for remote administration. Which type of policy must the engineer configure to accomplish this?
An engineer must deploy a Cisco FTD device. Management wants to examine traffic without requiring network changes that will disrupt end users. Corporate security policy requires the separation of management traffic from data traffic and the use of SSH over Telnet for remote administration. How must the device be deployed to meet these requirements?
|
PDF + Testing Engine
|
|---|
|
$61.25 |
|
Testing Engine
|
|---|
|
$47.25 |
|
PDF (Q&A)
|
|---|
|
$40.25 |
Cisco Free Exams |
|---|

|