A network engineer is deploying a Cisco Firepower 4100 appliance and must configure a multi-instance environment for high availability. Drag and drop me actions from the left into sequence on the right far this configuration.

After using Firepower for some time and learning about how it interacts with the network, an administrator is trying to correlate malicious activity with a user Which widget should be configured to provide this visibility on the Cisco Firepower dashboards?
An engineer must configure a new identity policy in Cisco Firepower Management Center. Active authentication must be configured by using a Kerberos connection. Which two realms must be configured? (Choose two.)
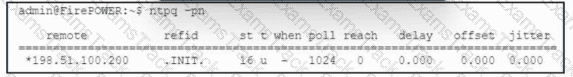
Refer to the exhibit. A security engineer views the health alerts in Cisco Secure Firewall Management Center by using the Health Monitor in the web interface. One of the alerts shows an appliance as critical because the Time Synchronization module status is out of sync. To troubleshoot the issue, the engineer runs the ntpq command in Secure Firewall Management Center. The output is shown in the exhibit. Which action must the security engineer take next to resolve the issue?
A network administrator notices that inspection has been interrupted on all non-managed interfaces of a device. What is the cause of this?
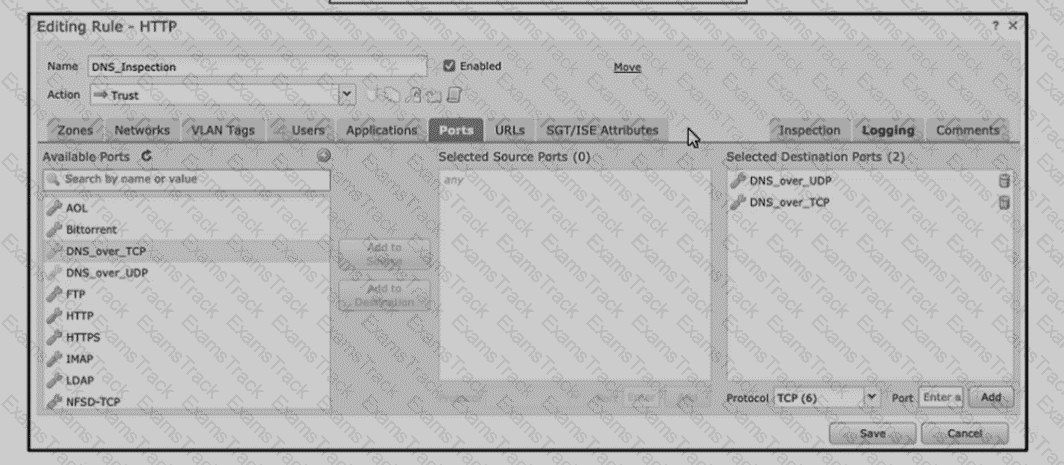
Refer to the exhibit An engineer is modifying an access control pokey to add a rule to inspect all DNS traffic that passes through the firewall After making the change and deploying thepokey they see that DNS traffic is not bang inspected by the Snort engine What is the problem?
On the advanced tab under inline set properties, which allows interfaces to emulate a passive interface?
An engineer is configuring a custom intrusion rule on Cisco FMC. The engineer needs the rule to search the payload or stream for the string "|45 5* 26 27 4 0A|*. Which Keyword must the engineer use with this stung lo create an argument for packed inspection?
An engineer is configuring a custom application detector for HTTP traffic and wants to import a file that was provided by a third party. Which type of flies are advanced application detectors creates and uploaded as?
In which two ways do access control policies operate on a Cisco Firepower system? (Choose two.)
|
PDF + Testing Engine
|
|---|
|
$61.25 |
|
Testing Engine
|
|---|
|
$47.25 |
|
PDF (Q&A)
|
|---|
|
$40.25 |
Cisco Free Exams |
|---|

|