Which component is needed to perform rapid threat containment with Cisco FMC?
An engineer is troubleshooting application failures through a FTD deployment. While using the FMC CLI. it has been determined that the traffic in question is not matching the desired policy. What should be done to correct this?
What is an advantage of adding multiple inline interface pairs to the same inline interface set when deploying an asynchronous routing configuration?
A security engineer must integrate an external feed containing STIX/TAXII data with Cisco FMC. Which feature must be enabled on the Cisco FMC to support this connection?
Which Firepower feature allows users to configure bridges in routed mode and enables devices to perform Layer 2 switching between interfaces?
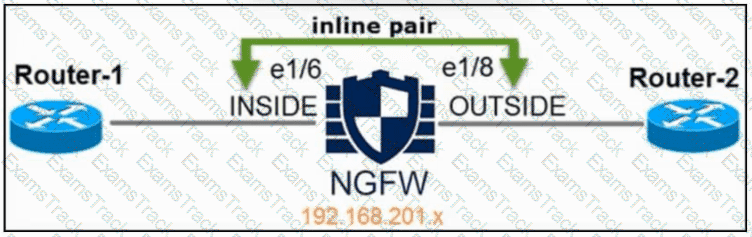
Refer to the exhibit. An engineer is configuring an instance of Cisco Secure Firewall Threat Defense with interfaces in IPS Inline Pair mode. What must be configured on interface e1/6 to accomplish the requirement?
A company has many Cisco FTD devices managed by a Cisco FMC. The security model requires that access control rule logs be collected for analysis. The security engineer is concerned that the Cisco FMC will not be able to process the volume of logging that will be generated. Which configuration addresses this concern?
Which feature within the Cisco FMC web interface allows for detecting, analyzing and blocking malware in network traffic?
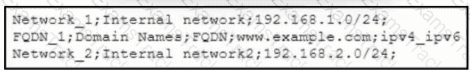
Refer to the exhibit. An engineer must import three network objects into the Cisco Secure Firewall Management Center by using a CSV file. Which header must be configured in the CSV file to accomplish the task?
A network administrator wants to block traffictoa known malware site athttps://www.badsite.comand all subdomains while ensuring no packets from any internal client are sent to that site. Which type of policy must the network administrator use to accomplish this goal?
|
PDF + Testing Engine
|
|---|
|
$61.25 |
|
Testing Engine
|
|---|
|
$47.25 |
|
PDF (Q&A)
|
|---|
|
$40.25 |
Cisco Free Exams |
|---|

|