A network engineer is logged into the Cisco AMP for Endpoints console and sees a malicious verdict for an identified SHA-256 hash. Which configuration is needed to mitigate this threat?
An engineer is integrating Cisco Secure Endpoint with Cisco Secure Firewall Management Center in high availability mode. Malware events detected by Secure Endpoint must also be
received by Secure Firewall Management Center and public cloud services are used. Which two configurations must be selected on both high availability peers independently? (Choose two.)
Which two considerations must be made when deleting and re-adding devices while managing them via Cisco FMC (Choose two).
When a Cisco FTD device is configured in transparent firewall mode, on which two interface types can an IP address be configured? (Choose two.)
An engineer must configure a correlation policy in Cisco Secure Firewall Management Center to detect when an IP address from an internal network communicates with a known malicious host. Connections made by the internal IP addresses must be tracked, and an external dynamic list must be used for the condition. Which type of event must the engineer configure on the correlation policy?
How many report templates does the Cisco Firepower Management Center support?
An engineer must configure email notifications on Cisco Secure Firewall Management Center. TLS encryption must be used to protect the messages from unauthorized access. The engineer adds the IP address of the mail relay host and must set the port number. Which TCP port must the engineer use?
Which action must be taken to configure an isolated bridge group for IRB mode on a Cisco Secure Firewall device?
A network administrator reviews me attack risk report and notices several Low-Impact attacks. What does this type of attack indicate?
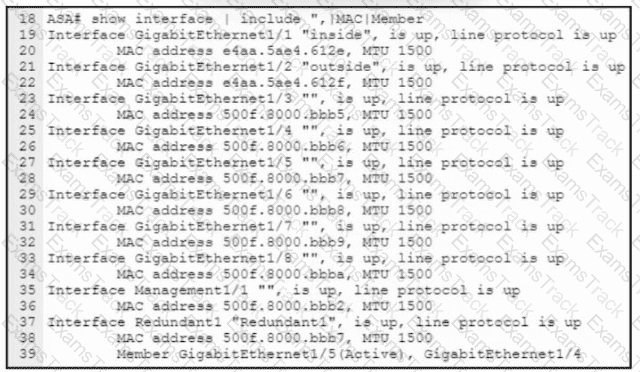
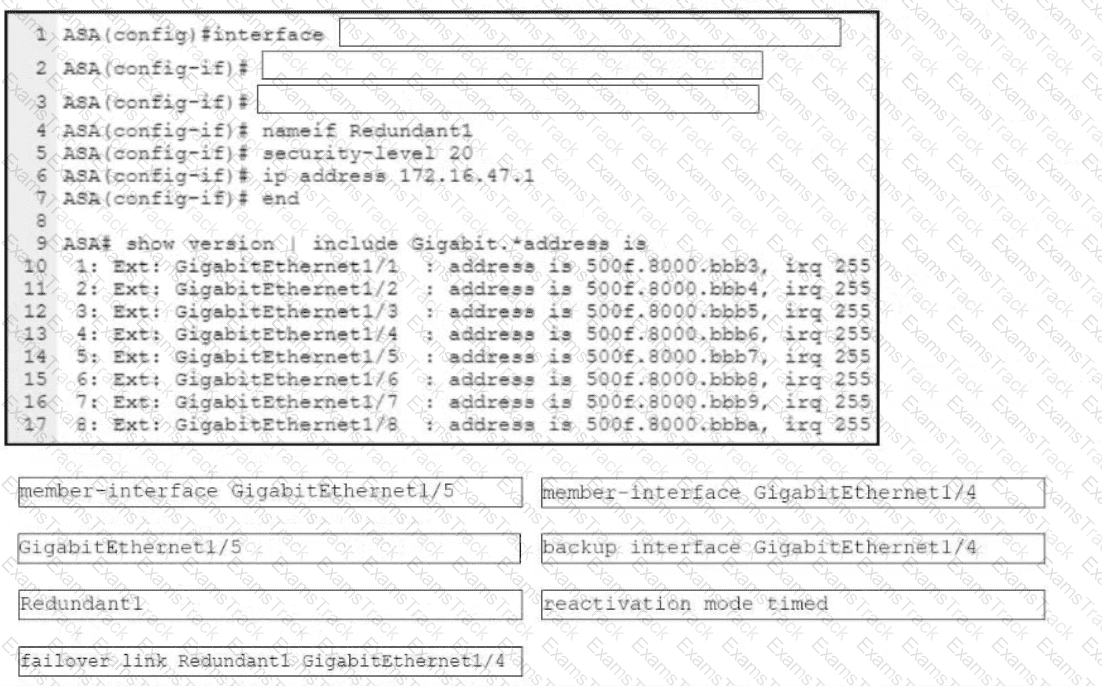
Refer to the exhibit. An engineer must configure a connection on a Cisco ASA Firewall with a Cisco Secure Firewall Services Module to ensure that the secondary interface takes over all the functions of the primary interface if the primary interface fails. Drag and drop the code snippets from the bottom onto the boxes in the CLI commands to configure the failover. Not all options are used.
|
PDF + Testing Engine
|
|---|
|
$61.25 |
|
Testing Engine
|
|---|
|
$47.25 |
|
PDF (Q&A)
|
|---|
|
$40.25 |
Cisco Free Exams |
|---|

|