Which technique changes protocols at random during a session?
What is used to orchestrate, coordinate, and control clusters of containers?
SecOps consists of interfaces, visibility, technology, and which other three elements? (Choose three.)
What is the primary security focus after consolidating data center hypervisor hosts within trust levels?
Which component of cloud security uses automated testing with static application security testing (SAST) to identify potential threats?
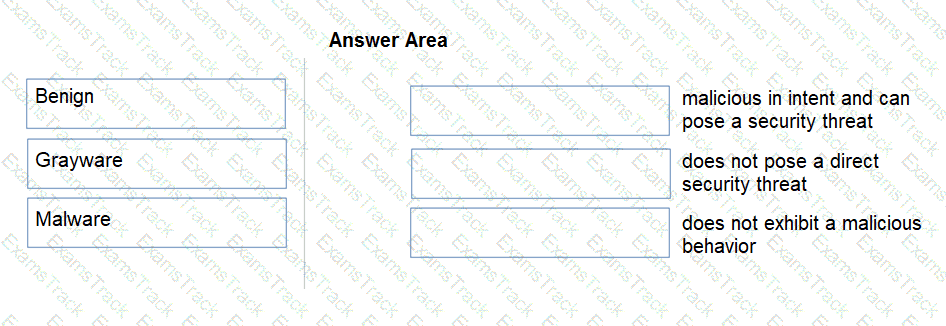
Match the Palo Alto Networks WildFire analysis verdict with its definition.
You received an email, allegedly from a bank, that asks you to click a malicious link to take action on your account.
Which type of attack is this?
Which network device breaks networks into separate broadcast domains?
Which characteristic of advanced malware makes it difficult to detect?
Which internet of things (loT) connectivity technology operates on the 2.4GHz and 5GHz bands, as well as all bands between 1 and 6GHz when they become available for 802.11 use. at ranges up to 11 Gbit/s?
|
PDF + Testing Engine
|
|---|
|
$49.5 |
|
Testing Engine
|
|---|
|
$37.5 |
|
PDF (Q&A)
|
|---|
|
$31.5 |
Paloalto Networks Free Exams |
|---|

|