In SecOps, what are two of the components included in the identify stage? (Choose two.)
What is the ptrpose of automation in SOAR?
Routing Information Protocol (RIP), uses what metric to determine how network traffic should flow?
An administrator finds multiple gambling websites in the network traffic log.
What can be created to dynamically block these websites?
What are two functions of an active monitoring system? (Choose two.)
Which component of the AAA framework regulates user access and permissions to resources?
Which endpoint product from Palo Alto Networks can help with SOC visibility?
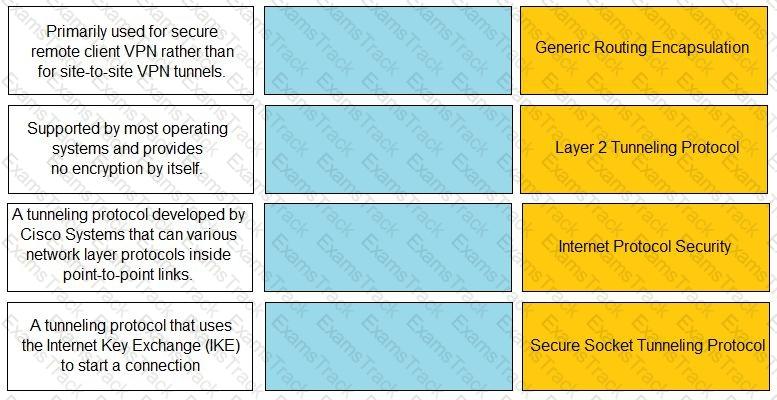
Match the description with the VPN technology.
Which organizational function is responsible for security automation and eventual vetting of the solution to help ensure consistency through machine-driven responses to security issues?
On an endpoint, which method should you use to secure applications against exploits?
|
PDF + Testing Engine
|
|---|
|
$49.5 |
|
Testing Engine
|
|---|
|
$37.5 |
|
PDF (Q&A)
|
|---|
|
$31.5 |
Paloalto Networks Free Exams |
|---|

|