You have the files shown in the following table.

You configure a retention policy as shown >n the exhibit. (Click the Exhibit lab.)
The start of the retention period is based on when items are created. The current date is January 01. 207S.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.

You have a Microsoft 365 tenant
You need to create a new sensitive into type for items that contain the following:
• An employee ID number that consists of the hire date of the employee followed by a three digit number
• The words "Employee", "ID", or "Identification" within 300 characters of the employee ID number
What should you use for the primary and secondary elements? To answer, select the appropriate options m the answer area
NOTE: Each correct selection is worth one point

You have a Microsoft 365 E5 tenant that contains a sensitivity label named label1.
You plan to enable co-authoring for encrypted files.
You need to ensure that files that have label1 applied support co-authoring.
Which two settings should you modify? To answer, select the settings in the answer area.
NOTE: Each correct selection is worth one point.

You have a Microsoft 365 ES subscription.
You have a Microsoft SharePoint Online document library that contains Microsoft Word and Excel documents. The documents contain the following types of information:
• Credit card numbers
• Physical addresses in the UK
• National hearth service numbers from the UK
• Sensitive projects that contain the following words: Project Tailspin. Project Contoso, and Project falcon
You have email messages m Microsoft Exchange Online that contain the following information types:
• Credit card numbers
• User sign-in credentials
• National health service numbers from the UK
You plan to use sensitive information types (SITs) for compliance policies.
What is the minimum number of SITs required to classify all the information types?
Your company has a Microsoft 365 tenant.
The company performs annual employee assessments. The assessment results are recorded in a document named AssessmentTemplate.docx that is created by using a Microsoft Word template. Copies of the employee assessments are sent to employees and their managers.
The assessment copies are stored in mailboxes, Microsoft SharePoint Online sites, and OneDrive folders. A copy of each assessment is also stored in a SharePoint Online folder named Assessments.
You need to create a data loss prevention (DLP) policy that prevents the employee assessments from being emailed to external users. You will use a document fingerprint to identify the assessment documents. The solution must minimize effort.
What should you include in the solution?
You have a Microsoft 365 E5 subscription. The subscription contains 500 devices that are onboarded to Microsoft Purview.
You select Activate Microsoft Purview Audit.
You need to ensure that you can track interactions between users and generative AI websites.
What should you deploy to the devices?
HOTSPOT
You have a Microsoft 365 E5 subscription that contains two Microsoft 365 groups named Group1 and Group2. Both groups use the following resources:
● A group mailbox
● Microsoft Teams channel messages
● A Microsoft SharePoint Online teams site
You create the objects shown in the following table.
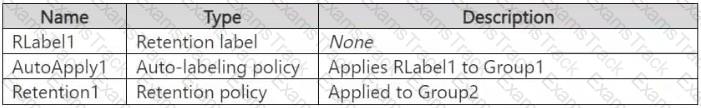
To which resources will AutoApply1 and Retention1 be applied? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
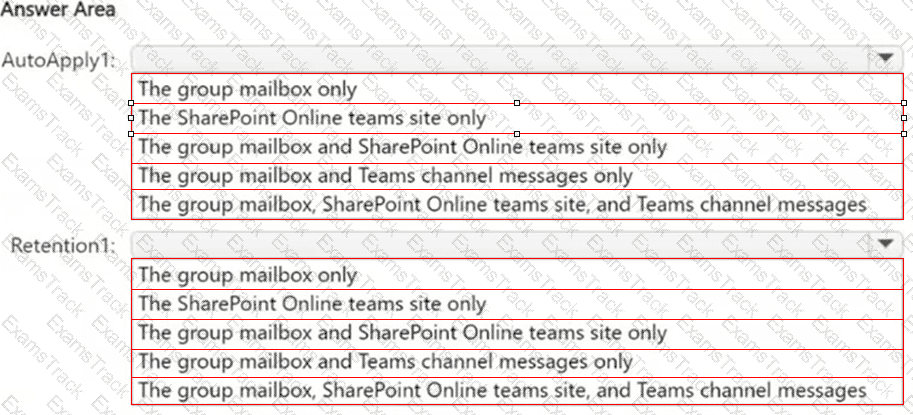
You have a Microsoft 365 subscription that contains a sensitivity label named Contoso Confidential.
You publish Contoso Confidential to all users.
Contoso Confidential is configured as shown in the Configuration exhibit. (Click the Configuration tab.)
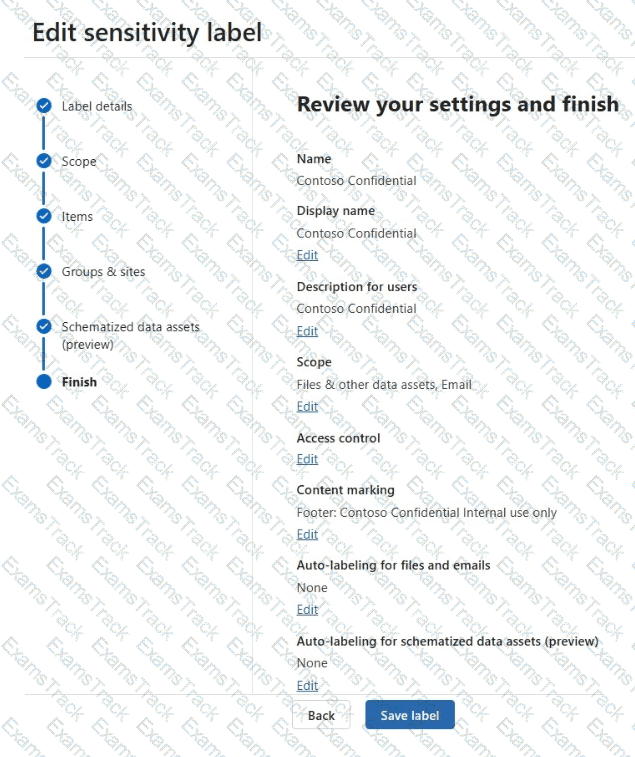
The Access control settings of Contoso Confidential are configured as shown in the Access control exhibit. (Click the Access control tab.)
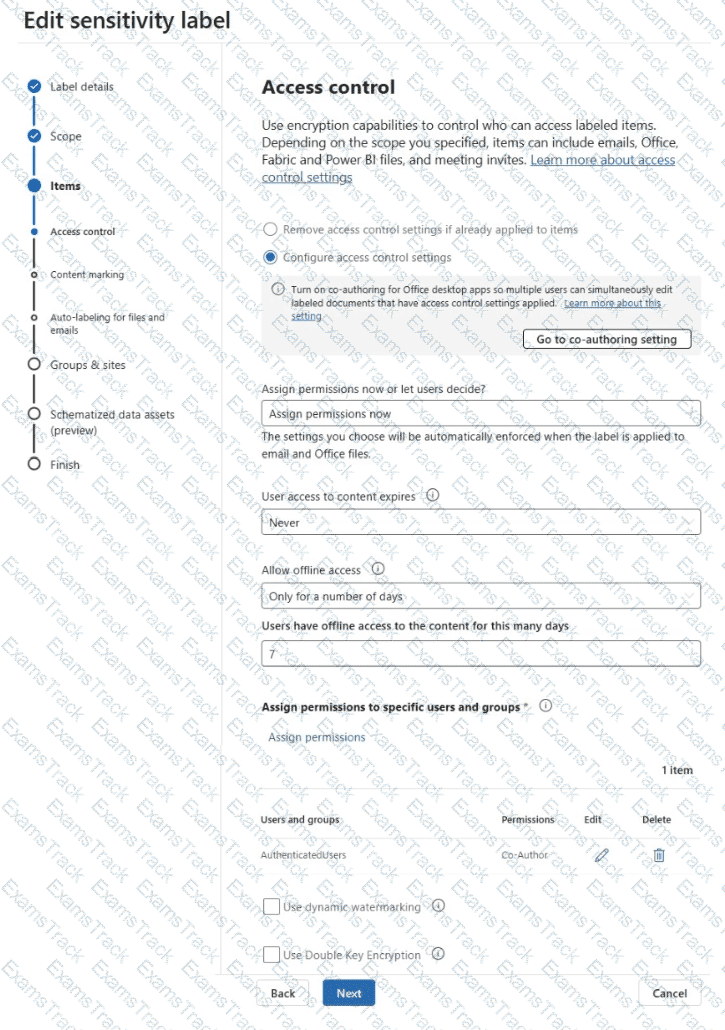
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

You have a Microsoft 365 £5 subscription.
You are implementing insider risk management.
You need to create an insider risk management notice template and format the message body of the notice template.
How should you configure the template? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription.
You need to ensure that encrypted email messages sent to an external recipient can be revoked or will expire within seven days.
What should you configure first?
|
PDF + Testing Engine
|
|---|
|
$52.5 |
|
Testing Engine
|
|---|
|
$40.5 |
|
PDF (Q&A)
|
|---|
|
$34.5 |
Microsoft Free Exams |
|---|

|