You have a Microsoft 365 E5 subscription that contains a user named User1.
You deploy Microsoft Purview insider risk management.
You need ensure that insider risk management events related to User1 are visible only to specific users.
What should you create?
You have a Microsoft 365 E5 subscription that contains three users named User1, User2, and User3 and a file named Filetdocx.
You create a sensitivity label named Label1 as shown in the following exhibit.
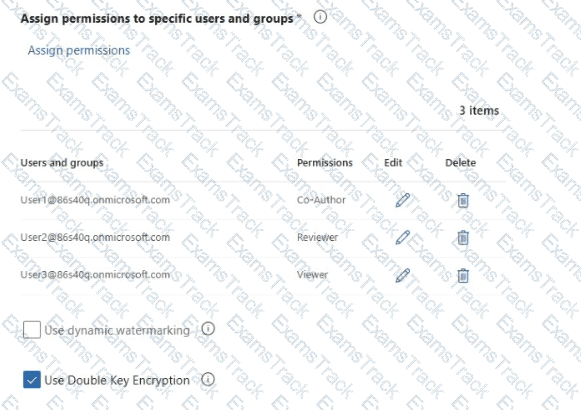
You apply Label1 to File1.
For which users can Microsoft 365 Copilot summarize File1?
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
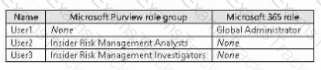
The subscription contains the groups shown in the following table.
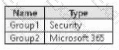
You plan to create a priority user group named Priority1.
You need to identify the following:
. Which users and groups can be added to Priority1?
. Which users can be enabled to view alerts that involve the members of Priority1?
What should you identify? To answer, select the appropriate options in the answer area.
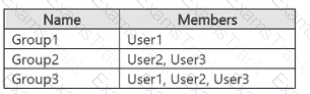

You have a Microsoft 365 IS subscription that contains the resources shown in the following table.
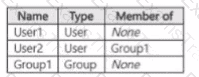
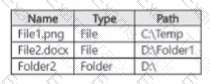
The subscription contains a Windows 11 device named Device 1 and has the Microsoft Purview Information Protection client installed. Device i contains the resources shown in the following table.
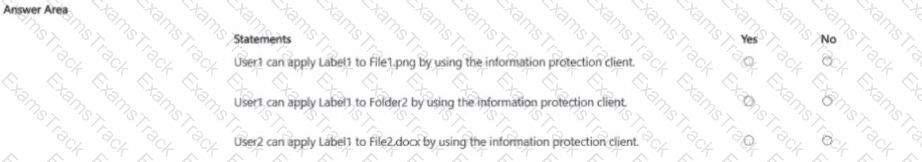
You publish a sensitivity label named Label1 to User1 and Group1.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
You have a Microsoft 365 E5 subscription that contains 500 Windows devices.
You plan to deploy Microsoft Purview Data Security Posture Management for AI (DSPM for AI).
You need to ensure that you can monitor user activities on third-party generative AI websites.
Which two prerequisites should you complete for DSPM for AI? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You have a user named User1. Several users have full access to the mailbox of User1.
Some email messages sent to User1 appear to have been read and deleted before the user viewed them.
When you search the audit log in the Microsoft Purview portal to identify who signed in to the mailbox of User1, the results are blank.
You need to ensure that you can view future sign-ins to the mailbox of User1.
Solution: You run the Set-Mailbox -Identity "User1" -AuditEnabled $true command.
Does that meet the goal?
You need to provide a user with the ability to view data loss prevention (DIP) alerts in the Microsoft Purview portal. The solution must use the principle of least privilege.
Which role should you assign to the user?
You have a Microsoft 365 E5 subscription that contains two users named User1 and User2.
On January 1, you create the sensitivity label shown in the following table.
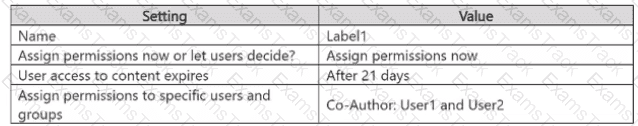
On January 2, you publish Label1 to User1.
On January 3, User1 creates a Microsoft Word document named Doc1 and applies Label! to the document. On January 4. User2 edits Doc1.
On January 15. you increase the content expiry period for Label1to 28 days. When will access to Doc1 expire for User2?
DRAG DROP
You have a Microsoft 365 subscription that contains 20 data loss prevention (DLP) policies.
You need to identify the following:
● Rules that are applied without triggering a policy alert
● The top 10 files that have matched DLP policies
● Alerts that are miscategorized
Which report should you use for each requirement? To answer, drag the appropriate reports to the correct requirements. Each report may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

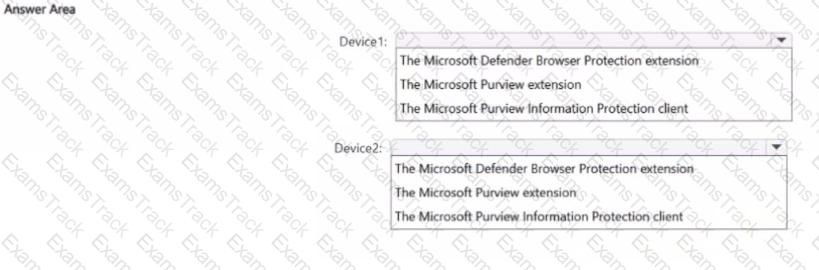
You have a Microsoft 36S ES subscription that contains two Windows devices named Devicel1and Device2 Device1 has the default browser set to Microsoft Edge. Devke2 has the default browser set to Google Chrome.
You need to ensure that Microsoft Purview insider risk management can collect signals when a user copies files to a USB device by using their default browser.
What should you deploy to each device? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
|
PDF + Testing Engine
|
|---|
|
$52.5 |
|
Testing Engine
|
|---|
|
$40.5 |
|
PDF (Q&A)
|
|---|
|
$34.5 |
Microsoft Free Exams |
|---|

|