An unusual occurrence in a system or network is best described as:
Example of a technical control:
Exhibit.
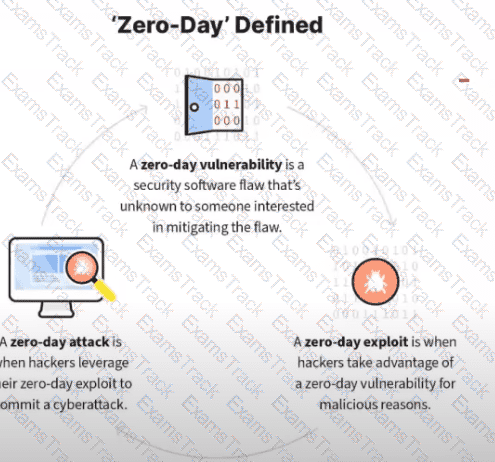
What kind of vulnerability is typically not identifiable through a standard vulnerability assessment?
An IP network protocol standardized by the IETF through RFC 792 to determine if a host is available is:
Which is NOT a component of a Business Continuity (BC) plan?
David's team recently implemented a new system that gathers information from a variety of different log sources, analyzes that information, and then triggers automated playbooks in response to security events. What term BEST describes this technology?
Which of the following is NOT one of the three main components of an SQL database?
What is meant by non-repudiation?
Which protocol would be most suitable to fulfill the secure communication requirements between clients and the server for a company deploying a new application?
|
PDF + Testing Engine
|
|---|
|
$49.5 |
|
Testing Engine
|
|---|
|
$37.5 |
|
PDF (Q&A)
|
|---|
|
$31.5 |
ISC Free Exams |
|---|

|