You work as a Network Administrator for Net Perfect Inc. The company has a Linux-based network. You have created a folder named Report. You have made David the owner of the folder. The members of a group named JAdmin can access the folder and have Read, Write, and Execute permissions. No other user can access the folder. You want to ensure that the members of the JAdmin group do not have Write permission on the folder. Also, you want other users to have Read permission on the Report folder.
Which of the following commands will you use to accomplish the task?
Which of the following choices accurately describes how PGP works when encrypting email?
An application developer would like to replace Triple DES in their software with a stronger algorithm of the same type. Which of the following should they use?
Which of the following applications would be BEST implemented with UDP instead of TCP?
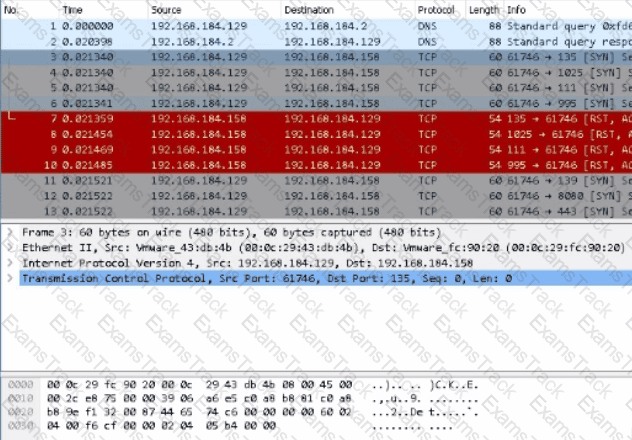
Use Wireshark to analyze Desktop;PCAP FILES/charile.pcap
What is the destination IP address in packet #3?

What is a characteristic of iOS security?
When should you create the initial database for a Linux file integrity checker?
What does an attacker need to consider when attempting an IP spoofing attack that relies on guessing Initial Sequence Numbers (ISNs)?
What is the first thing that should be done during the containment step of incident handling?
Which of the following is Azure's version of a superuser?
|
PDF + Testing Engine
|
|---|
|
$57.75 |
|
Testing Engine
|
|---|
|
$43.75 |
|
PDF (Q&A)
|
|---|
|
$36.75 |
GIAC Free Exams |
|---|

|