How is confidentiality disabled in the IPSec Encapsulated Security Payload protocol?
You work as a Network Administrator for McNeil Inc. The company has a Windows Server 2008 network environment. The network is configured as a Windows Active Directory-based single forest domain-based network. The company's management has decided to provide laptops to its sales team members. These laptops are equipped with smart card readers. The laptops will be configured as wireless network clients. You are required to accomplish the following tasks:
The wireless network communication should be secured.
The laptop users should be able to use smart cards for getting authenticated. In order to accomplish the tasks, you take the following steps:
Configure 802.1x and WEP for the wireless connections. Configure the PEAP-MS-CHAP v2 protocol for authentication. What will happen after you have taken these steps?
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. John is working as a root user on the Linux operating system. He wants to change the startup shell of Maria from bash to tcsh. Which of the following commands will John use to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following processes is known as sanitization?
What security practice is described by NIST as the application of science to the identification, collection, examination, and analysis of data while maintaining data integrity and chain of custody?
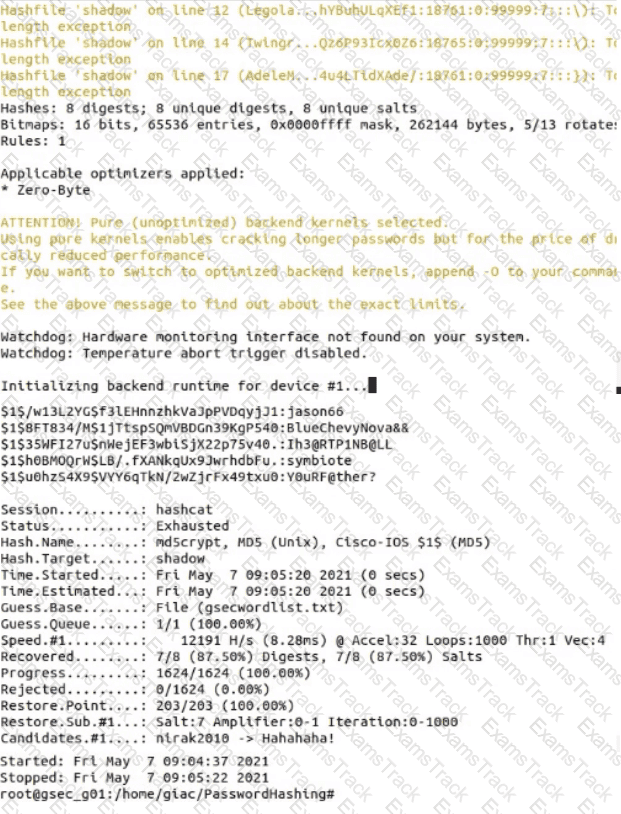
Use Hashcat to crack a local shadow file. What Is the password for the user account AGainsboro?
Hints
• The shadow file (shadow) and Hashcat wordlist (gsecwordlist.txt) are located in the directory /home /giac /PasswordHashing/
• Run Hashcat in straight mode (flag -a 0) to crack the MD5 hashes (flag -m 500) In the shadow file.
• Use the hash values from the Hashcat output file and the shadow file to match the cracked password with the user name.
• If required, a backup copy of the original files can be found in the shadowbackup directory.

Which of the following protocols work at the Session layer of the OSI model? Each correct answer represents a complete solution. Choose all that apply.
The Windows 'tracert' begins by sending what type of packet to the destination host?
Which of the following is an advantage of an Intrusion Detection System?
Which of the following are examples of Issue-Specific policies all organizations should address?
|
PDF + Testing Engine
|
|---|
|
$57.75 |
|
Testing Engine
|
|---|
|
$43.75 |
|
PDF (Q&A)
|
|---|
|
$36.75 |
GIAC Free Exams |
|---|

|