You are using a Windows-based sniffer named ASniffer to record the data traffic of a network. You have extracted the following IP Header information of a randomly chosen packet from the sniffer's log:
45 00 00 28 00 00 40 00 29 06 43 CB D2 D3 82 5A 3B 5E AA 72
Which of the following TTL decimal values and protocols are being carried by the IP Header of this packet?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He is using a tool to crack the wireless encryption keys. The description of the tool is as follows:
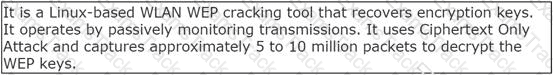
Which of the following tools is John using to crack the wireless encryption keys?
Rick works as the Network Administrator of Baby Blue Inc. He wants to upgrade the existing network to the Active Directory based Windows 2000 network.
He configures a DNS on the network. Which of the following is the primary reason that the DNS is required in an Active Directory environment?
In which of the following IDS evasion techniques does an attacker deliver data in multiple small sized packets, which makes it very difficult for an IDS to detect the attack signatures of such attacks?
Which of the following OSI layers is responsible for protocol conversion, data encryption/decryption, and data compression?
Rick works as a Computer Forensic Investigator for BlueWells Inc. He has been informed that some confidential information is being leaked out by an employee of the company. Rick suspects that someone is sending the information through email. He checks the emails sent by some employees to other networks. Rick finds out that Sam, an employee of the Sales department, is continuously sending text files that contain special symbols, graphics, and signs. Rick suspects that Sam is using the Steganography technique to send data in a disguised form. Which of the following techniques is Sam using?
Each correct answer represents a part of the solution. Choose all that apply.
An IDS is a group of processes working together in a network. These processes work on different computers and devices across the network. Which of the following processes does an IDS perform?
Each correct answer represents a complete solution. Choose all that apply.
An attacker changes the address of a sub-routine in such a manner that it begins to point to the address of the malicious code. As a result, when the function has been exited, the application can be forced to shift to the malicious code. The image given below explains this phenomenon:
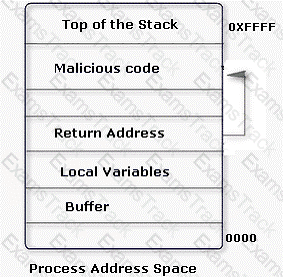
Which of the following tools can be used as a countermeasure to such an attack?
You are planning DNS configuration for your company. You decide to configure an Active Directory integrated DNS.
Which of the following are the benefits of Active Directory integrated DNS configuration?
Each correct answer represents a complete solution. Choose all that apply.
By gaining full control of router, hackers often acquire full control of the network. Which of the following methods are commonly used to attack Routers?
Each correct answer represents a complete solution. Choose all that apply.
Adam works as a professional Computer Hacking Forensic Investigator. A project has been assigned to him to investigate and examine drive image of a compromised system, which is suspected to be used in cyber crime. Adam uses Forensic Sorter to sort the contents of hard drive in different categories. Which of the following type of image formats is NOT supported by Forensic Sorter?
In a complex network, Router transfers data packets by observing some form of parameters or metrics provided in the routing table. Which of the following metrics is NOT included in the routing table?
Which of the following tools works by using standard set of MS-DOS commands and can create an MD5 hash of an entire drive, partition, or selected files?
Which of the following is a valid IP address for class B Networks?
You work as a technician for Tech Perfect Inc. You are troubleshooting an Internet name resolution issue. You ping your ISP's DNS server address and find that the server is down. You want to continuously ping the DNS address until you have stopped the command. Which of the following commands will you use?
|
PDF + Testing Engine
|
|---|
|
$57.75 |
|
Testing Engine
|
|---|
|
$43.75 |
|
PDF (Q&A)
|
|---|
|
$36.75 |
GIAC Free Exams |
|---|

|