In a /24 subnet, which of the following is a valid broadcast address?
You have been hired to design a TCP/IP-based network that will contain both Unix and Windows computers. You are planning a name resolution strategy. Which of the following services will best suit the requirements of the network?
Which of the following is the key point to consider in the recovery phase of incident handling?
Which of the following is the key point to consider in the recovery phase of incident handling?
Which Linux file lists every process that starts at boot time?
You are going to upgrade your hard disk's file system from FAT to NTFS. What are the major advantages of the NTFS file system over FAT16 and FAT32 file systems?
Each correct answer represents a complete solution. Choose all that apply.
You are examining a packet capture session in Wire shark and see the packet shown in the accompanying image. Based on what you see, what is the appropriate protection against this type of attempted attack?
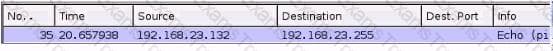
You work as a Linux technician for Tech Perfect Inc. You have lost the password of the root. You want to provide a new password. Which of the following steps will you take to accomplish the task?
Which of the following statements about the authentication concept of information security management is true?
When a packet leaving the network undergoes Network Address Translation (NAT), which of the following is changed?
Which logging capability is provided natively by syslog?
|
PDF + Testing Engine
|
|---|
|
$57.75 |
|
Testing Engine
|
|---|
|
$43.75 |
|
PDF (Q&A)
|
|---|
|
$36.75 |
GIAC Free Exams |
|---|

|