Which of the following defines the communication link between a Web server and Web applications?
Which of the following attacks can be mitigated by avoiding making system calls from within a web application?
The Linux command to make the /etc/shadow file, already owned by root, readable only by root is which of the following?
Which of the following terms refers to the process in which headers and trailers are added around user data?
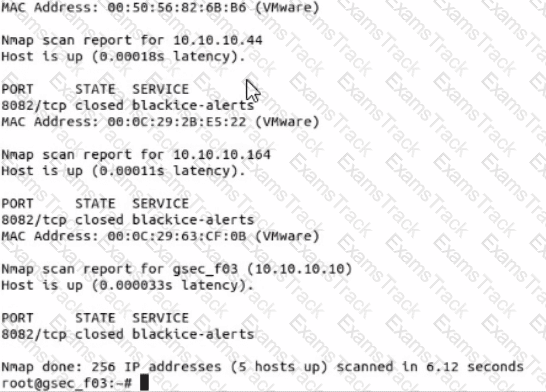
Use nmap to discover a host on the 10.10.10.0/24 network, scanning only port 8082 and using the SYN or Stealth scan approach. Which host has a service called -blackice-alerts"?

When considering ingress filtering, why should all inbound packets be dropped if they contain a source address from within the protected network address space?
Where are user accounts and passwords stored in a decentralized privilege management environment?
A Host-based Intrusion Prevention System (HIPS) software vendor records how the Firefox Web browser interacts with the operating system and other applications, and identifies all areas of Firefox functionality. After collecting all the data about how Firefox should work, a database is created with this information, and it is fed into the HIPS software. The HIPS then monitors Firefox whenever it's in use. What feature of HIPS is being described in this scenario?
What is needed for any of the four options for Azure AD multi-factor user authentication?
Which of the following is generally practiced by the police or any other recognized governmental authority?
|
PDF + Testing Engine
|
|---|
|
$57.75 |
|
Testing Engine
|
|---|
|
$43.75 |
|
PDF (Q&A)
|
|---|
|
$36.75 |
GIAC Free Exams |
|---|

|