The OT network analyst run different level of reports to quickly explore failures that could put the network at risk. Such reports can be about device performance. Which FortiSIEM reporting method helps to identify device failures?
Refer to the exhibit
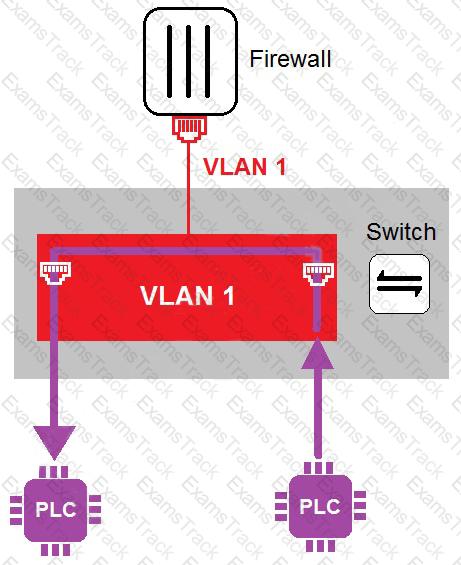
In the topology shown in the exhibit, both PLCs can communicate directly with each other, without going through the firewall.
Which statement about the topology is true?
Refer to the exhibits.
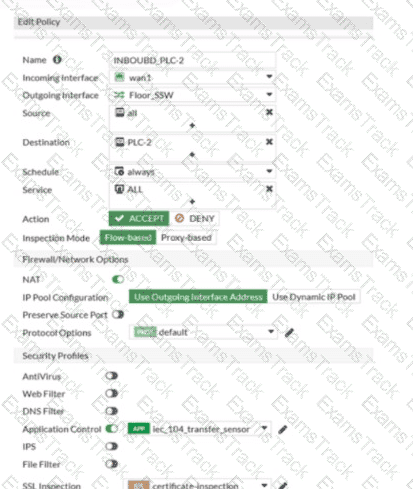
Which statement is true about the traffic passing through to PLC-2?
As an OT network administrator, you are managing three FortiGate devices that each protect different levels on the Purdue model. To increase traffic visibility, you are required to implement additional security measures to detect exploits that affect PLCs.
Which security sensor must implement to detect these types of industrial exploits?
Refer to the exhibit.
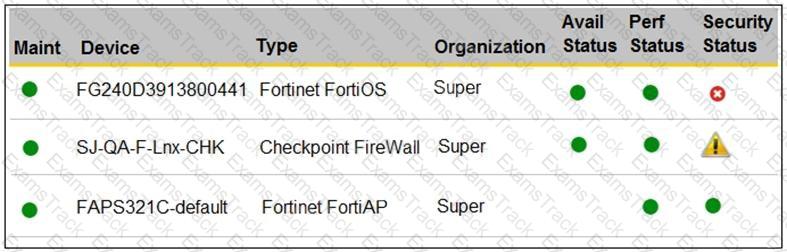
You are navigating through FortiSIEM in an OT network.
How do you view information presented in the exhibit and what does the FortiGate device security status tell you?
As an OT network administrator you are required to generate reports that primarily use the same type of data sent to FortiSlEM These reports are based on the preloaded analytic searches
Which two actions can you take on FortiSlEM to enhance running reports for future use? (Choose two.)
To increase security protection in an OT network, how does application control on ForliGate detect industrial traffic?
How can you achieve remote access and internet availability in an OT network?
Which statement about the IEC 104 protocol is true?
A FortiGate device is newly deployed as the edge gateway of an OT network security fabric. The downstream FortiGate devices are also newly deployed as Security Fabric leafs to protect the control area zone.
With no additional essential networking devices, and to implement micro-segmentation on this OT network, what configuration must the OT network architect apply to control intra-VLAN traffic?
|
PDF + Testing Engine
|
|---|
|
$49.5 |
|
Testing Engine
|
|---|
|
$37.5 |
|
PDF (Q&A)
|
|---|
|
$31.5 |
Fortinet Free Exams |
|---|

|