Following the setting of an organization’s risk appetite by senior management, a risk manager needs to prioritize all identified risks for treatment. Each risk has been scored based on its Annualized Loss Expectancy (ALE). Management has asked for an immediate risk mitigation plan focusing on top risks. Which is the MOST effective approach for the risk manager to quickly present a proposal to management?
Which of the following presents the GREATEST benefit to an organization's security posture when a change management process is implemented?
Which of the following statements is an advantage of a fourth-party logistics (4PL) provider?
An organization is considering options to outsource their Information Technology (IT) operations. Although they do not sell anything on the Internet, they have a strong requirement in uptime of their application. After the offerings received by the Cloud Service Provider (CSP), the IT manager decided it was mandatory to develop processes to continue operations without access to community or public cloud-based applications. Which of the following arguments MOST likely led the IT manager to make this decision?
A security practitioner has been asked to investigate the presence of customer Personally Identifiable Information (PII) on a social media website. Where does the practitioner begin?
In the sales and operations planning (S&OP) process, the demand management function provides:
Which of the following is the BEST activity to mitigate risk from ransomware on mobile devices and removable media in a corporate environment?
The question below is based on the following standard and actual data of a production order
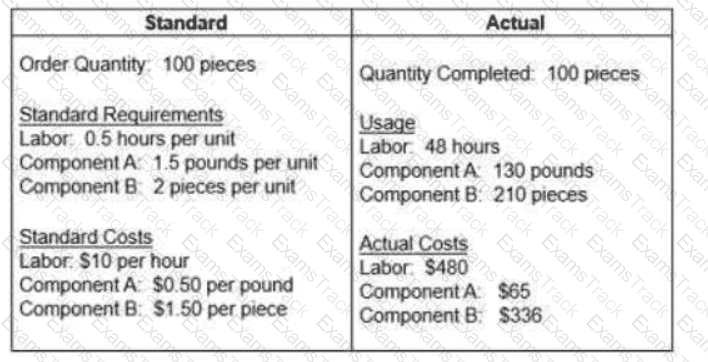
Which of the following statements about variances is true?
The question below is based on the following information:
Beginning inventory = 43Week 1Week 2Week 3
Forecast202020
Customer orders221710
Projected on-hand
Master production schedule (MPS)80
Available-to-promise (ATP)
What is the largest customer order that could be accepted for delivery at the end of week 3 without making changes to the master production schedule (MPS)?
Management should support investments in new process technologies that:
Which of the following BEST represents a security benefit of Software-Defined Networking (SDN)?
As the organization requires user friendly access to a new web-based application, a software developer decides to implement Single Sign-On (SSO). The developer uses the de-facto standard for web-based applications and the implementation includes the use of a JavaScript Object Notation (JSON) web token. With this information, which is the BEST way for the software developer to establish SSO capability?
An organization is designing a new Disaster Recovery (DR) site. What is the BEST option to harden security of the site?
Which of the following roles is the BEST choice for classifying sensitive data?
Business management should be engaged in the creation of Business Continuity (BC) and Disaster Recovery plans (DRP) because they need to
|
PDF + Testing Engine
|
|---|
|
$49.5 |
|
Testing Engine
|
|---|
|
$37.5 |
|
PDF (Q&A)
|
|---|
|
$31.5 |
APICS Free Exams |
|---|

|