Which approach will BEST mitigate risks associated with root user access while maintaining system functionality?
Forecast error typically triggers forecast revision when it is:
An information security professional is considering what type of classification label to place on an organization’s software code in order to implement proper access controls. The code is considered intellectual property data and would have a catastrophic impact to the organization if compromised or destroyed. Which of the following would be the MOST appropriate classification label to apply?
At which Open Systems Interconnection (OSI) layer does User Datagram Protocol (UDP) function?
Which of the following tools shows process changes and random variation over time?
A consultant has been engaged to support the team in analyzing why the development of a new software product has slipped schedule by a year. The consultant discovered an increase of the functionality requirements due to the failure of the asset tracking program. Which of the following BEST describes which system lifecycle element is impacted?
A Software As A Service (SaaS) solution was compromised due to multiple missing security controls. The SaaS deployment was rushed and the Software Development Life Cycle (SDLC) was not followed. Which SDLC phase would have been MOST effective in preventing this failure?
Which of the following MUST be in place for security to be effective in an organization?
A security team member is assessing an organization’s backup strategy that follows the 3-2-1 rule. How many different types of media should they inspect to validate?
Access Control Lists (ACL), protection bits, and file passwords are typical examples of which of the following access control methods?
Which security concept applies if an architecture diagram illustrates a particular user/role combination with access to an asset or applicaton?
An organization is implementing Zero Trust Network Access (ZTNA) and needs a strategy to measure device trust for employee laptops. Which measurement strategy is BEST suited and why?
Which of the following techniques would a group use to prioritize problems?
Which of the following items does the master scheduler have the authority to change in the master scheduling process?
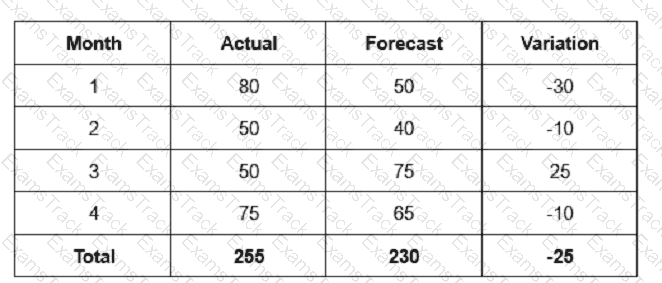
Based on the above table, calculate the mean absolute deviation (MAD).
|
PDF + Testing Engine
|
|---|
|
$49.5 |
|
Testing Engine
|
|---|
|
$37.5 |
|
PDF (Q&A)
|
|---|
|
$31.5 |
APICS Free Exams |
|---|

|