Which of the following actions best supports a company's strategic focus on delivery speed to improve competitive advantage?
In order to meet retention requirements, it may be necessary to migrate digital records to different media because of which of the following issues?
An example of a cradle-to-cradle sustainability model would be:
Which of the following represents the BEST metric when measuring the effectiveness of a security awareness program?
An organization discovered that malicious software was installed on an employee’s work laptop and allowed a competing vendor to access confidential files. The employee was fully aware of the policy not to install unauthorized software on the organization laptop. What is the BEST automated security practice for an organization to implement to avoid this situation?
The primary purpose for engaging in cycle count activities is to:
In the context of mobile device security, which of the following BEST describes why a walled garden should be implemented?
Which of the following provides for continuous improvement of the change control process?
Which of the following is the fundamental difference between finite loading and other capacity planning approaches?
In conducting a new corporate payroll system security review, which of the following individuals should answer questions regarding the data classification?
An OpenID Connect (OIDC) authorization server received two requests from a client. The server identifies the request as replay attack and rejects the request. Which of the following BEST describes these requests?
Exhibit:
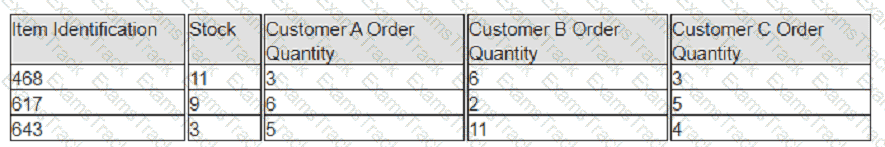
A company has prioritized customers A, B, and C, filling orders in that sequence. What are the impacts to customer service levels for customers B and C?
A company is having trouble with raw material deliveries and has decided to develop a supplier certification program. The certification process most appropriately would start with which of the following suppliers?
An agency has the requirement to establish a direct data connection with another organization for the purpose of exchanging data between the agency and organization systems. There is a requirement for a formal agreement between the agency and organization. Which source of standards can the system owners use to define the roles and responsibilities along with details for the technical and security requirements?
Which of the following mechanisms are PRIMARILY designed to thwart side channel attacks?
|
PDF + Testing Engine
|
|---|
|
$49.5 |
|
Testing Engine
|
|---|
|
$37.5 |
|
PDF (Q&A)
|
|---|
|
$31.5 |
APICS Free Exams |
|---|

|