Which statement is true regarding CloudFormation templates?
The security team wants to target a CNAF policy for specific running Containers. How should the administrator scope the policy to target the Containers?
Which three OWASP protections are part of Prisma Cloud Web-Application and API Security (WAAS) rule? (Choose three.)
If you are required to run in an air-gapped environment, which product should you install?
Given the following RQL:
Which audit event snippet is identified by the RQL?
A)
B)
C)
D)
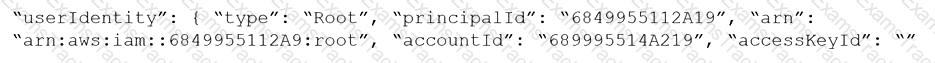
Which serverless cloud provider is covered by the "overly permissive service access" compliance check?
Which set of steps is the correct process for obtaining Console images for Prisma Cloud Compute Edition?
You have onboarded a public cloud account into Prisma Cloud Enterprise. Configuration Resource ingestion is visible in the Asset Inventory for the onboarded account, but no alerts are being generated for the configuration assets in the account.
Config policies are enabled in the Prisma Cloud Enterprise tenant, with those policies associated to existing alert rules. ROL statements on the investigate matching those policies return config resource results successfully.
Why are no alerts being generated?
An administrator sees that a runtime audit has been generated for a Container. The audit message is “DNS resolution of suspicious name wikipedia.com. type A”.
Why would this message appear as an audit?
A Prisma Cloud Administrator needs to enable a Registry Scanning for a registry that stores Windows images. Which of the following statement is correct regarding this process?
|
PDF + Testing Engine
|
|---|
|
$49.5 |
|
Testing Engine
|
|---|
|
$37.5 |
|
PDF (Q&A)
|
|---|
|
$31.5 |
Paloalto Networks Free Exams |
|---|

|