The Prisma Cloud administrator has configured a new policy.
Which steps should be used to assign this policy to a compliance standard?
Which command should be used in the Prisma Cloud twistcli tool to scan the nginx:latest image for vulnerabilities and compliance issues?
A)
B)

C)
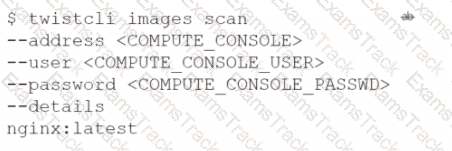
D)
Which two filters are available in the SecOps dashboard? (Choose two.)
Which RQL will trigger the following audit event activity?
Under which tactic is “Exploit Public-Facing Application” categorized in the ATT&CK framework?
An administrator sees that a runtime audit has been generated for a container.
The audit message is:
“/bin/ls launched and is explicitly blocked in the runtime rule. Full command: ls -latr”
Which protection in the runtime rule would cause this audit?
Which ban for DoS protection will enforce a rate limit for users who are unable to post five (5) “. tar.gz" files within five (5) seconds?
Which type of RQL query should be run to determine if AWS Elastic Compute Cloud (EC2) instances without encryption was enabled?
A customer has serverless functions that are deployed in multiple clouds.
Which serverless cloud provider is covered be “overly permissive service access” compliance check?
Which statement about build and run policies is true?
|
PDF + Testing Engine
|
|---|
|
$49.5 |
|
Testing Engine
|
|---|
|
$37.5 |
|
PDF (Q&A)
|
|---|
|
$31.5 |
Paloalto Networks Free Exams |
|---|

|