Which three types of classifications are available in the Data Security module? (Choose three.)
Which resources can be added in scope while creating a vulnerability policy for continuous integration?
Given an existing ECS Cluster, which option shows the steps required to install the Console in Amazon ECS?
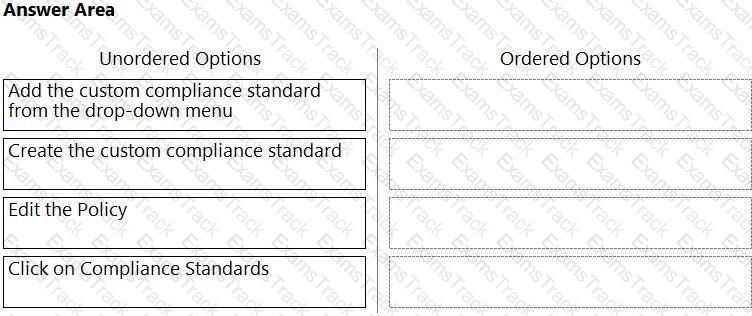
Which order of steps map a policy to a custom compliance standard?
(Drag the steps into the correct order of occurrence, from the first step to the last.)
Which component(s), if any, will Palo Alto Networks host and run when a customer purchases Prisma Cloud Enterprise Edition?
In which Console menu would an administrator verify whether a custom compliance check is failing or passing?
What is the frequency to create a compliance report? (Choose two.)
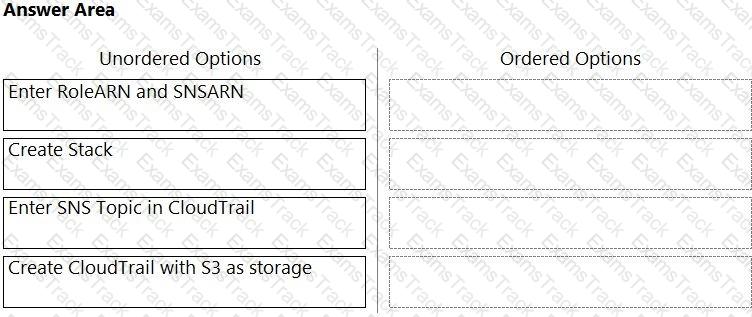
Order the steps involved in onboarding an AWS Account for use with Data Security feature.
Which type of compliance check is available for rules under Defend > Compliance > Containers and Images > CI?
Which three actions are required in order to use the automated method within Azure Cloud to streamline the process of using remediation in the identity and access management (IAM) module? (Choose three.)
|
PDF + Testing Engine
|
|---|
|
$49.5 |
|
Testing Engine
|
|---|
|
$37.5 |
|
PDF (Q&A)
|
|---|
|
$31.5 |
Paloalto Networks Free Exams |
|---|

|