Which of following best demonstrates the application of the cost principle?
Which of the following job design techniques would most likely be used to increase employee motivation through job responsibility and recognition?
A new manager received computations of the internal rate of return regarding his project proposal. What should the manager compare the computation results to in order to determine whether the project is potentially acceptable?
Which of the following is a characteristic of big data?
A chief audit executive (CAE) joined an organization in the middle of the financial year. A risk-based annual audit plan has been approved by the board and is already underway. However, after discussions with key stakeholders, the CAE realizes that some significant key risk areas have not been covered in the original audit plan. How should the CAE respond?
Which of the following best describes a detective control designed to protect an organization from cyberthreats and attacks?
Which of the following items represents a limitation with an impact the chief audit executive should report to the board?
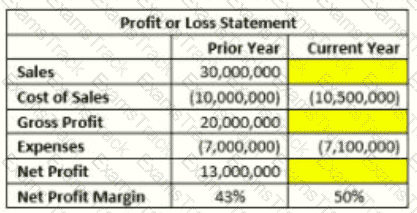
The manager of the sales department wants to Increase the organization's net profit margin by 7% (from 43% in the prior year to 50% in the current year). Given the information provided in the table below, what would be the targeted sales amount for the current year?
Which of the following describes a third-party network that connects an organization specifically with its trading partners?
The budgeted cost of work performed is a metric best used to measure which project management activity?
Which of the following should software auditors do when reporting internal audit findings related to enterprisewide resource planning?
When management uses the absorption costing approach, fixed manufacturing overhead costs are classified as which of the following types of costs?
At an organization that uses a periodic inventory system, the accountant accidentally understated the organization s beginning inventory. How would the accountant's accident impact the income statement?
According to UA guidance on IT, at which of the following stages of the project life cycle would the project manager most likely address the need to coordinate project resources?
Which of the following purchasing scenarios would gain the greatest benefit from implementing electronic data interchange (EDI)?
|
PDF + Testing Engine
|
|---|
|
$49.5 |
|
Testing Engine
|
|---|
|
$37.5 |
|
PDF (Q&A)
|
|---|
|
$31.5 |
IIA Free Exams |
|---|

|