A company has AOS-CX switches and HPE Aruba Networking ClearPass Policy Manager (CPPM). The company wants switches to implement 802.1X
authentication to CPPM and download user roles.
What is one task that you must complete on the switches to support this use case?
You have installed an HPE Aruba Networking Network Analytic Engine (NAE) script on an AOS-CX switch to monitor a particular function.
Which additional step must you complete to start the monitoring?
You need to create a rule in an HPE Aruba Networking ClearPass Policy Manager (CPPM) role mapping policy that references a ClearPass Device Insight Tag. Which Type (namespace) should you specify for the rule?
Refer to the exhibit.
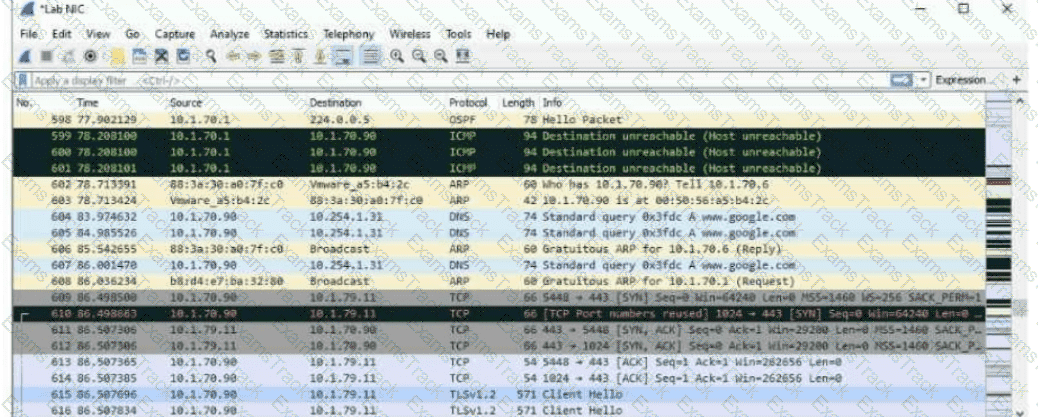
The exhibit shows a saved packet capture, which you have opened in Wireshark. You want to focus on the complete conversation between 10.1.70.90 and 10.1.79.11 that uses source port 5448.
What is a simple way to do this in Wireshark?
You are using Wireshark to view packets captured from HPE Aruba Networking infrastructure, but you’re not sure that the packets are displaying correctly. In which circumstance does it make sense to configure Wireshark to ignore protection bits with the IV for the 802.11 protocol?
A company wants HPE Aruba Networking ClearPass Policy Manager (CPPM) to respond to Syslog messages from its Check Point firewall. You have added the
firewall as an event source and set up an event service. However, test Syslog messages are not triggering the expected actions.
What is one CPPM setting that you should check?
A company has AOS-CX switches. The company wants to make it simpler and faster for admins to detect denial of service (DoS) attacks, such as ping or ARP floods, launched against the switches.
What can you do to support this use case?
A company uses both HPE Aruba Networking ClearPass Policy Manager (CPPM) and HPE Aruba Networking ClearPass Device Insight (CPDI). What is one way integrating the two solutions can help the company implement Zero Trust Security?
A company is using HPE Aruba Networking Central SD-WAN Orchestrator to establish a hub-spoke VPN between branch gateways (BGWs) at 1164 site and VPNCs at multiple data centers. What is part of the configuration that admins need to complete?
You are setting up an HPE Aruba Networking VIA solution for a company. You need to configure access control policies for applications and resources that remote
clients can access when connected to the VPN.
Where on the VPNC should you configure these policies?
|
PDF + Testing Engine
|
|---|
|
$49.5 |
|
Testing Engine
|
|---|
|
$37.5 |
|
PDF (Q&A)
|
|---|
|
$31.5 |
HP Free Exams |
|---|

|