Which of the following statements about Secure Sockets Layer (SSL) are true? (Choose two)
You work as an Exchange Administrator for XYZ CORP. The network design of the company is given below:
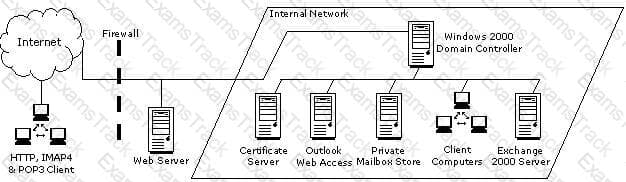
Employees are required to use Microsoft Outlook Web Access to access their emails remotely. You are required to accomplish the following goals: Ensure fault tolerance amongst the servers. Ensure the highest level of security and encryption for the Outlook Web Access clients. What will you do to accomplish these goals?
You work as a Network Administrator for ABC Inc. The company needs a secured wireless network. To provide network security to the company, you are required to configure a device that provides the best network perimeter security. Which of the following devices would you use to accomplish the task?
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. John is working as a root user on the Linux operating system. He wants to break a dat a.txt file, 200MB in size, into two files in which the size of the first file named data.txt.aa should be 150MB and that of the second file named data.txt.ab should be 50MB. To accomplish his task and to further delete the data.txt file, he enters the following command: split --verbose -b 150m data.txt data.txt. ; rm -vf data.txt Which of the following commands can John use to join the splitted files into a new data.txt file?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He begins to perform a pre-attack test before conducting an attack on the We-are-secure server. Which of the following will John perform in the pre-attack phase?
Mark works as a Database Administrator for MarLinc Inc. How will he execute a SQL command from the SQL buffer?
Which of the following types of authentication tokens forms a logical connection to the client computer but does not require a physical connection?
Which of the following is an Internet mapping technique that relies on various BGP collectors that collect information such as routing updates and tables and provide this information publicly?
You work as a Network Administrator for Infosec Inc. Nowadays, you are facing an unauthorized access in your Wi-Fi network. Therefore, you analyze a log that has been recorded by your favorite sniffer, Ethereal. You are able to discover the cause of the unauthorized access after noticing the following string in the log file: (Wlan.fc.type_subtype eq 32 and llc.oui eq 0x00601d and llc.pid eq 0x0001) When you find All your 802.11b are belong to us as the payload string, you are convinced about which tool is being used for the unauthorized access. Which of the following tools have you ascertained?
In which of the following attacking methods does an attacker distribute incorrect IP address?
|
PDF + Testing Engine
|
|---|
|
$57.75 |
|
Testing Engine
|
|---|
|
$43.75 |
|
PDF (Q&A)
|
|---|
|
$36.75 |
GIAC Free Exams |
|---|

|