Which of the following tools hides information about IIS Webservers so that they can be prevented from various attacks performed by an attacker?
Which of the following statements are true about a hot site?
You work as a Network Administrator for Techpearl Inc. You are configuring the rules for the firewall of the company. You need to allow internal users to access secure external websites. Which of the following firewall rules will you use to accomplish the task?
Sarah works as a Web Developer for XYZ CORP. She develops a Web site for the company. She uses tables in the Web site. Sarah embeds three tables within a table. What is the technique of embedding tables within a table known as?
You work as a Database Administrator for BigApple Inc. The Company uses Oracle as its database. You enabled standard database auditing. Later, you noticed that it has a huge impact on performance of the database by generating a large amount of audit data. How will you keep control on this audit data?
Brutus is a password cracking tool that can be used to crack the following authentications: HTTP (Basic Authentication) HTTP (HTML Form/CGI) POP3 (Post Office Protocol v3) FTP (File Transfer Protocol) SMB (Server Message Block) Telnet Which of the following attacks can be performed by Brutus for password cracking?
In a network, a data packet is received by a router for transmitting it to another network. For forwarding the packet to the other available networks, the router is configured with a static or a dynamic route. What are the benefits of using a static route?
In an IT organization, some specific tasks require additional detailed controls to ensure that the workers perform their job correctly. What do these detailed controls specify? (Choose three)
You work as the Network Administrator for XYZ CORP. The company has a Linux-based network. You are a root user on the Red Hat operating system. You want to see first five lines of the file /etc/passwd. Which of the following commands should you use to accomplish the task?
You have purchased a laptop that runs Windows Vista Home Premium. You want to protect your computer from malicious applications, such as spyware, while connecting to the Internet. You configure Windows Defender on your laptop to schedule scan daily at 2 AM as shown in the image below:
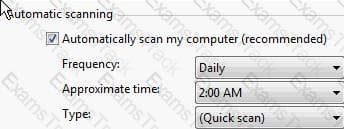
You want Windows Defender to scan the laptop for all the known spyware and other potentially unwanted software, including the latest one. You do not want to manually perform this task. Which of the following actions will you perform to accomplish the task?
|
PDF + Testing Engine
|
|---|
|
$57.75 |
|
Testing Engine
|
|---|
|
$43.75 |
|
PDF (Q&A)
|
|---|
|
$36.75 |
GIAC Free Exams |
|---|

|