Why is it important to have a cheat sheet reference of database system tables when performing SQL Injection?
Approximately how many packets are usually required to conduct a successful FMS attack onWEP?
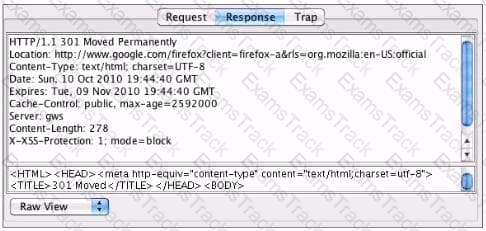
You've been asked to test a non-transparent proxy lo make sure it is working. After confirming the browser is correctly pointed at the proxy, you try to browse a web site. The browser indicates it is "loading" but never displays any part the page. Checking the proxy, you see a valid request in the proxy from your browser. Checking the response to the proxy, you see the results displayed in the accompanying screenshot. Which of the following answers is the most likely reason the browser hasn't displayed the page yet?
Which Metasploit payload includes simple upload and download functionality for moving files to and from compromised systems?
What is the purpose of the following command?
C:\>wmic /node:[target IP] /user:[admin-user]
/password:[password] process call create [command]
Which of the following modes describes a wireless interface that is configured to passively grab wireless frames from one wireless channel and pass them to the operating system?
When a DNS server transfers its zone file to a remote system, what port does it typically use?
Which of the following TCP packet sequences are common during a SYN (or half-open) scan?
A tester has been contracted to perform a penetration test for a corporate client. The scope of the test is limited to end-user workstations and client programs only. Which of die following actions is allowed in this test?
A customer has asked for a scan or vulnerable SSH servers. What is the penetration tester attempting to accomplish using the following Nmap command?
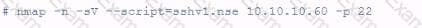
|
PDF + Testing Engine
|
|---|
|
$57.75 |
|
Testing Engine
|
|---|
|
$43.75 |
|
PDF (Q&A)
|
|---|
|
$36.75 |
GIAC Free Exams |
|---|

|