Which of the following attacks allows an attacker to sniff data frames on a local area network (LAN) or stop the traffic altogether?
In which of the following attacks does an attacker use packet sniffing to read network traffic between two parties to steal the session cookie?
Analyze the screenshot below, which of the following sets of results will be retrieved using this search?
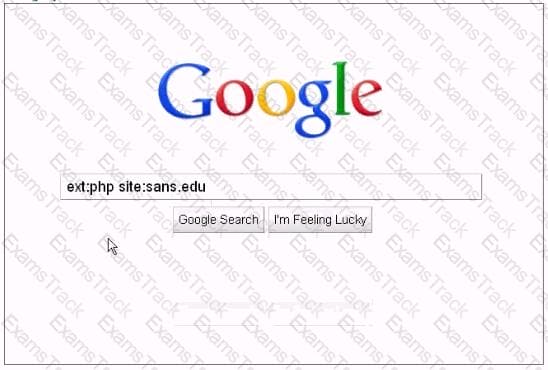
Which of the following penetration testing phases involves gathering data from whois, DNS, and network scanning, which helps in mapping a target network and provides valuable information regarding the operating system and applications running on the systems?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He is using a tool to crack the wireless encryption keys. The description of the tool is as follows:

Which of the following tools is John using to crack the wireless encryption keys?
Which of the following security policies will you implement to keep safe your data when you connect your Laptop to the office network over IEEE 802.11 WLANs?
Each correct answer represents a complete solution. Choose two.
Which of the following statements are true about NTLMv1?
Each correct answer represents a complete solution. Choose all that apply.
What happens when you scan a broadcast IP address of a network?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following tools allow you to perform HTTP tunneling?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following Web authentication techniques uses a single sign-on scheme?
|
PDF + Testing Engine
|
|---|
|
$57.75 |
|
Testing Engine
|
|---|
|
$43.75 |
|
PDF (Q&A)
|
|---|
|
$36.75 |
GIAC Free Exams |
|---|

|