Refer to the exhibits.
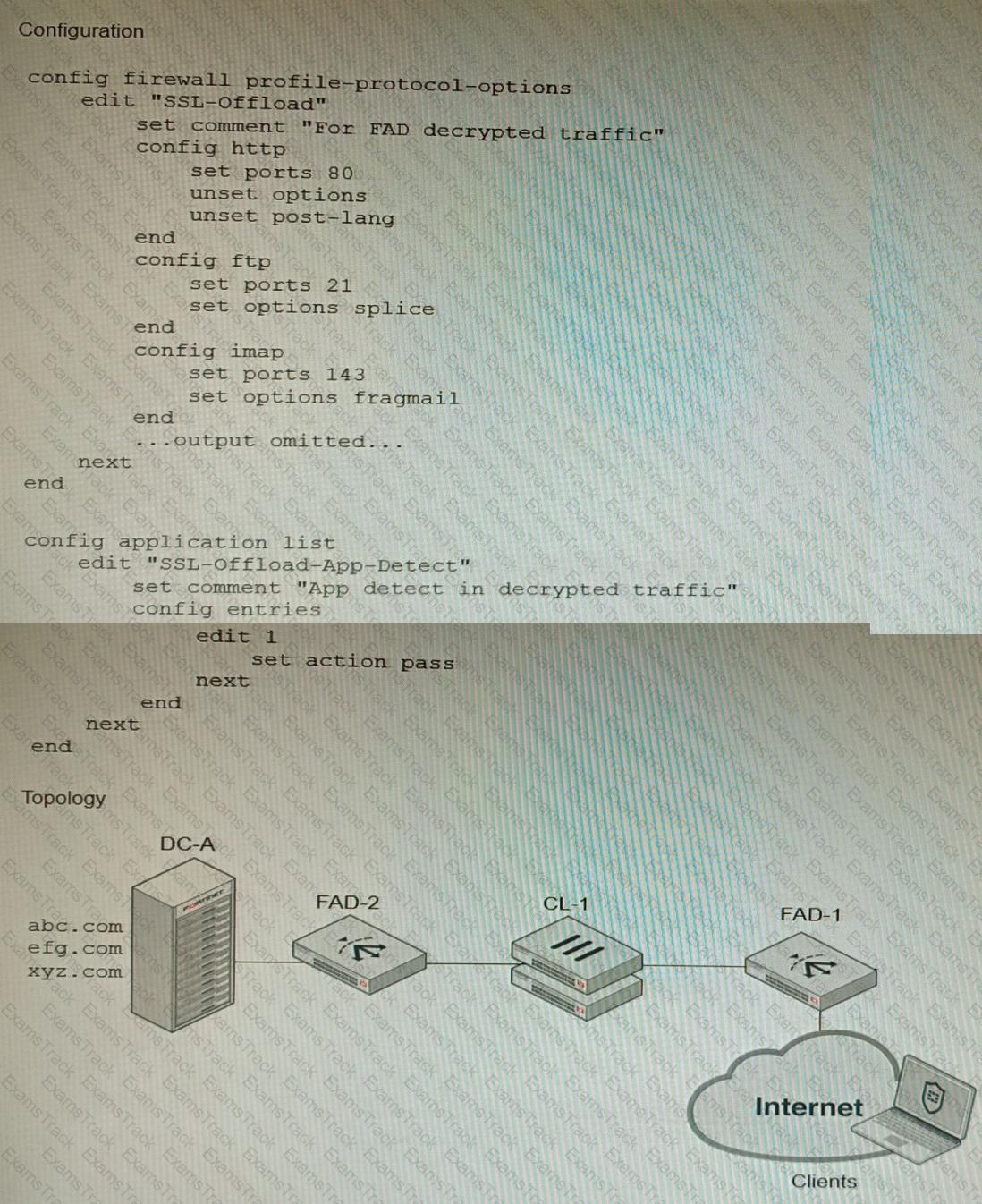
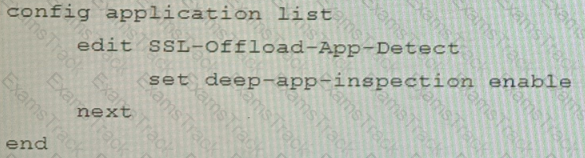
A FortiGate cluster (CL-1) protects a data center hosting multiple web applications. A pair of FortiADC devices are already configured for SSL decryption (FAD-1), and re-encryption (FAD-2). CL-1 must accept unencrypted traffic from FAD-1, perform application detection on the plain-text traffic, and forward the inspected traffic to FAD-2.
The SSL-Offload-App-Detect application list and SSL-Offload protocol options profile are applied to the firewall policy handling the web application traffic on CL-1.
Given this scenario, which two configuration tasks must the administrator perform on CL-1? (Choose two.)
A)
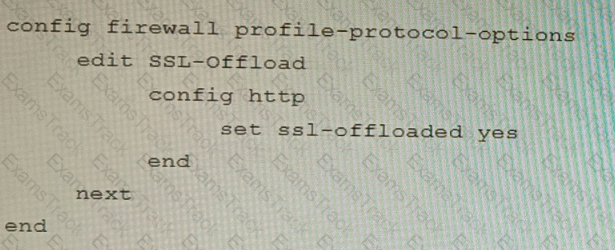
B)
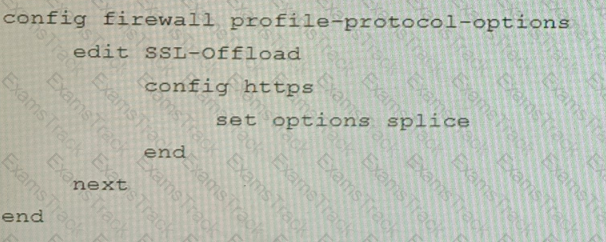
C)
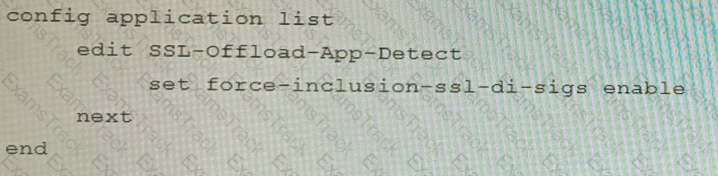
D)
Refer to the exhibit.
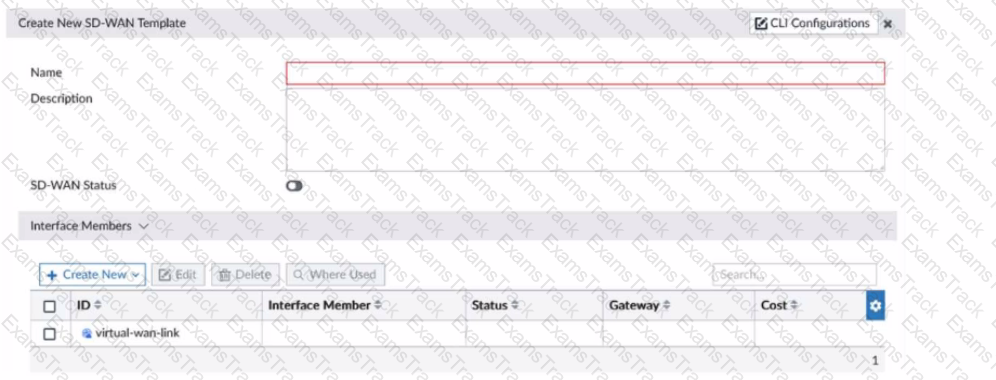
You need to create a base SD-WAN configuration that includes SD-WAN rules and Performance SLAs for spoke sites with various connectivity types. It needs to be done in a way that can be easily applied to new sites with a minimum amount of change. How should you create the SD-WAN zones?
Refer to the exhibit, which shows a VPN topology.

The device IP 10.1.100.40 downloads a file from the FTP server IP 192.168.4.50
Referring to the exhibit, what will be the traffic flow behavior if ADVPN is configured in this environment?
Refer to the exhibits.
Exhibit A

Exhibit B

Exhibit C

A customer is trying to set up a VPN with a FortiGate, but they do not have a backup of the configuration. Output during a troubleshooting session is shown in the exhibits A and B and a baseline VPN configuration is shown in Exhibit C Referring to the exhibits, which configuration will restore VPN connectivity?
A)

B)

C)

D)

Refer to the exhibit.
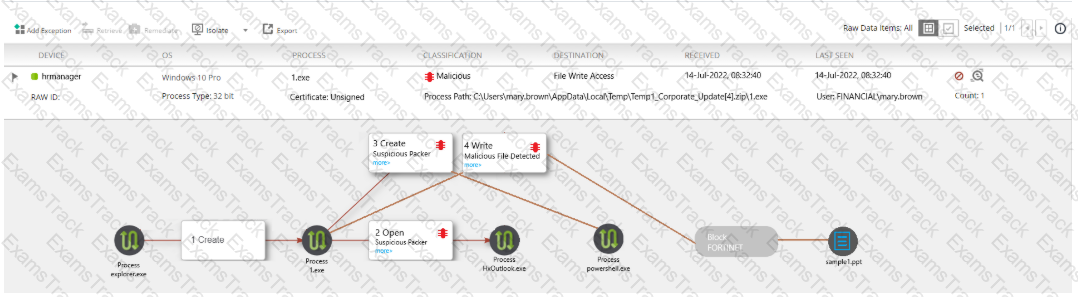
The exhibit shows the forensics analysis of an event detected by the FortiEDR core
In this scenario, which statement is correct regarding the threat?
A customer is operating a FortiWeb cluster in a high volume active-active HA group consisting of eight FortiWeb appliances. One of the secondary members is handling traffic for one specific VIP.
What will happen with the traffic if that secondary FortiWeb appliance fails?
Refer to the exhibit, which shows a Branch1 configuration and routing table.
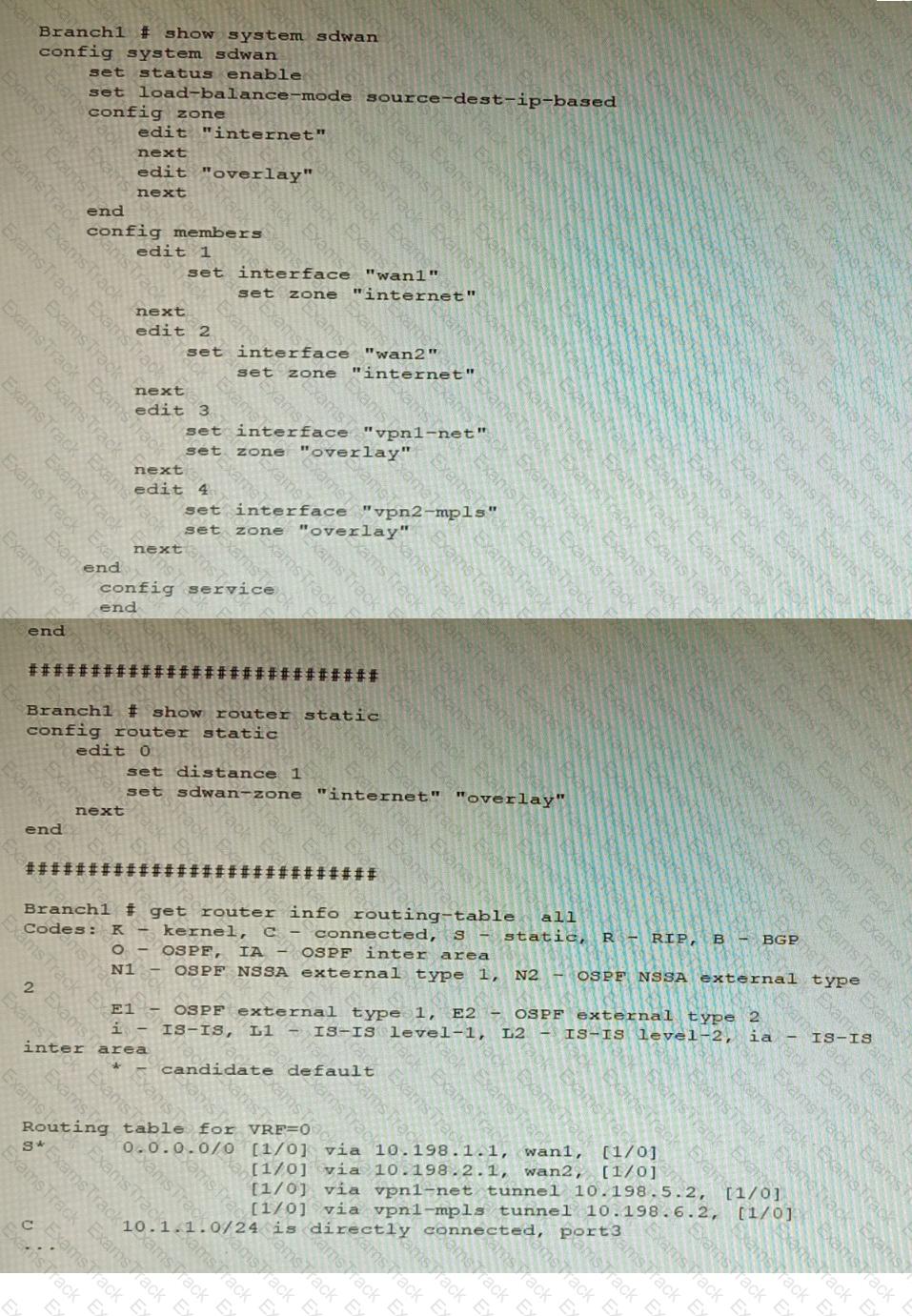
In the SD-WAN implicit rule, you do not want the traffic load balance for the overlay interface when all members are available.
In this scenario, which configuration change will meet this requirement?
Refer to the exhibits.
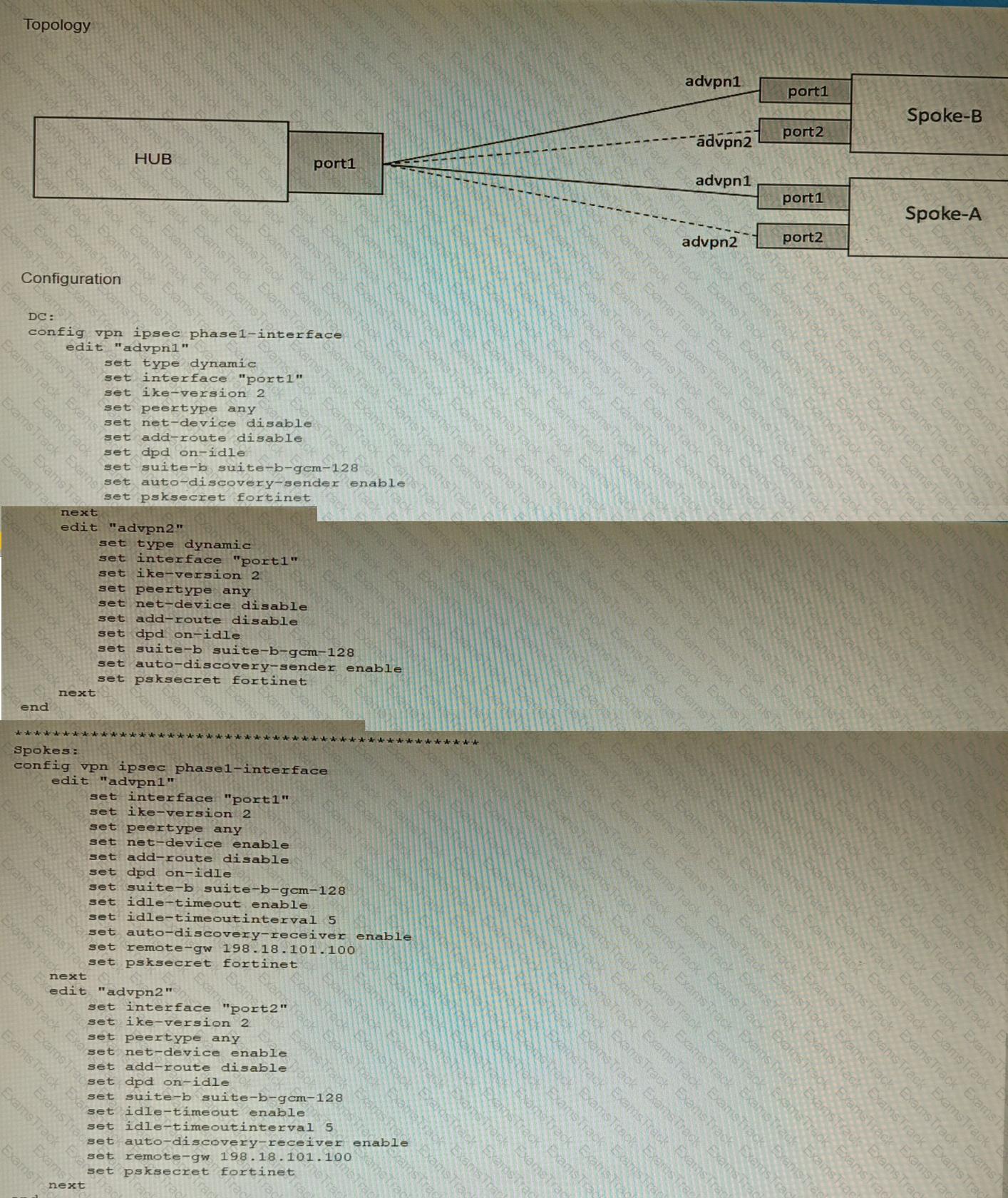
The exhibits show a diagram of a requested topology and the base IPsec configuration.
A customer asks you to configure ADVPN via two internet underlays. The requirement is that you use one interface with a single IP address on DC FortiGate.
In this scenario, which feature should be implemented to achieve this requirement?
An automation stitch was configured using an incoming webhook as the trigger named 'my_incoming_webhook'. The action is configured to execute the CLI Script shown:
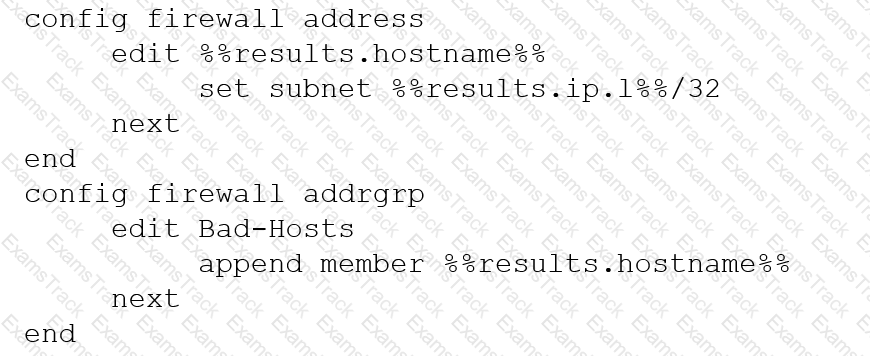
Refer to the exhibit of a FortiNAC configuration.

In this scenario, which two statements are correct? (Choose two.)
|
PDF + Testing Engine
|
|---|
|
$49.5 |
|
Testing Engine
|
|---|
|
$37.5 |
|
PDF (Q&A)
|
|---|
|
$31.5 |
Fortinet Free Exams |
|---|

|