Refer to the exhibit.
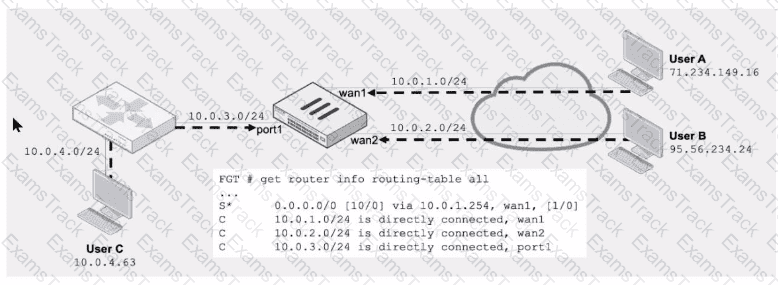
Assuming a default configuration, which three statements are true? (Choose three.)
Refer to the exhibit.
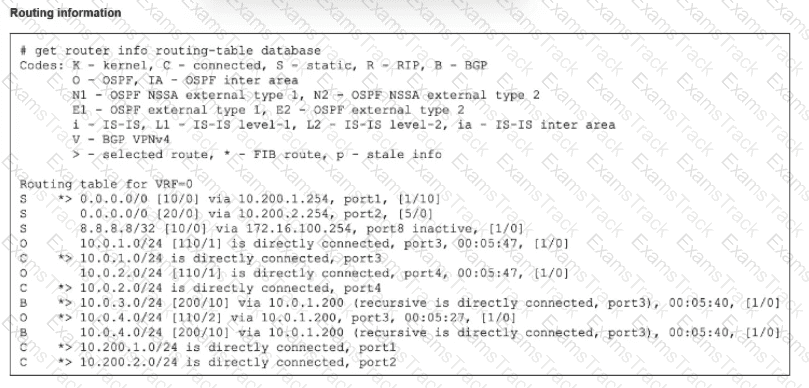
The modified output of live routing kemel is shown
Which two statements about the output are (rue? (Choose two.)
Refer to the exhibit, which shows the output of the command get router info ospf neighbor.
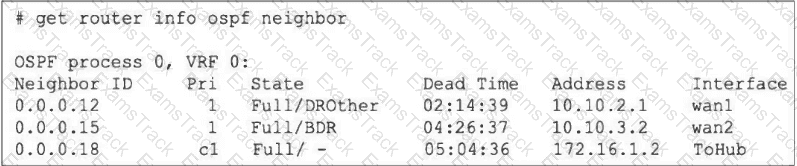
To what extent does FortiGate operate when looking at its OSPF neighbors? (Choose two.)
What is an accurate description of LDAP authentication using the regular bind type?
Refer to the exhibit.
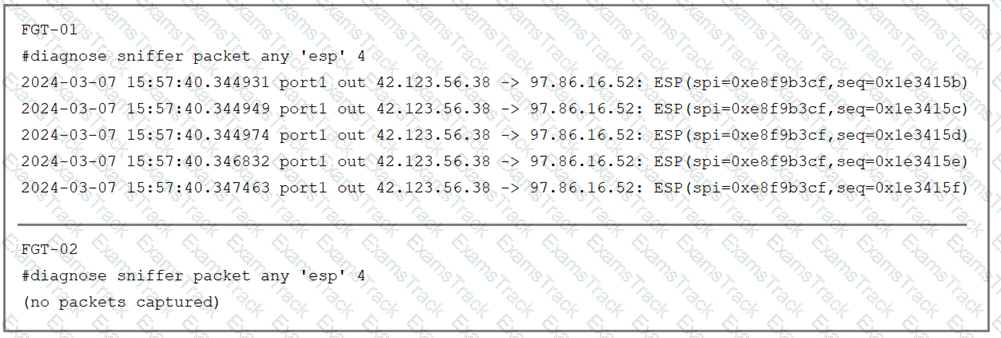
The sniffer log on two FortiGate devices are shown. Based on the information in the log, which two factors explain the output on FortiGate FGT-02? (Choose two answers)
Refer to the exhibit, which shows a truncated output of a real-time LDAP debug.
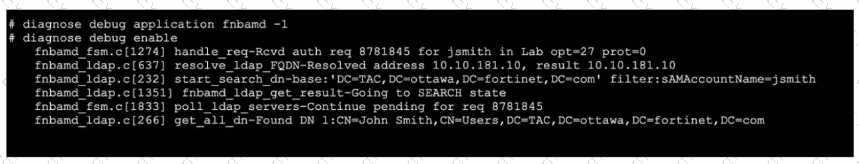
What two conclusions can you draw from the output? (Choose two.)
Refer to the exhibit, which contains the output of diagnose vpn tunnel list.
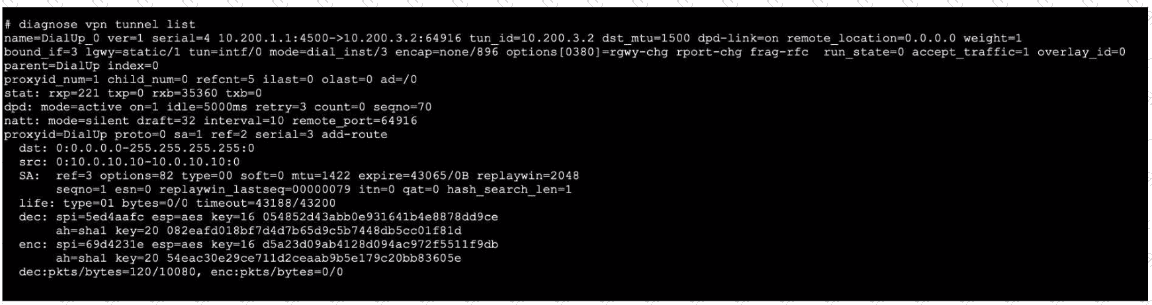
Which command will capture ESP traffic for the VPN named DialUp_0?
Refer to the exhibits.
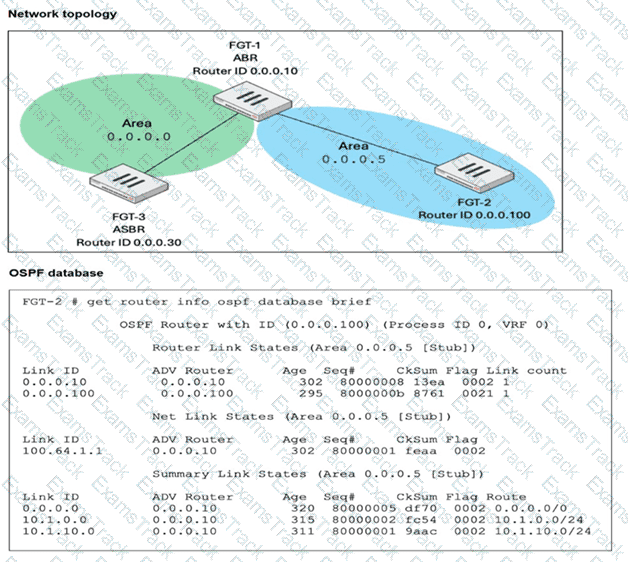
FGT-1 is an area border router (ABR) that has interfaces in OSPF areas 0.0.0.0 and 0.0.0.5. FGT-3 acts as an autonomous system border router (ASBR), importing static routes into OSPF. FGT-2 is an internal router with all its interfaces belonging to area 0.0.0.5. FGT-1 is receiving all advertised routes from FGT-2, however, FGT-3 is not receiving any of the advertised routes from FGT-1. What is the most likely reason for this? (Choose one answer)
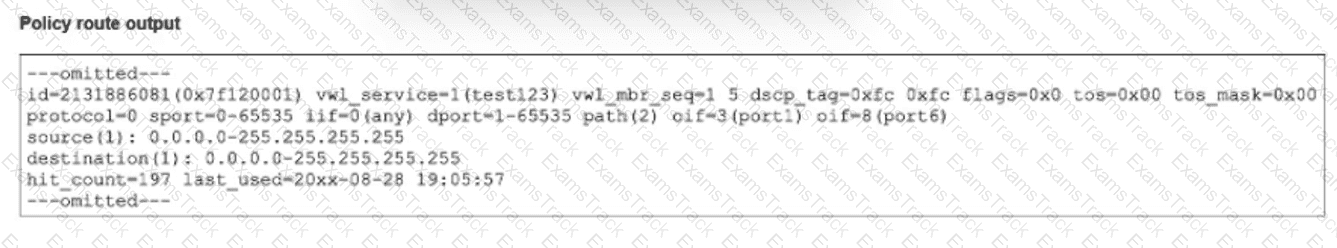
The output of a policy route table entry is shown.
Which type of policy route does the output show?
Refer to the exhibit, which shows the partial output of FortiOS kernel slabs.
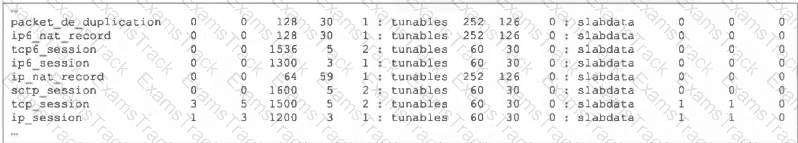
Which statement is true?
|
PDF + Testing Engine
|
|---|
|
$49.5 |
|
Testing Engine
|
|---|
|
$37.5 |
|
PDF (Q&A)
|
|---|
|
$31.5 |
Fortinet Free Exams |
|---|

|